Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
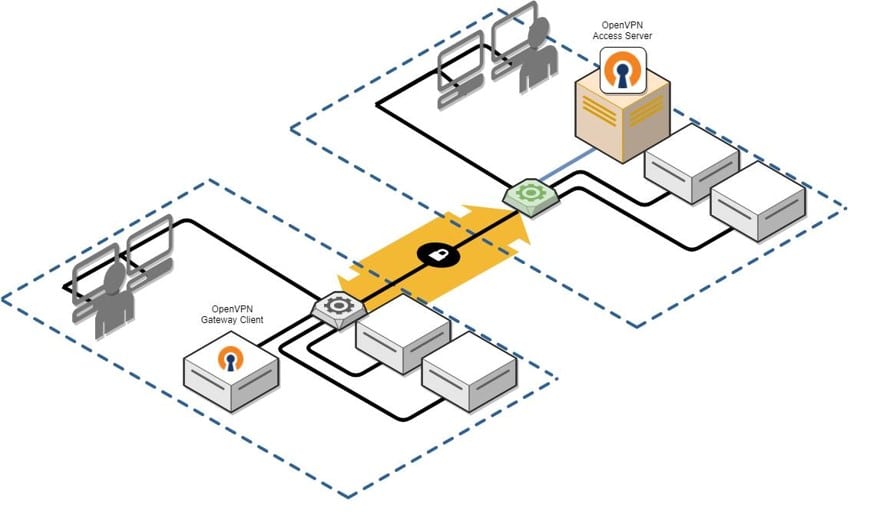
Microsoft researchers recently identified multiple medium severity vulnerabilities in OpenVPN, an open-source project with binaries integrated into routers, firmware, PCs, mobile devices, and many other smart devices worldwide, numbering in the millions. Attackers could chain and remotely exploit some of the discovered vulnerabilities to achieve an attack chain[…]
Read More
We are announcing the release of the recently published Zero Trust practice guide in collaboration between Microsoft and the National Cybersecurity Center of Excellence (NCCoE). This guide details how to implement a Zero Trust strategy, and what an end to end security approach using Zero Trust means for you[…]
Read More
AI is driving unprecedented opportunities for businesses. With advancements in AI and low-code development platforms, organizations are finding new ways to accelerate their growth and efficiency. And it couldn’t come at a better time, because technology has a talent problem. There’s just not enough high-tech talent in the[…]
Read More
The era of AI brings many opportunities to companies, from boosts in productivity to generative AI applications and more. As humans continue to harness the power of machine learning, these AI innovations are poised to have an enormous impact on organizations, industries, and society at large. A recent[…]
Read More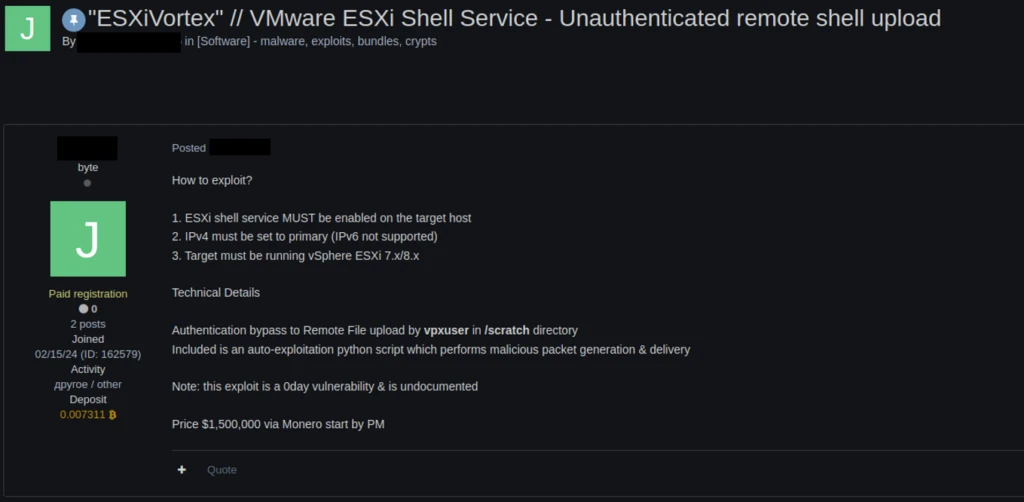
Microsoft researchers have uncovered a vulnerability in ESXi hypervisors being exploited by several ransomware operators to obtain full administrative permissions on domain-joined ESXi hypervisors. ESXi is a bare-metal hypervisor that is installed directly onto a physical server and provides direct access and control of underlying resources. ESXi hypervisors[…]
Read More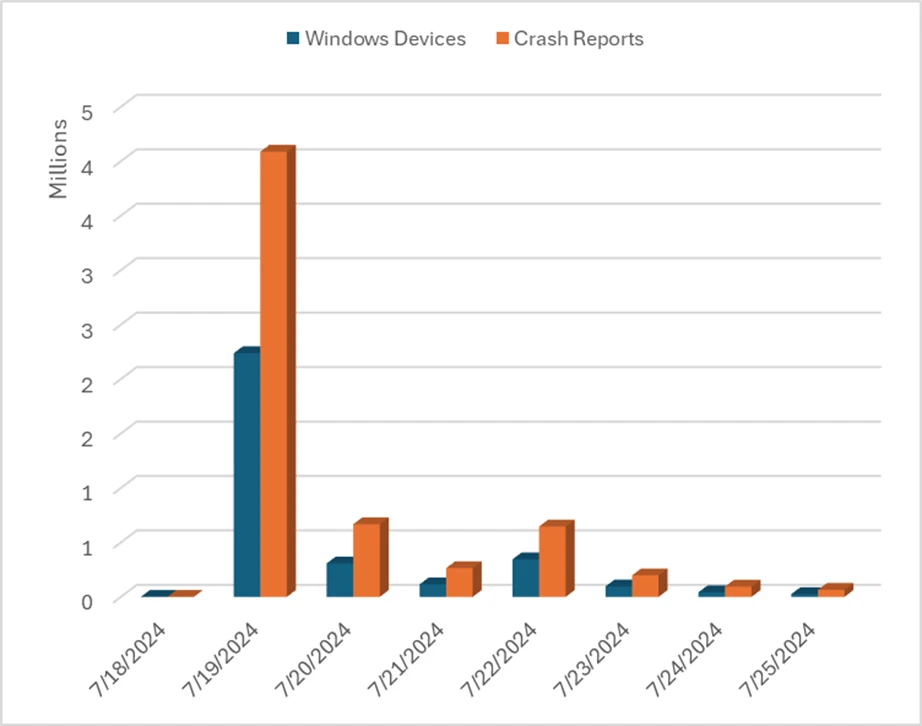
Windows is an open and flexible platform used by many of the world’s top businesses for high availability use cases where security and availability are non-negotiable. To meet those needs: Windows provides a range of operating modes that customers can choose from. This includes the ability to limit[…]
Read More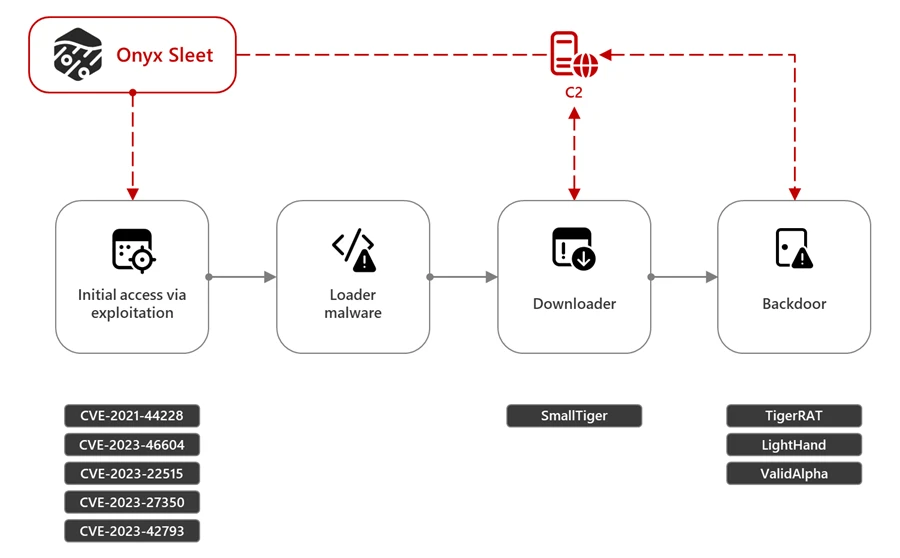
On July 25, 2024, the United States Department of Justice (DOJ) indicted an individual linked to the North Korean threat actor that Microsoft tracks as Onyx Sleet. Microsoft Threat Intelligence collaborated with the Federal Bureau of Investigation (FBI) in tracking activity associated with Onyx Sleet. We will continue[…]
Read More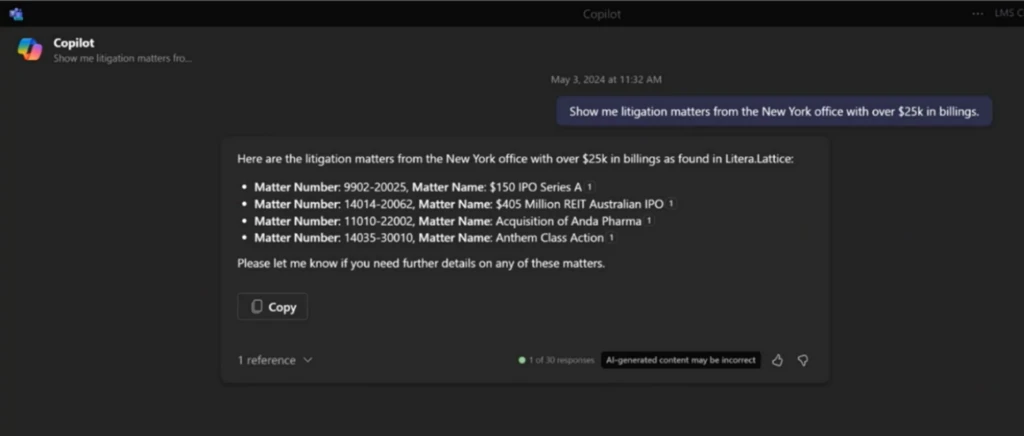
As Microsoft Copilot becomes an integral part of an organization’s business processes, it is essential to enhance Copilot AI capabilities to include skills and knowledge that are unique to that process. Using Copilot connectors in Microsoft Copilot Studio, organizations can create, extend, enrich, and customize Copilot with knowledge[…]
Read More
Cybercrime never sleeps and the threat actors behind it never stop evolving their tactics—including using AI to automate cyberattacks, create deep fakes, and complete other nefarious tasks. According to Statista’s Market Insights, the estimated global cost of online criminal acts is expected to surge to $23.84 trillion by 2027, up[…]
Read More
Black Hat USA 2024 is packed with timely, relevant information for today’s security professionals. During the conference this August, we’ll share our deep expertise in AI-first end-to-end security and extensive threat intelligence research. Join us as we present our main stage speaker Ann Johnson, Corporate Vice President and[…]
Read More