Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
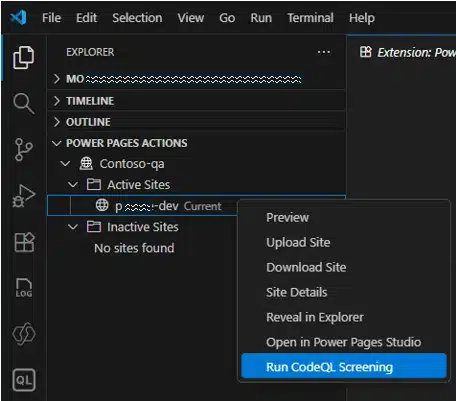
As web applications have become central to business operations, securing every line of custom code is more critical than ever. With the introduction of CodeQL scan in Power Pages toolset, we are empowering developers with static code analysis directly within their development workflow. Why CodeQL Security vulnerabilities can[…]
Read More
In today’s digital-first enterprise, identities have become the new corporate security perimeter. Hybrid work and cloud-first strategies have dissolved traditional network boundaries and dramatically increased the complexity of identity fabrics. Security teams are left managing a constellation of users, infrastructure, and tools scattered across hybrid environments or even[…]
Read More
The latest Microsoft Digital Defense Report 2025 paints a vivid picture of a cyberthreat landscape in flux. The surge in financially motivated cyberattacks and the persistent risk of nation-state actors demand urgent attention. But for those of us in the Office of the Chief Information Security Officer (CISO),[…]
Read More
On September 30, 2025, Microsoft announced a bold new vision for security: a unified, AI-powered platform designed to help organizations defend against today’s most sophisticated cyberthreats. But an equally important story—one that’s just beginning to unfold—is how the Microsoft Security Store is bringing this vision to life through[…]
Read More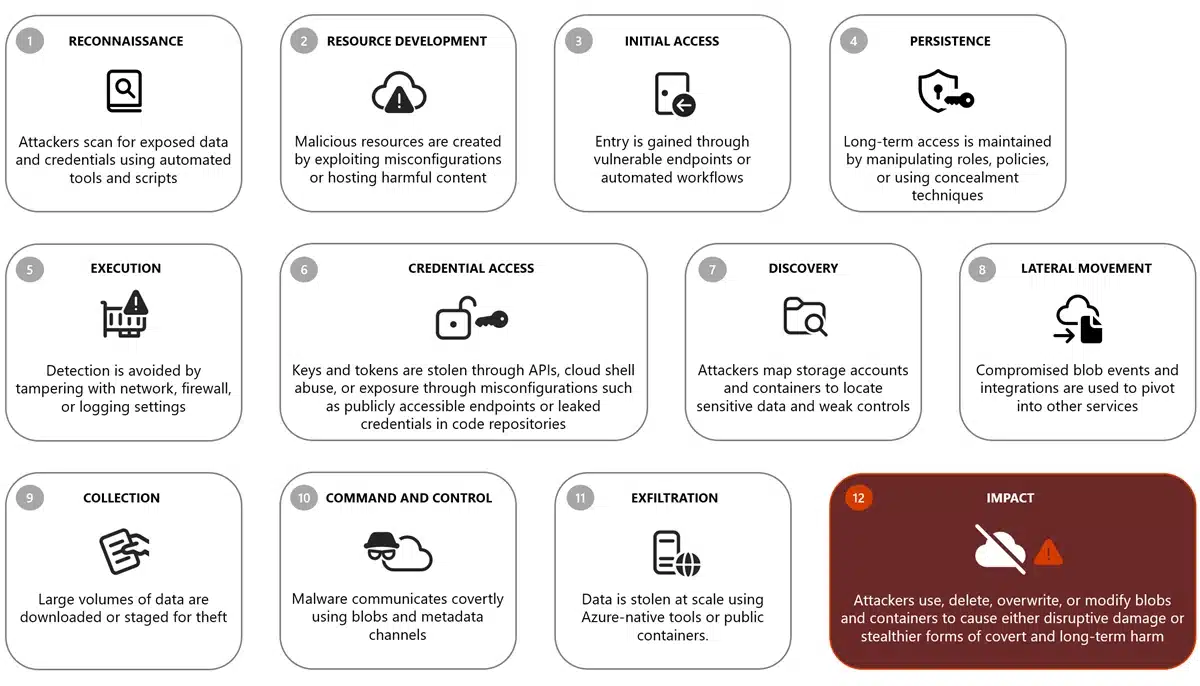
Azure Blob Storage, like any object data service, is a high-value target for threat actors due to its critical role in storing and managing massive amounts of unstructured data at scale across diverse workloads. Organizations of all sizes use Blob Storage to support key workloads—such as AI, high[…]
Read More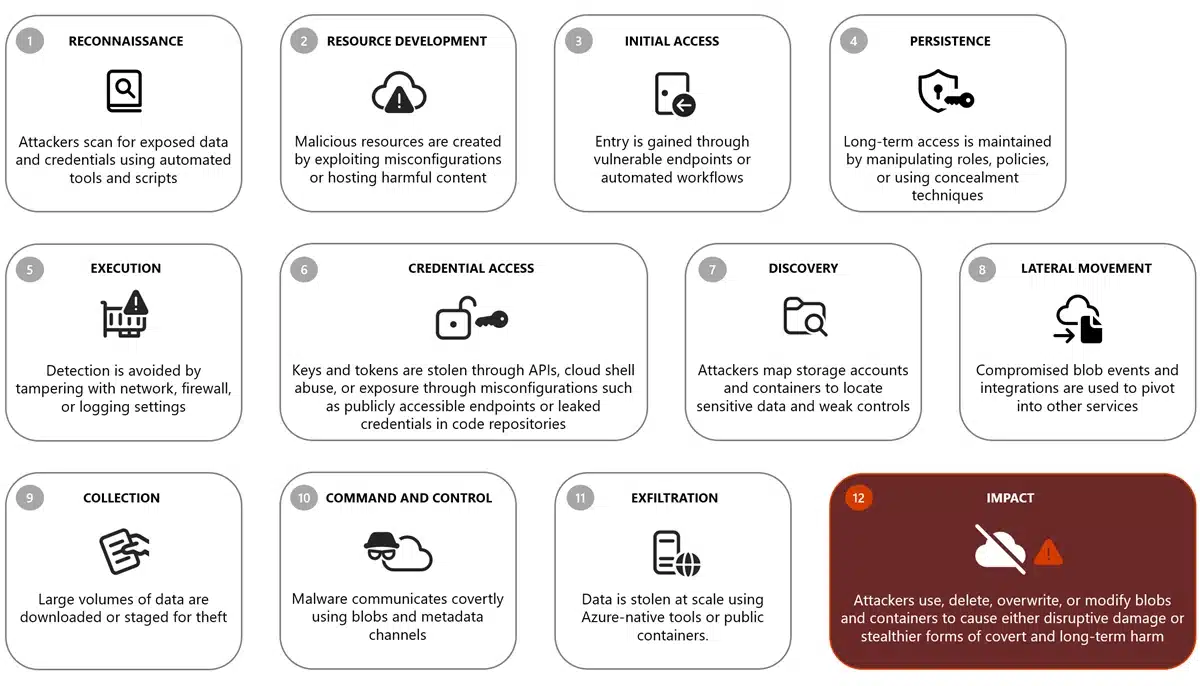
Azure Blob Storage, like any object data service, is a high-value target for threat actors due to its critical role in storing and managing massive amounts of unstructured data at scale across diverse workloads. Organizations of all sizes use Blob Storage to support key workloads—such as AI, high[…]
Read More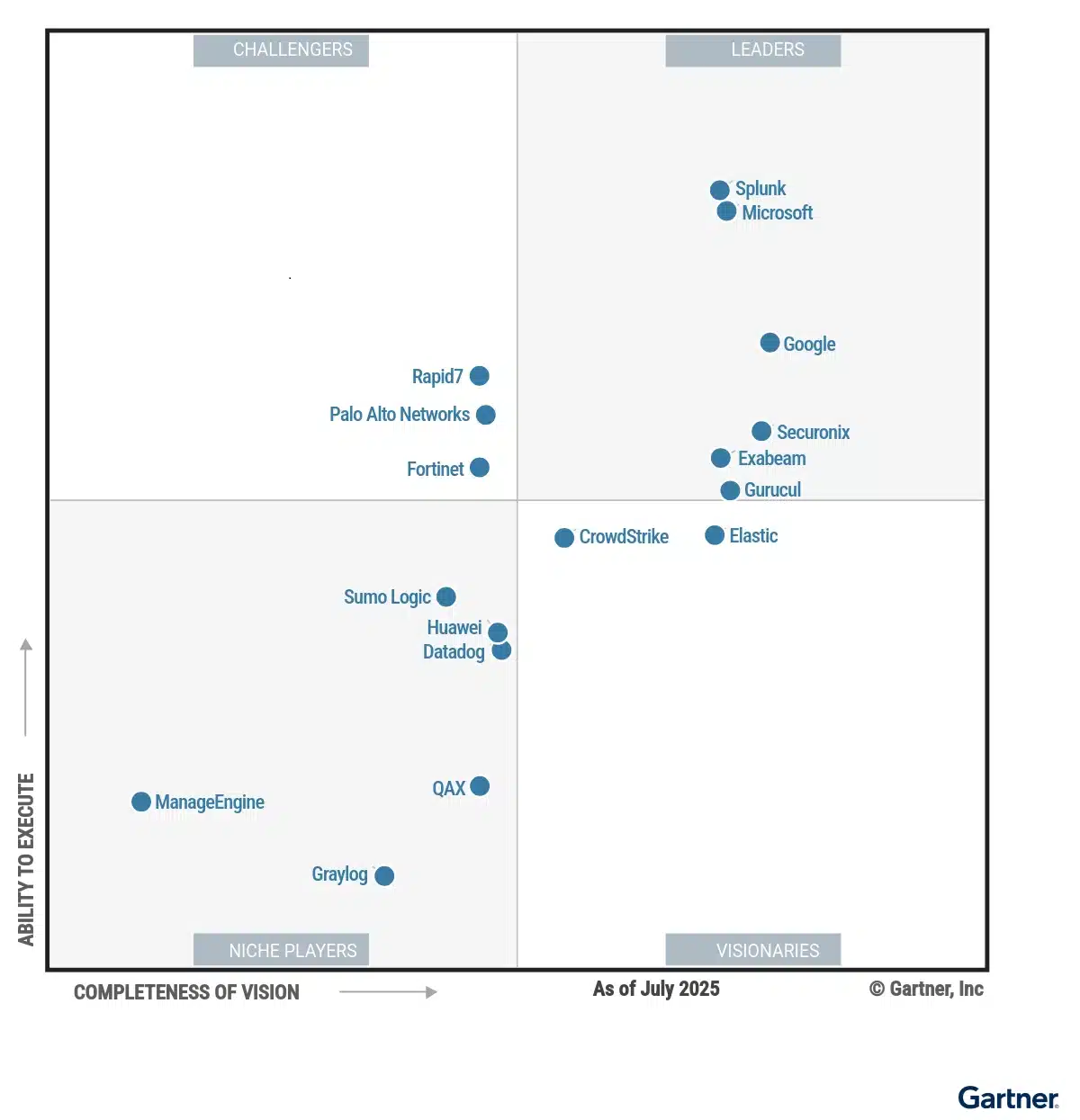
We’re honored to share that Microsoft has again been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for Security Information and Event Management (SIEM).1 We believe this recognition reinforces Microsoft Sentinel‘s position as an industry-leading, cloud and AI-powered SIEM—designed to solve SOC challenges head-on and streamline[…]
Read MoreIn 80% of the cyber incidents Microsoft’s security teams investigated last year, attackers sought to steal data—a trend driven more by financial gain than intelligence gathering. According to the latest Microsoft Digital Defense Report, written with our Chief Information Security Officer Igor Tsyganskiy, over half of cyberattacks with[…]
Read More
The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most important in their respective domains. In this series, you will get practical advice, tactics to start (and stop) deploying, forward-looking commentary on where the industry is going, and[…]
Read More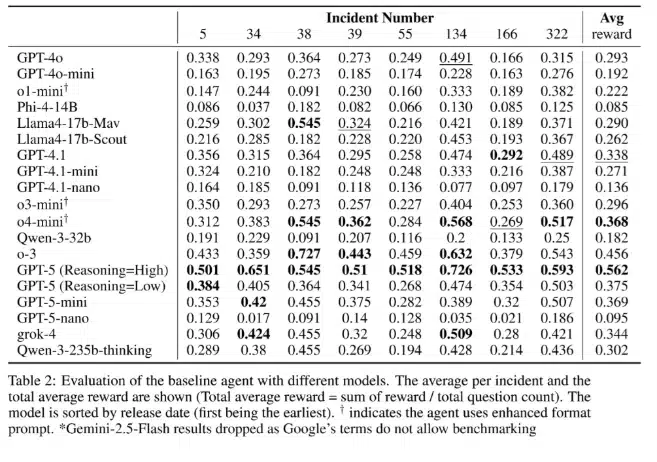
ExCyTIn-Bench is Microsoft’s newest open-source benchmarking tool designed to evaluate how well AI systems perform real-world cybersecurity investigations.1 It helps business leaders assess language models by simulating realistic cyberthreat scenarios and providing clear, actionable insights into how those tools reason through complex problems. In contrast to previous benchmarks[…]
Read More