Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026

Generative AI presents companies of all sizes with opportunities to increase efficiency and drive innovation. With this opportunity comes a new set of cybersecurity requirements particularly focused on data that has begun to reshape the responsibilities of data security teams. The 2024 Microsoft Data Security Index focuses on[…]
Read More
In 2022, the United States Department of Defense (DoD) released its formal Zero Trust (ZT) Strategy with the goal of achieving enterprise-wide Target Level ZT implementation by September 30, 2027. A pioneer among these departments is the United States Navy, which recently launched Flank Speed—a large-scale zero trust[…]
Read More
The technology landscape is undergoing a massive transformation, and AI is at the center of this change—posing both new opportunities as well as new threats. While AI can be used by adversaries to execute malicious activities, it also has the potential to be a game changer for organizations[…]
Read More
Microsoft is on the front lines helping secure customers worldwide—analyzing and responding to cybersecurity threats, building security technologies, and partnering with organizations to effectively deploy these technologies for increased security. Many of you have been following as we’ve described our Secure Future Initiative, which is pushing the Zero Trust[…]
Read More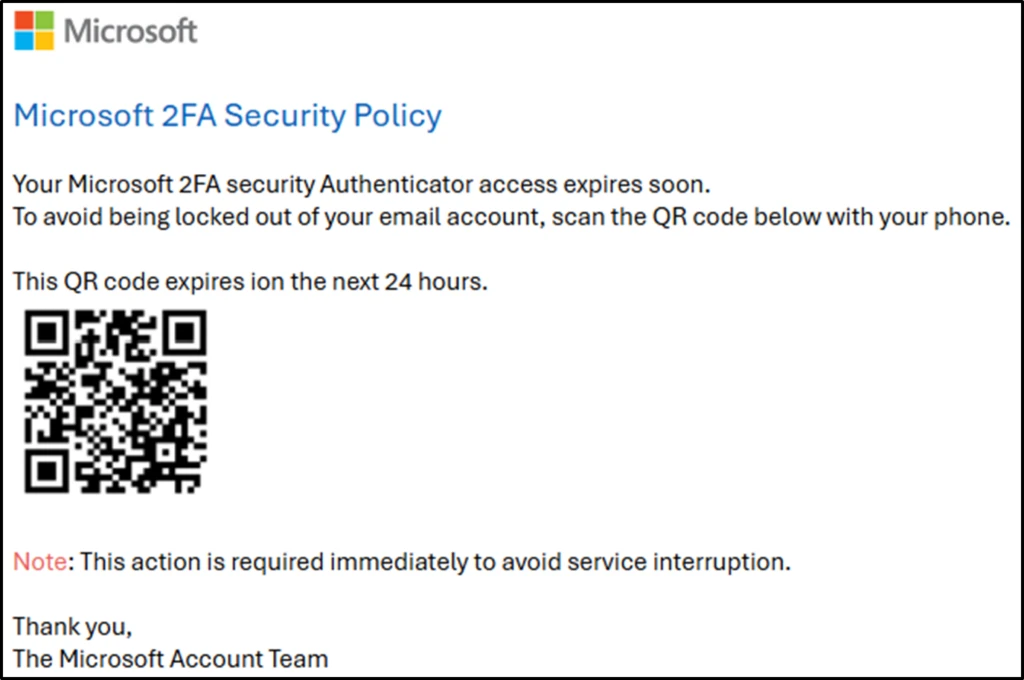
Over the last year, the cybersecurity industry faced a significant surge in QR code phishing campaigns, with some attacks increasing at a growth rate of 270% per month.1 A QR code (short for “Quick Response code”) is a two-dimensional barcode that can be scanned using a smartphone or[…]
Read MoreWe’re excited and honored to be positioned in the Leaders Category in the IDC MarketScape: Worldwide SIEM (security information and event management) for Enterprise 2024 Vendor Assessment (doc #US51541324, September 2024)—our third major analyst report in SIEM to name Microsoft as a Leader. We were recognized in the[…]
Read More
Since August 2023, Microsoft has observed intrusion activity targeting and successfully stealing credentials from multiple Microsoft customers that is enabled by highly evasive password spray attacks. Microsoft has linked the source of these password spray attacks to a network of compromised devices we track as CovertNetwork-1658, also known[…]
Read More
As October draws to a close, marking 21 years of Cybersecurity Awareness Month, cyberattacks continue to be a challenge for businesses of all sizes, however, small and medium businesses (SMBs) face distinct challenges when it comes to cybersecurity. Although SMBs face heightened cybersecurity threats, unlike large enterprises, they[…]
Read More
Now more than ever is the time for every organization to prioritize security. The use of AI by cyberattackers gives them an asymmetric advantage over defenders, as cyberattackers only have to be right once, while defenders have to be right 100% of the time. The way to win[…]
Read More
Since October 22, 2024, Microsoft Threat Intelligence has observed Russian threat actor Midnight Blizzard sending a series of highly targeted spear-phishing emails to individuals in government, academia, defense, non-governmental organizations, and other sectors. This activity is ongoing, and Microsoft will continue to investigate and provide updates as available.[…]
Read More