Notizie per Categorie
Articoli Recenti
- Retirement: Announcing the 3-Year Retirement of Current Architecture for AKS on Windows Server 2019 and Windows Server 2022 29 Marzo 2025
- Retirement: Azure Intelligent Recommendation Service to Be Retired 29 Marzo 2025
- [Launched] Generally Availability: AzAcSnap 11 — Azure Application Consistent Snapshot Tool Updates 28 Marzo 2025
- Retirement: Azure Maps Traffic APIs Version 1.0 to Be Retired on March 31, 2028 28 Marzo 2025
- Retirement: Ubuntu 20.04 Node Pools in AKS 28 Marzo 2025
- Retirement: Azure SQL Database FSV2-Series Offer 28 Marzo 2025
- The future of manufacturing with Microsoft Dynamics 365 is here—are you ready? 28 Marzo 2025
- [Launched] Generally Available: Reminder – End of Limited Time Promotional Discounts on Azure Databricks Serverless Compute Services 28 Marzo 2025
- US Department of Labor’s journey to Zero Trust security with Microsoft Entra ID 27 Marzo 2025
- Beyond productivity: How industry-specific AI fuels growth 27 Marzo 2025
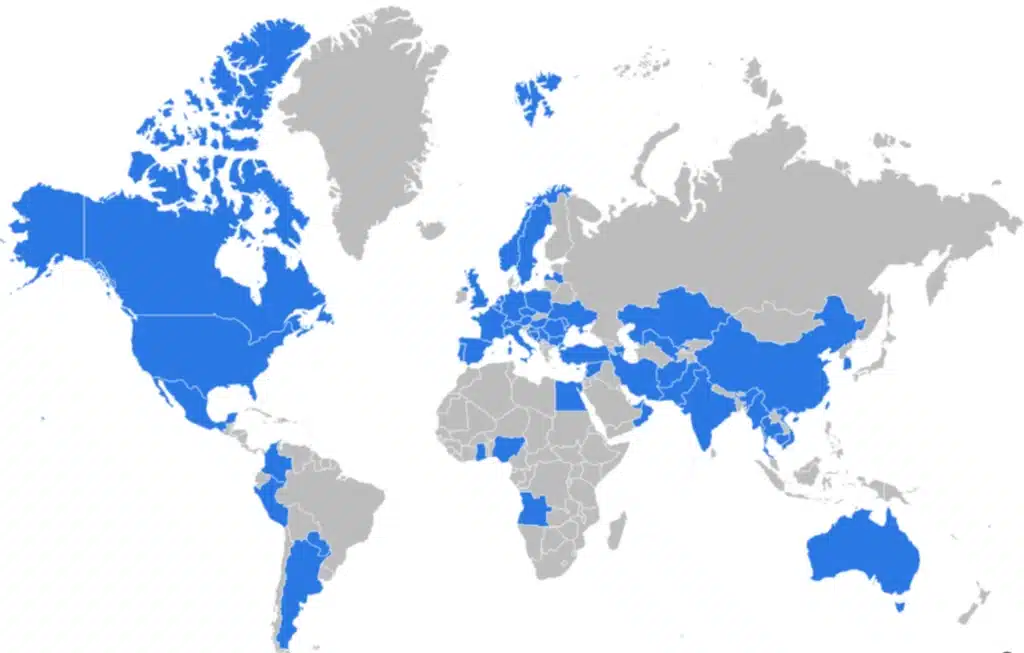
Microsoft is publishing for the first time our research into a subgroup within the Russian state actor Seashell Blizzard and its multiyear initial access operation, tracked by Microsoft Threat Intelligence as the “BadPilot campaign”. This subgroup has conducted globally diverse compromises of Internet-facing infrastructure to enable Seashell Blizzard[…]
Read More
There are countless statistics about cybercrime and one of the most impactful is that for threat actors. Their profits continue to increase year over year and are on track to rise from $9.22 trillion in 2024 to $13.82 trillion by 2028.1 If the financial drain caused by threat[…]
Read More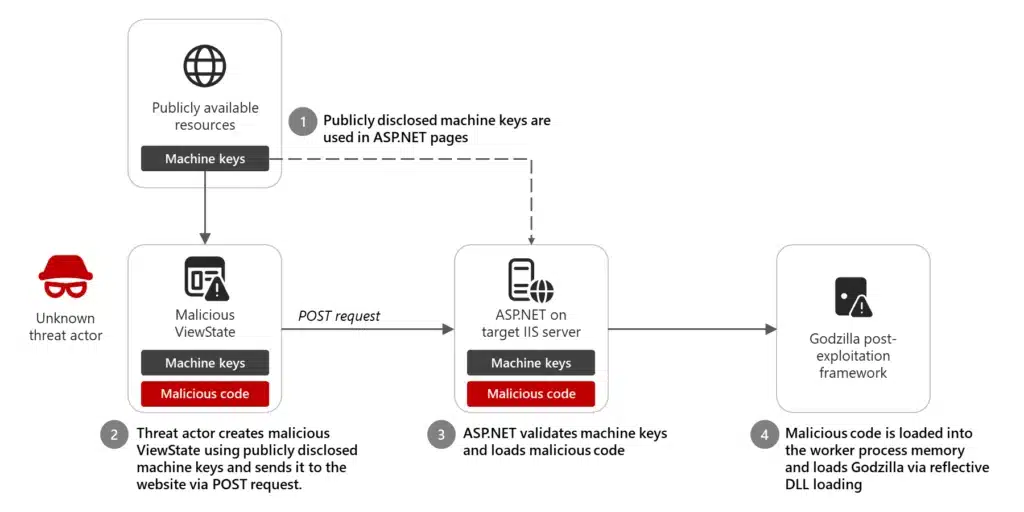
In December 2024, Microsoft Threat Intelligence observed limited activity by an unattributed threat actor using a publicly available, static ASP.NET machine key to inject malicious code and deliver the Godzilla post-exploitation framework. In the course of investigating, remediating, and building protections against this activity, we observed an insecure[…]
Read More
Inspiration can spark in an instant when you’re at a conference. Perhaps you discover a new tool during a keynote that could save you hours of time. Or maybe a peer shares a story over coffee that makes you rethink an approach. One conversation, one session, or one[…]
Read MoreIf 2024 taught us anything, it’s that a proactive, no-compromises approach to security is essential for 2025 and beyond. Nation-states and advanced cybercriminals are making significant investments in infrastructure and automation to intensify familiar cyberattack patterns; password attacks, for example, escalated from 579 incidents per second in 20211[…]
Read More
As a data security global black belt, I help organizations secure AI solutions. They are concerned about data oversharing, data leaks, compliance, and other potential risks. Microsoft Purview is Microsoft’s solution for securing and governing data in generative AI. I’m often asked how long it takes to deploy[…]
Read MoreWe’ve published the 2025 release wave 1 plans for Microsoft Dynamics 365, Microsoft Power Platform, and Role-based Copilot offerings. These plans are a compilation of the new capabilities planned to be released between April 2025 and September 2025. With advancements in agents, automation, intelligence, and seamless integrations, this[…]
Read More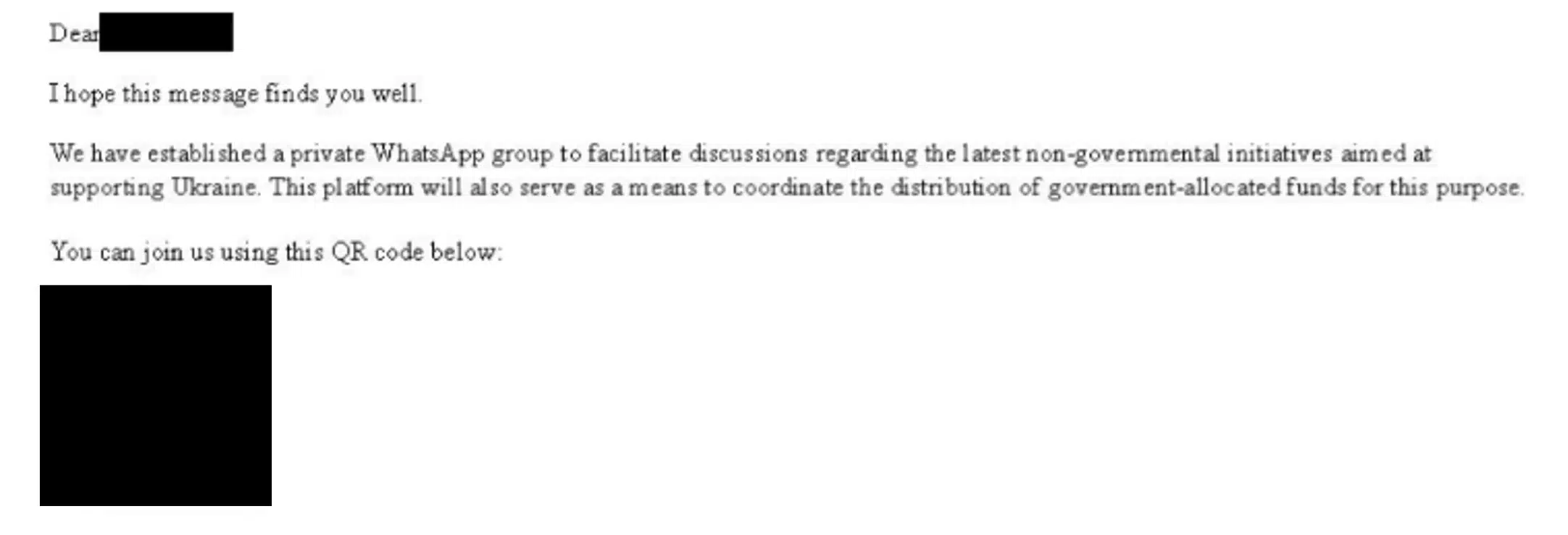
In mid-November 2024, Microsoft Threat Intelligence observed the Russian threat actor we track as Star Blizzard sending their typical targets spear-phishing messages, this time offering the supposed opportunity to join a WhatsApp group. This is the first time we have identified a shift in Star Blizzard’s longstanding tactics,[…]
Read MoreAs our Microsoft AI Tour reached Brussels, Paris, and Berlin toward the end of last year, we met with European organizations that were energized by the possibilities of our latest AI technologies and engaged in deployment projects. They were also alert to the fact that 2025 is the year that[…]
Read More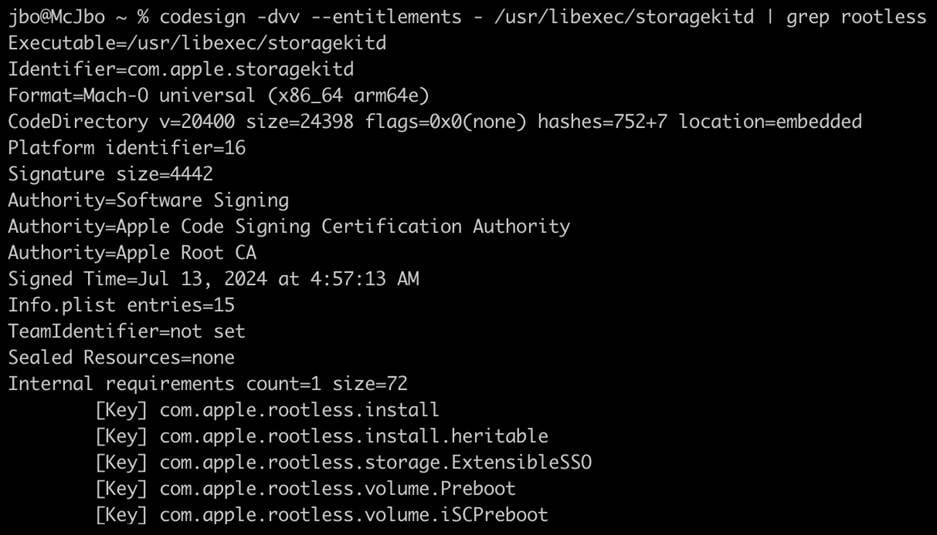
Microsoft Threat Intelligence discovered a new macOS vulnerability that could allow attackers to bypass Apple’s System Integrity Protection (SIP) in macOS by loading third party kernel extensions. SIP is a security technology that restricts the performance of operations that may compromise system integrity; thus, a SIP bypass affects[…]
Read More