Notizie per Categorie
Articoli Recenti
- Retirement: Announcing the 3-Year Retirement of Current Architecture for AKS on Windows Server 2019 and Windows Server 2022 29 Marzo 2025
- Retirement: Azure Intelligent Recommendation Service to Be Retired 29 Marzo 2025
- [Launched] Generally Availability: AzAcSnap 11 — Azure Application Consistent Snapshot Tool Updates 28 Marzo 2025
- Retirement: Azure Maps Traffic APIs Version 1.0 to Be Retired on March 31, 2028 28 Marzo 2025
- Retirement: Ubuntu 20.04 Node Pools in AKS 28 Marzo 2025
- Retirement: Azure SQL Database FSV2-Series Offer 28 Marzo 2025
- The future of manufacturing with Microsoft Dynamics 365 is here—are you ready? 28 Marzo 2025
- [Launched] Generally Available: Reminder – End of Limited Time Promotional Discounts on Azure Databricks Serverless Compute Services 28 Marzo 2025
- US Department of Labor’s journey to Zero Trust security with Microsoft Entra ID 27 Marzo 2025
- Beyond productivity: How industry-specific AI fuels growth 27 Marzo 2025

In today’s interconnected world, there’s virtually no limit to what technology can help us achieve. Millions of connections happen every moment between people, machines, apps, and devices. Digital connectivity fuels new possibilities for us in business, helps us make positive changes in the way we live and work,[…]
Read More
The security community is continuously changing, growing, and learning from each other to better position the world against cyberthreats. In the latest post of our Community Voices blog series, Microsoft Security Senior Product Marketing Manager Brooke Lynn Weenig talks with Matt Suiche, Director of Research and Development for Memory Analysis and Incident Response for Magnet Forensics. The thoughts below reflect[…]
Read More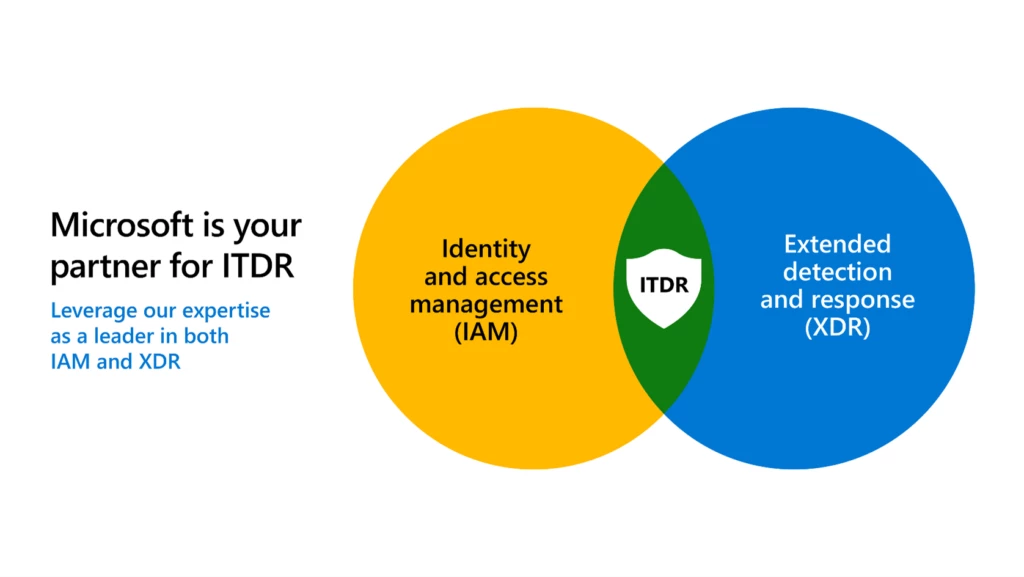
Identity has become the corporate security perimeter. The average organization used 130 different cloud applications in 2022. That’s up 18 percent from 2021 alone.1 And as organizations continue to embrace digital transformation and enable remote work, they look to identity and access management solutions to ensure that the[…]
Read More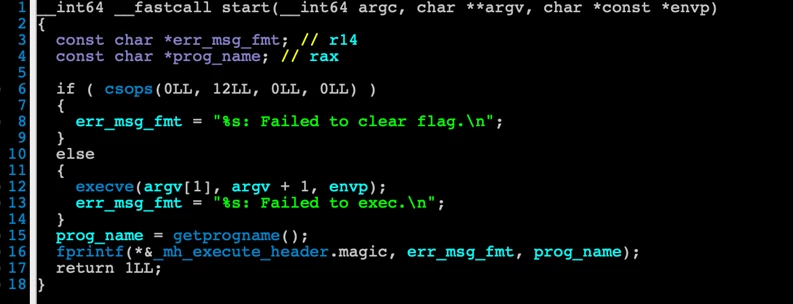
A new vulnerability, which we refer to as “Migraine” for its involvement with macOS migration, could allow an attacker with root access to automatically bypass System Integrity Protection (SIP) in macOS and perform arbitrary operations on a device. We shared these findings with Apple through Coordinated Vulnerability Disclosure[…]
Read More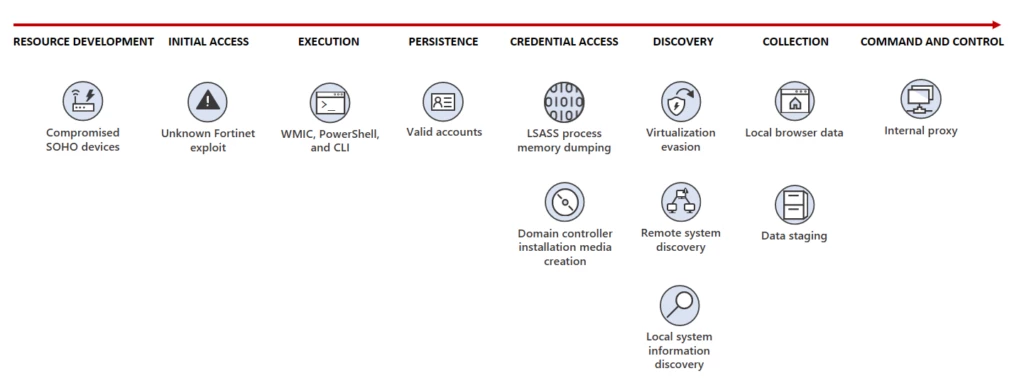
Microsoft has uncovered stealthy and targeted malicious activity focused on post-compromise credential access and network system discovery aimed at critical infrastructure organizations in the United States. The attack is carried out by Volt Typhoon, a state-sponsored actor based in China that typically focuses on espionage and information gathering.[…]
Read More
At Microsoft Build 2023—an event for developers by developers—we’re going to announce exciting new features and technologies, share ideas, and help everyone boost their skills so we can all build a more secure future together. This year’s Microsoft Build offers a full program, both online and in-person, to[…]
Read More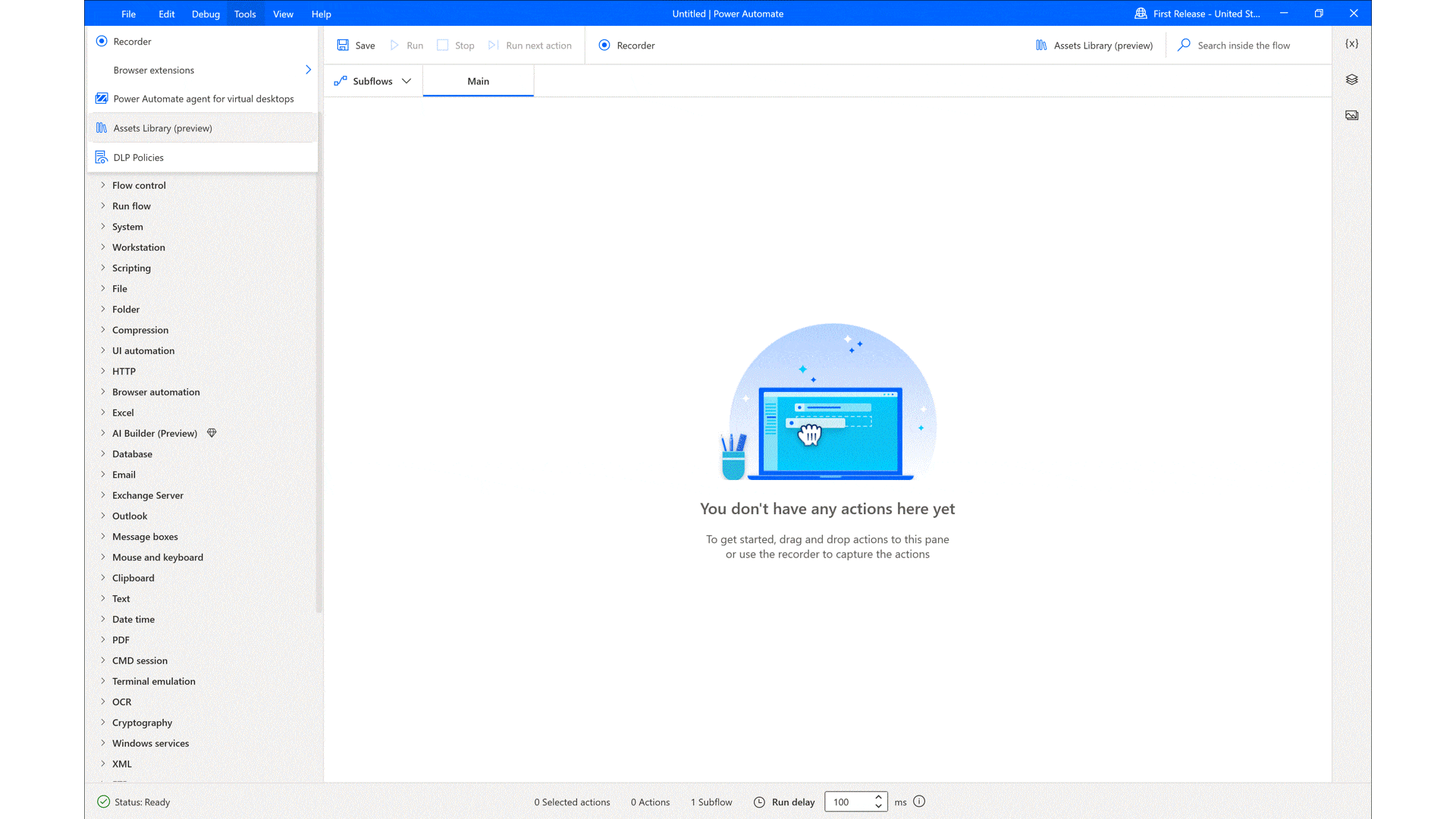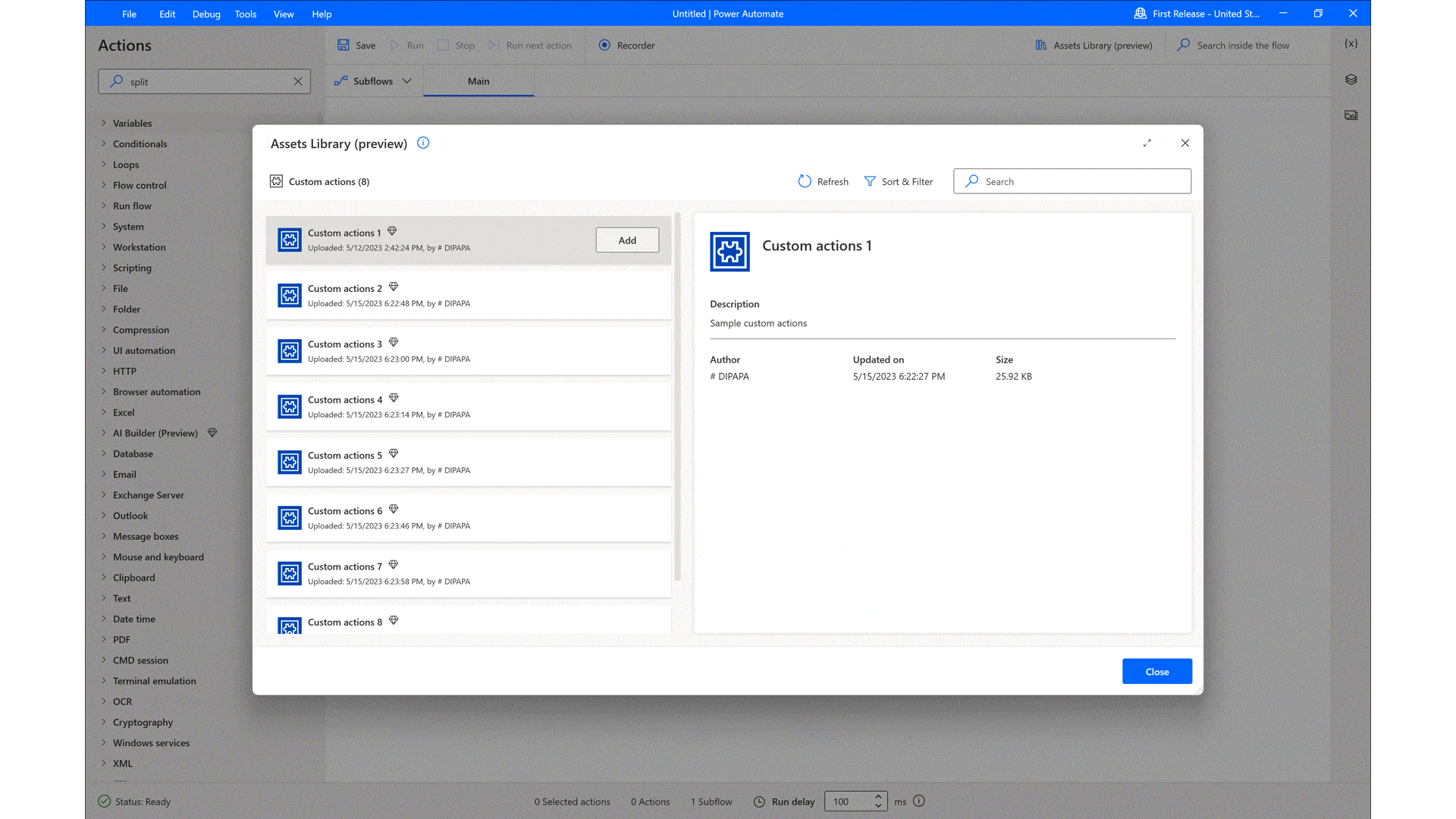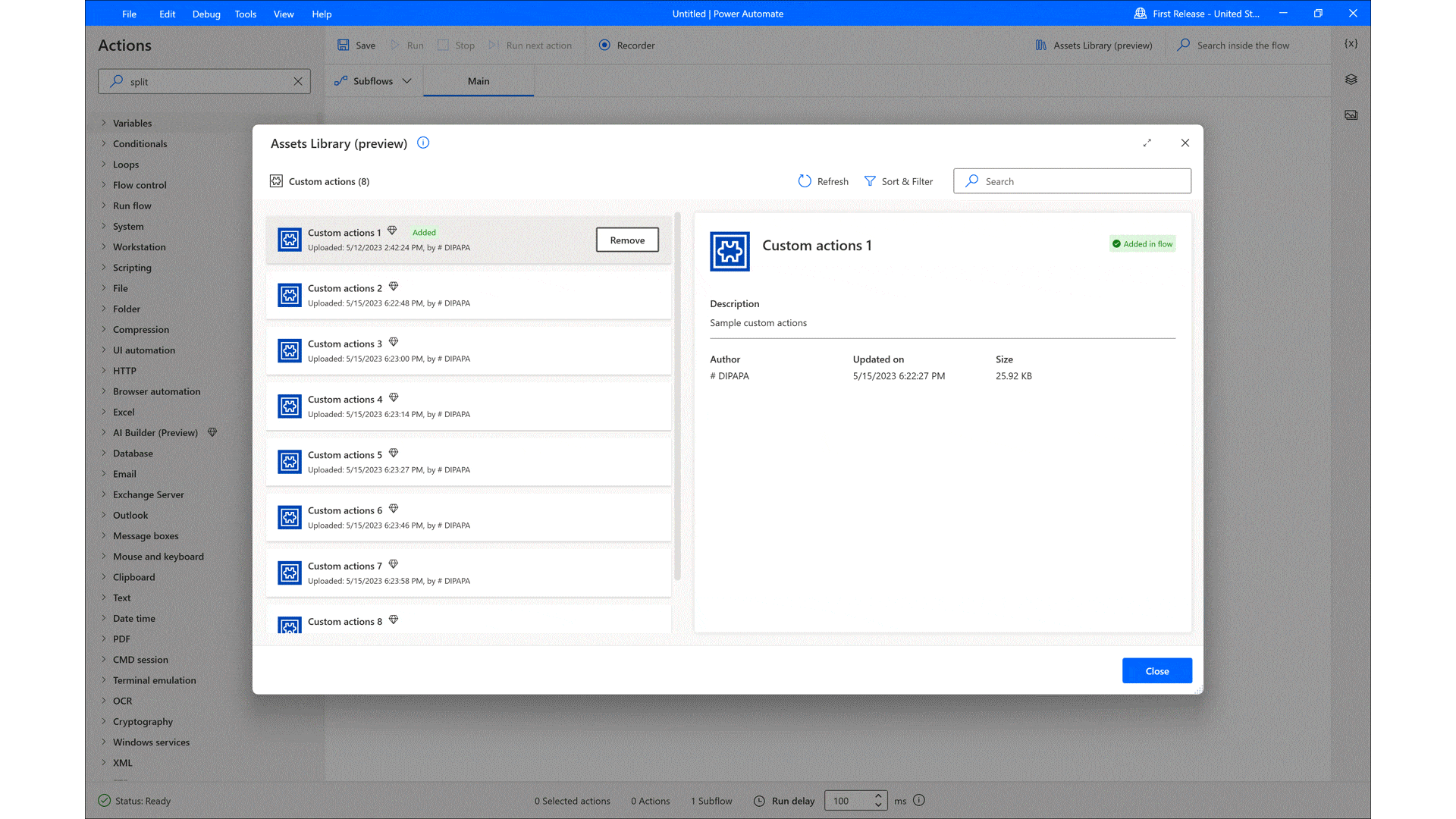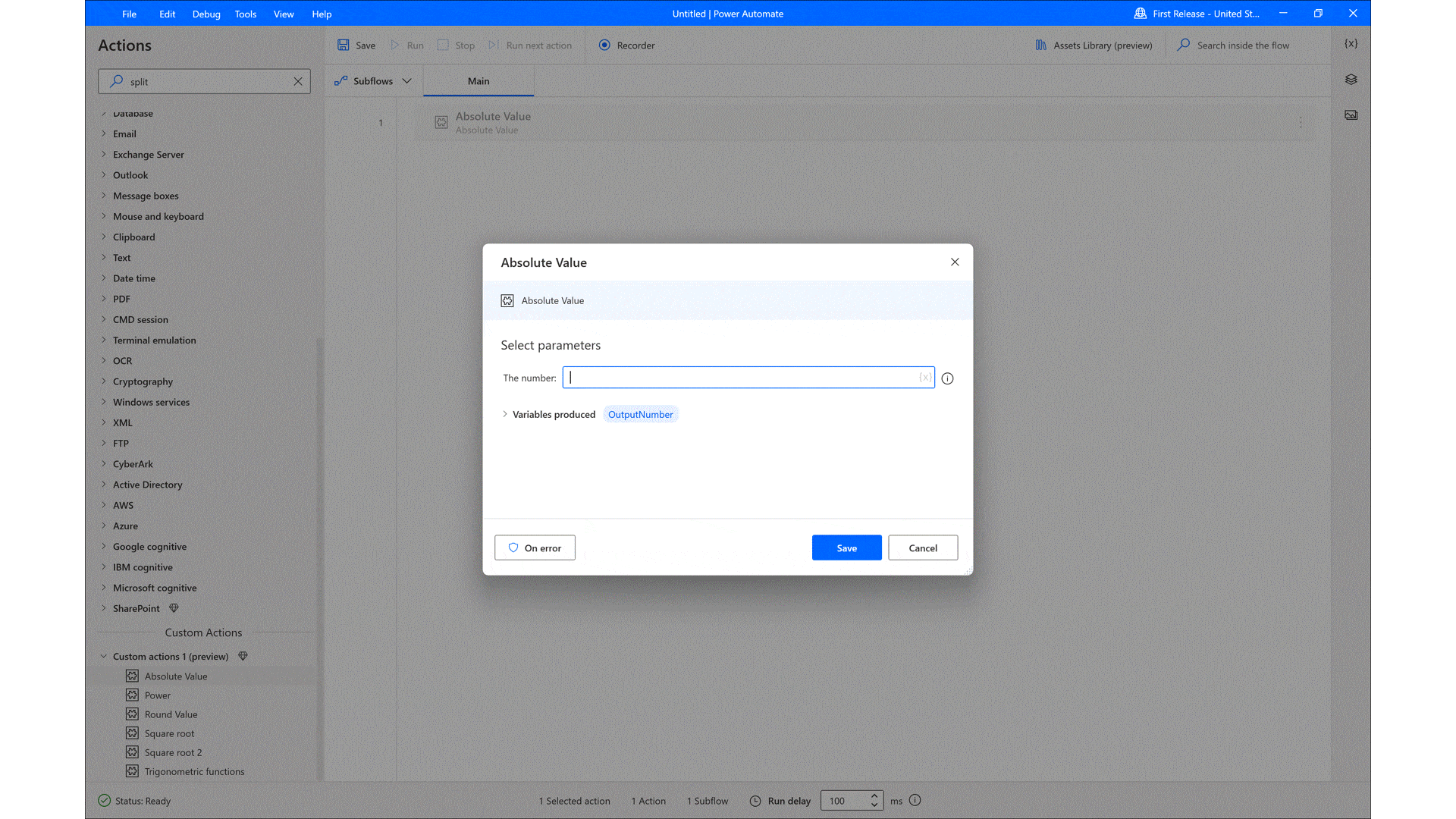
According to Gartner, “By 2026, low-code development tools will account for 75 percent of new application development.”1 To help build those applications, professional developers are turning to Microsoft Power Platform. Microsoft Power Platform transforms the way developers work by providing a comprehensive low-code platform that increases their productivity and[…]
Read More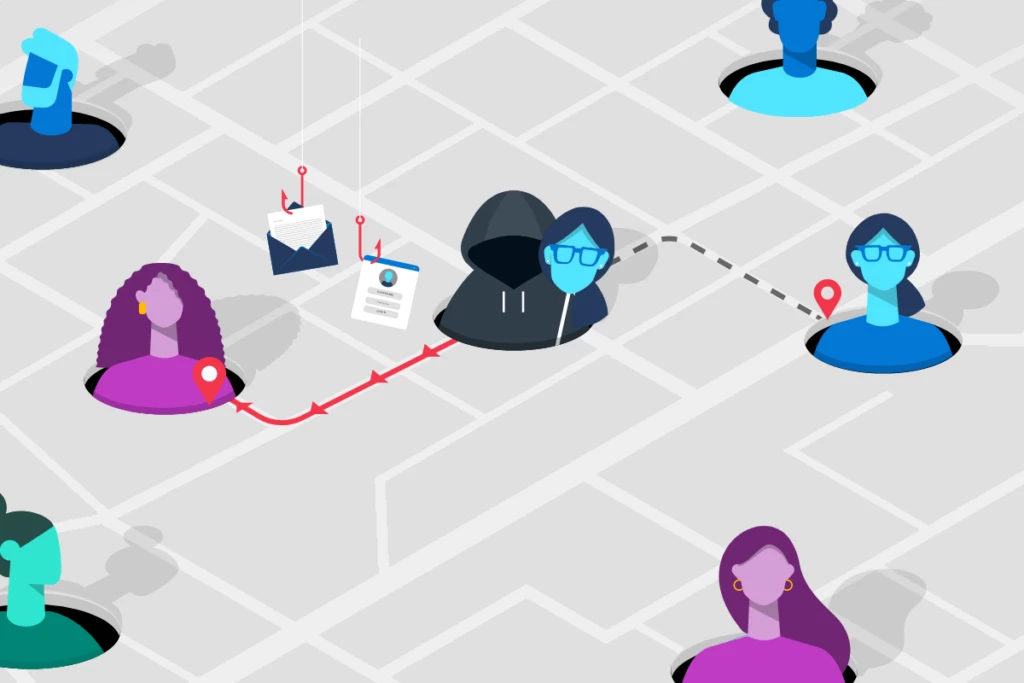
Today we released the fourth edition of Cyber Signals highlighting a surge in cybercriminal activity around business email compromise (BEC). Microsoft has observed a 38 percent increase in cybercrime as a service (CaaS) targeting business email between 2019 and 2022.1 Successful BEC attacks cost organizations hundreds of millions[…]
Read More
The RSA Conference (RSAC) gave us an incredible opportunity to meet with security professionals from around the world, learn about exciting advances in the world of cybersecurity, and share our own security innovations. Defenders everywhere serve an important mission of protecting our world, and RSAC is a special[…]
Read MoreThe post How Copilot in Microsoft Dynamics 365 and Power Platform delivers enterprise-ready AI built for security and privacy appeared first on Microsoft Power Platform Blog. Source: Microsoft Power Platform
Read More