Notizie per Categorie
Articoli Recenti
- Retirement: Announcing the 3-Year Retirement of Current Architecture for AKS on Windows Server 2019 and Windows Server 2022 29 Marzo 2025
- Retirement: Azure Intelligent Recommendation Service to Be Retired 29 Marzo 2025
- [Launched] Generally Availability: AzAcSnap 11 — Azure Application Consistent Snapshot Tool Updates 28 Marzo 2025
- Retirement: Azure Maps Traffic APIs Version 1.0 to Be Retired on March 31, 2028 28 Marzo 2025
- Retirement: Ubuntu 20.04 Node Pools in AKS 28 Marzo 2025
- Retirement: Azure SQL Database FSV2-Series Offer 28 Marzo 2025
- The future of manufacturing with Microsoft Dynamics 365 is here—are you ready? 28 Marzo 2025
- [Launched] Generally Available: Reminder – End of Limited Time Promotional Discounts on Azure Databricks Serverless Compute Services 28 Marzo 2025
- US Department of Labor’s journey to Zero Trust security with Microsoft Entra ID 27 Marzo 2025
- Beyond productivity: How industry-specific AI fuels growth 27 Marzo 2025
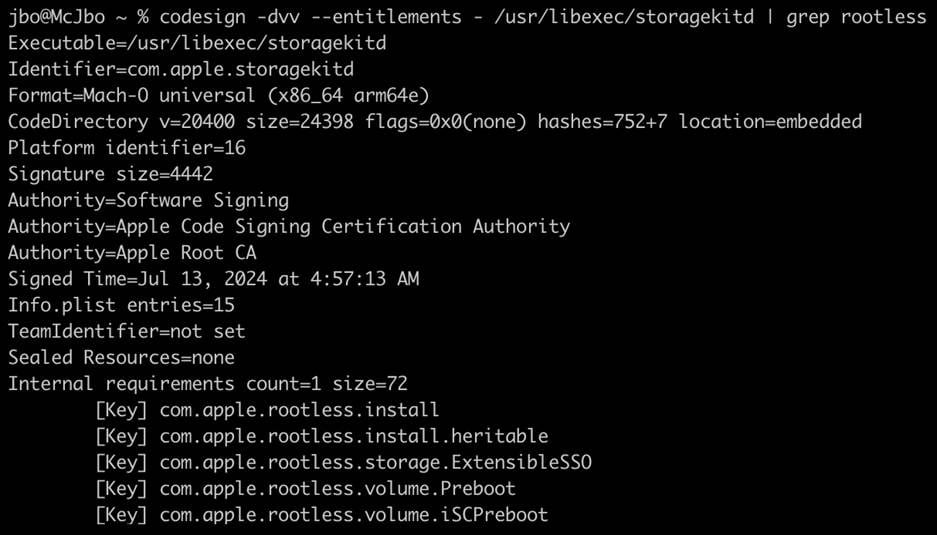
Microsoft Threat Intelligence discovered a new macOS vulnerability that could allow attackers to bypass Apple’s System Integrity Protection (SIP) in macOS by loading third party kernel extensions. SIP is a security technology that restricts the performance of operations that may compromise system integrity; thus, a SIP bypass affects[…]
Read More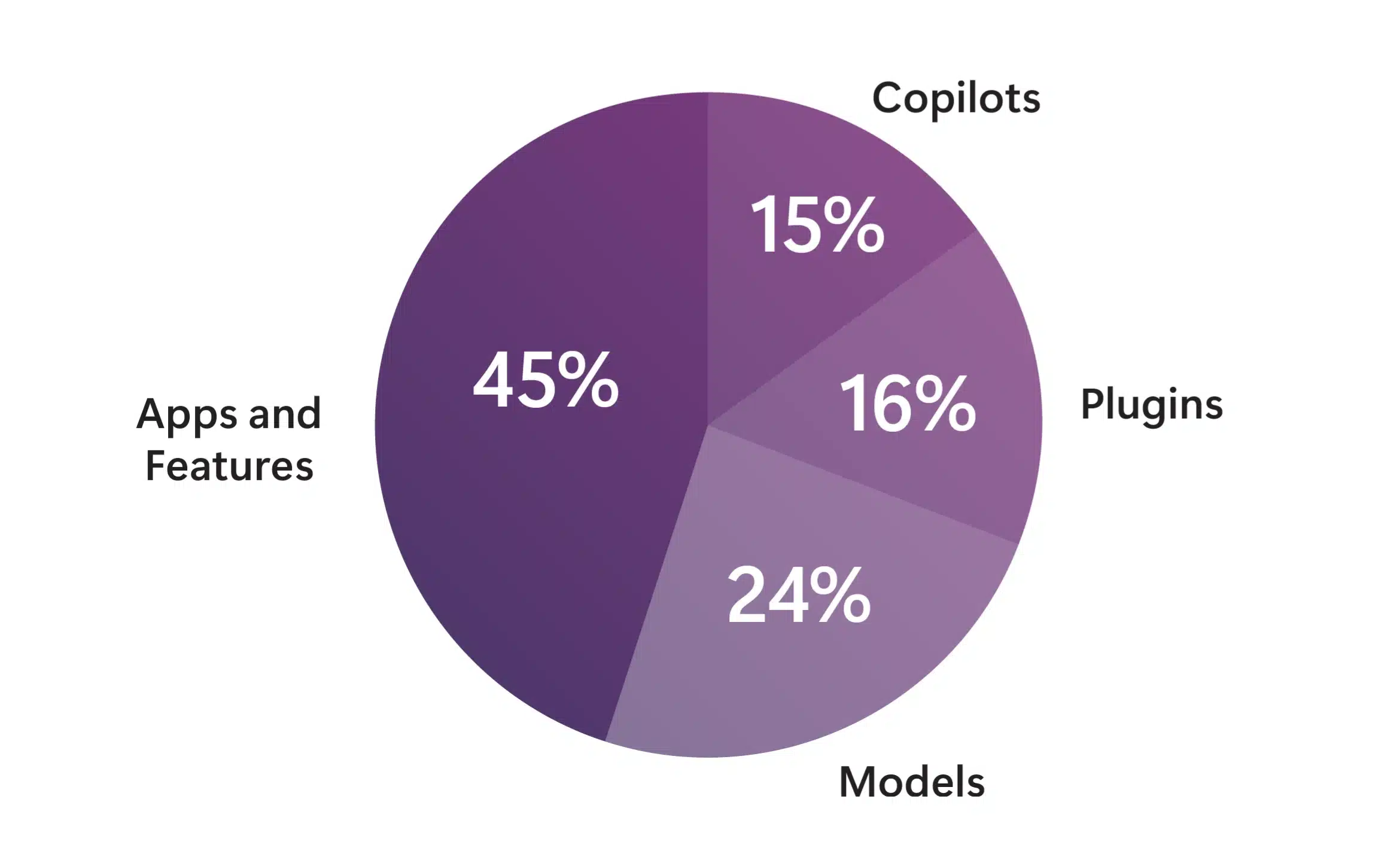
Microsoft’s AI red team is excited to share our whitepaper, “Lessons from Red Teaming 100 Generative AI Products.” The AI red team was formed in 2018 to address the growing landscape of AI safety and security risks. Since then, we have expanded the scope and scale of our[…]
Read More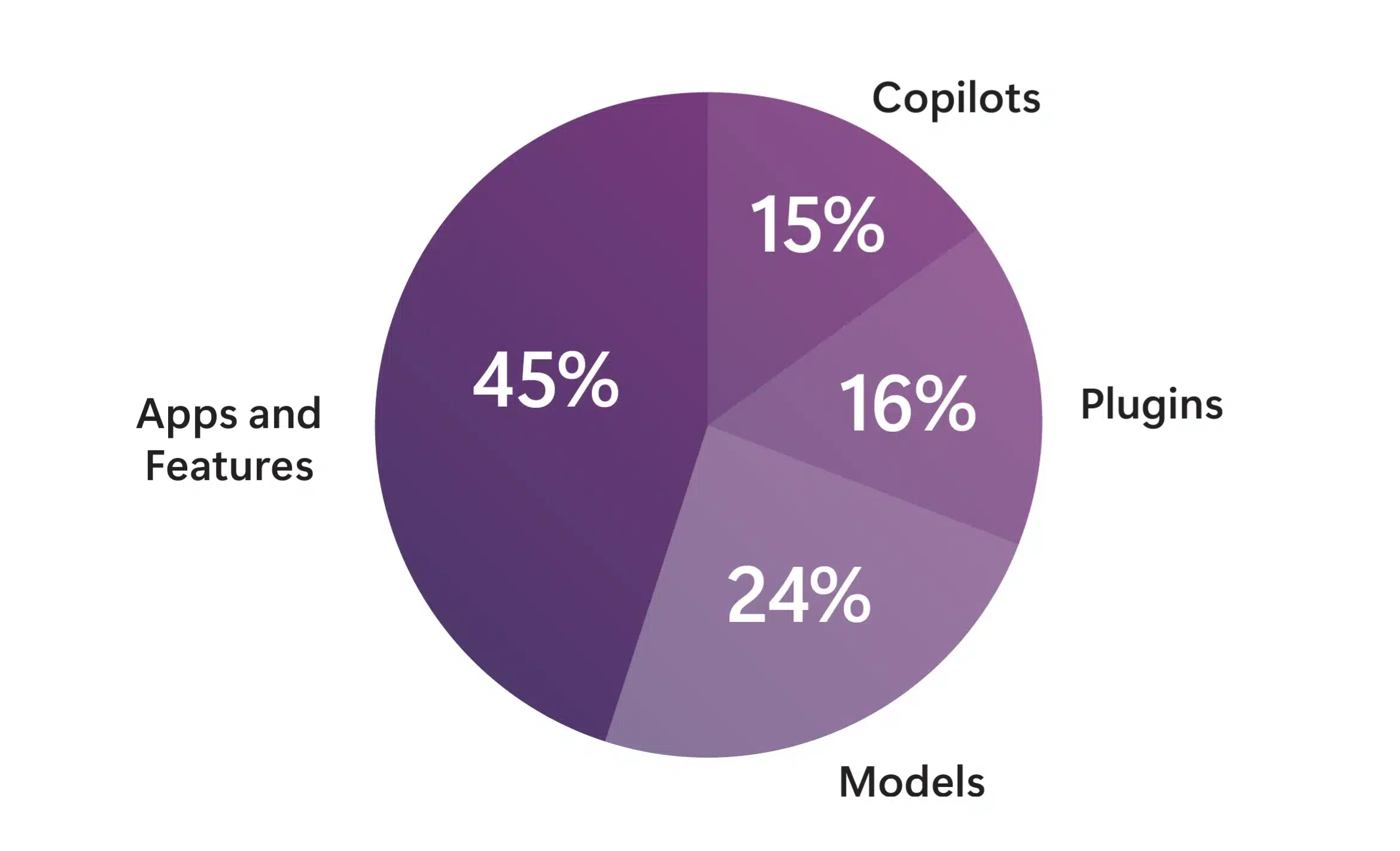
Microsoft’s AI red team is excited to share our whitepaper, “Lessons from Red Teaming 100 Generative AI Products.” The AI red team was formed in 2018 to address the growing landscape of AI safety and security risks. Since then, we have expanded the scope and scale of our[…]
Read More
The expanding attack surface is creating more opportunities for exploitation and adding to the pressure on security leaders and teams. Increasingly, organizations are investing in managed detection and response services (MDR) to bolster their security operations center (SOC) and meet the challenge. Demand is growing rapidly: according to[…]
Read More
The Cybersecurity Infrastructure Security Agency (CISA) Zero Trust Maturity Model (ZTMM) assists agencies in development of their Zero Trust strategies and continued evolution of their implementation plans. In April of 2024, we released Microsoft guidance for the Department of Defense Zero Trust Strategy. And now, we are excited[…]
Read More
Microsoft observes more than 600 million ransomware, phishing, and identity attacks each day.¹ One major theme from our analysis of these attacks is clear—organizations with integrated tools have better visibility and more holistic defense than those using a broader portfolio of point solutions. Microsoft wanted to test this observation[…]
Read More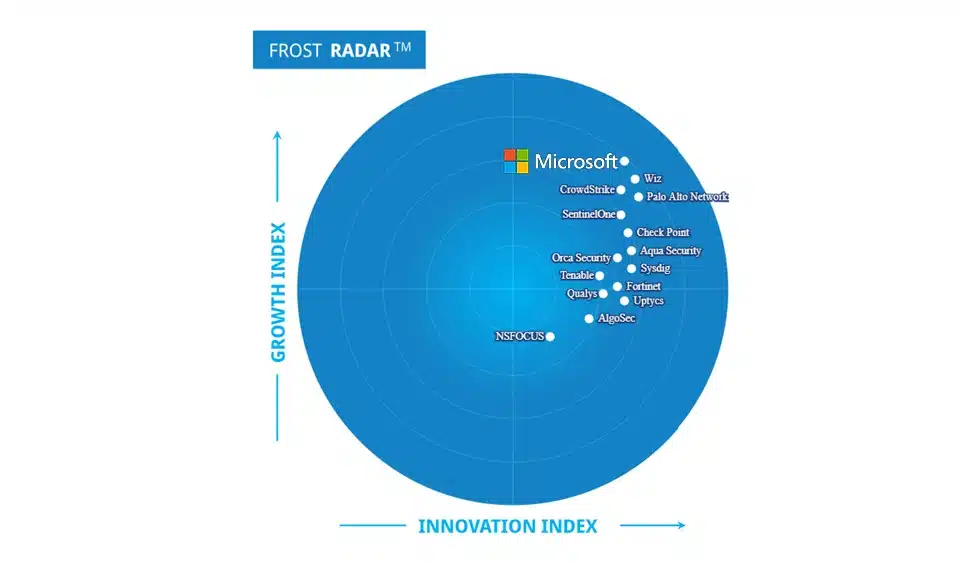
In the ever-evolving landscape of cloud security, Microsoft continues to assert its dominance with its comprehensive and innovative solutions. The Frost Radar™: Cloud-Native Application Protection Platforms, 2024 report underscores Microsoft’s leadership in both – the innovation and growth index, highlighting several key strengths that set it apart from[…]
Read More
Traditional security approaches don’t work for AI. Generative AI technology is already transforming our world and has immense positive potential for cybersecurity and business processes, but traditional security models and controls aren’t enough to manage the security risks associated with this new technology. We recently published a new[…]
Read More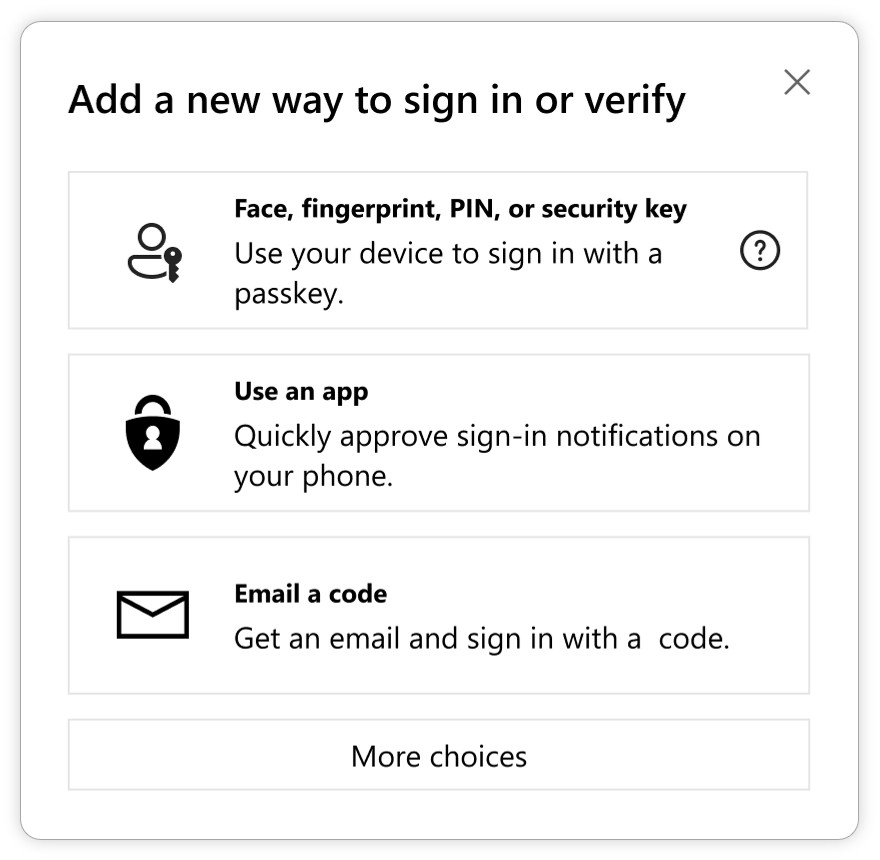
There’s no doubt about it: The password era is ending. Bad actors know it, which is why they’re desperately accelerating password-related attacks while they still can. At Microsoft, we block 7,000 attacks on passwords per second—almost double from a year ago. At the same time, we’ve seen adversary-in-the-middle[…]
Read More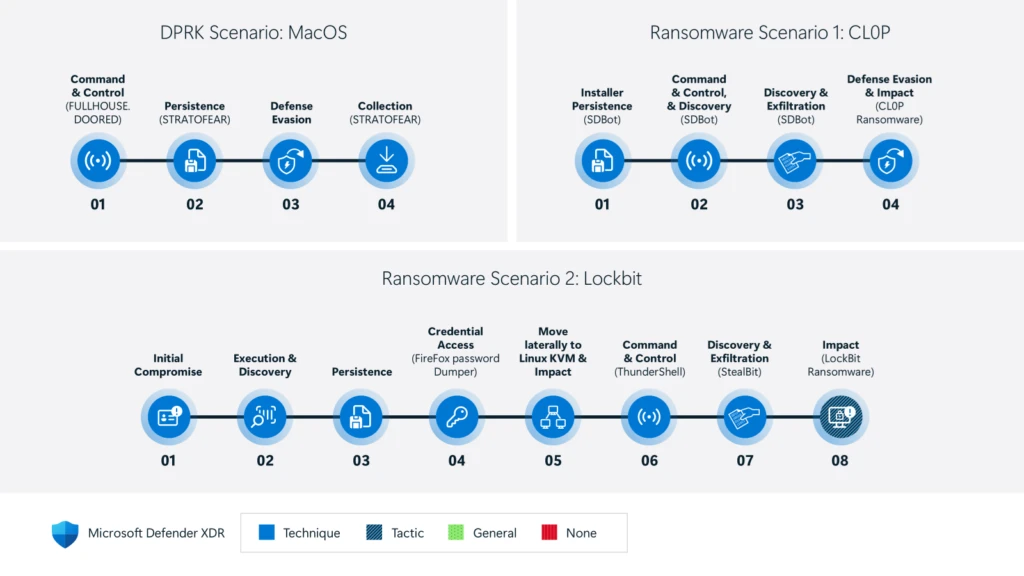
Delivering industry-leading detection for a sixth consecutive year For the sixth year in a row, Microsoft Defender XDR demonstrated industry-leading extended detection and response (XDR) capabilities in the independent MITRE ATT&CK® Evaluations: Enterprise. The cyberattack used during the detection test highlights the importance of a unified XDR platform[…]
Read More