Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: Azure Site Recovery Pricing Calculator for Azure to Azure Managed Disks 21 Febbraio 2025
- [Launched] Generally Available: Azure Site Recovery Pricing Calculator for Azure to Azure Managed Disks 21 Febbraio 2025
- [Launched] Generally Available: Azure Site Recovery Pricing Calculator for Azure to Azure Managed Disks 21 Febbraio 2025
- [Launched] Generally Available: Azure Site Recovery Pricing Calculator for Azure to Azure Managed Disks 21 Febbraio 2025
- [Launched] Generally Available: Azure Functions Support for Java 21 LTS 21 Febbraio 2025
- [Launched] Generally Available: Azure Functions Support for Java 21 LTS 21 Febbraio 2025
- [Launched] Generally Available: Azure Functions Support for Java 21 LTS 21 Febbraio 2025
- [Launched] Generally Available: Azure Functions Support for Java 21 LTS 21 Febbraio 2025
- [Launched] Generally Available: Azure Ultra Disk Storage is Now Available in New Zealand North 21 Febbraio 2025
- [Launched] Generally Available: Azure Ultra Disk Storage is Now Available in New Zealand North 21 Febbraio 2025

This week, teams across Microsoft Fabric and Microsoft Purview are gathered in Stockholm, Sweden, for the inaugural European Microsoft Fabric Community Conference. Attendees are in for an immersive experience with 130 sessions, 4 keynotes, 10 workshops, an expo hall, and a vibrant community lounge. The Microsoft Purview team[…]
Read MoreAs AI advances, we all have a role to play to unlock AI’s positive impact for organizations and communities around the world. That’s why we’re focused on helping customers use and build AI that is trustworthy, meaning AI that is secure, safe and private. At Microsoft, we have commitments to ensure Trustworthy AI[…]
Read More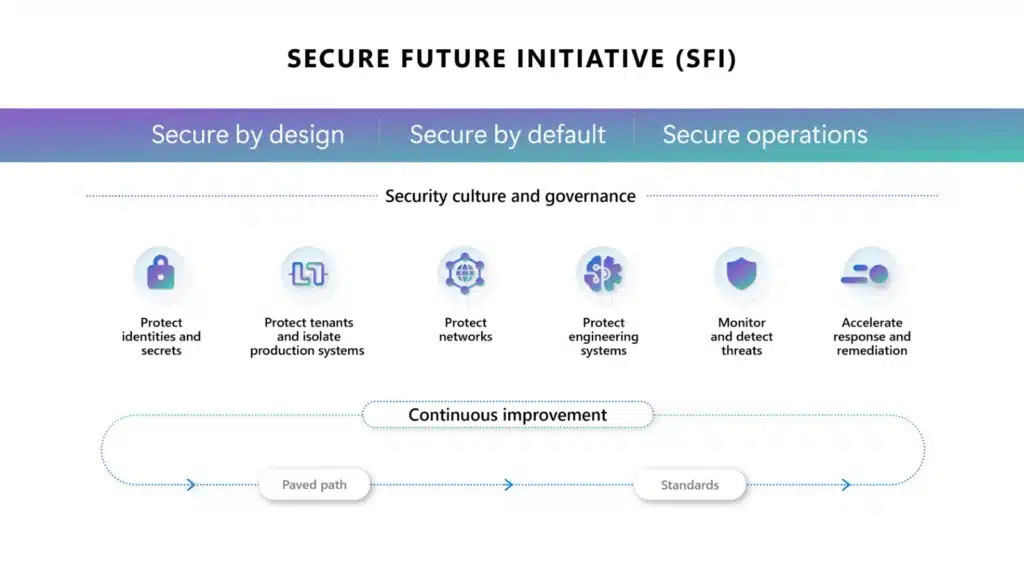
In November 2023, we introduced the Secure Future Initiative (SFI) to advance cybersecurity protection for Microsoft, our customers, and the industry. In May 2024, we expanded the initiative to focus on six key security pillars, incorporating industry feedback and our own insights. Since the initiative began, we’ve dedicated the[…]
Read More
For security professionals and teams, AI offers a significant advantage, empowering organizations of all sizes and industries to tip the scales in favor of defenders. It also introduces new uncertainties and risks that require organizations to create a culture of security to stay protected. Now, more than ever,[…]
Read More
We’re excited to welcome over 6,000 of our closest Microsoft Power Platform friends to the third annual Power Platform Community Conference (PPCC) at the MGM Grand in Las Vegas this week. The Power Platform Community Conference is all about you, the community, and we’re looking forward to spending[…]
Read More
Cybersecurity jobs are more challenging than ever. It’s not just increased speed, scale, and sophistication of cyberattacks that make cybersecurity jobs harder: there are 250 new regulatory updates to be tracked every day,1 cybersecurity teams have a disconnected collection of fragmented tools that they are expected to seamlessly[…]
Read More
At Microsoft, we understand that every organization is unique, and to get the most out of AI, you will want to customize it for your business’s specific needs and processes. Whether you’re a user, developer, or IT professional, Microsoft Copilot Studio offers a comprehensive platform for creating, managing,[…]
Read More
When building solutions in Microsoft Power Apps and Microsoft Power Automate, your organization may have company-specific needs and complex scenarios, such as custom mappings to various data sources, multi-faceted flows and triggers, and embedding various components with custom logic into apps. There is also repetitive work, such as[…]
Read More
My team and I spend our days developing technology that empowers everyone to build innovative solutions. We’ve seen the powerful combination of Copilot, AI, and low-code enable people from all sectors and professional backgrounds to transform their work and careers. The Microsoft Power Platform team believes that regardless of[…]
Read More
In today’s digital era, organizations need to maximize IT and business team efforts for process improvements and complex challenges. With cost and ROI in focus, Microsoft Power Platform offers low-code tools that enable efficient enterprise-grade solutions. To support investment decisions, Microsoft commissioned a 2024 Forrester Total Economic Impact™[…]
Read More