Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: New Microsoft Dev Box Regional Availability 1 Aprile 2025
- [In preview] Public Preview: CNI Overlay for Application Gateway for Containers and AGIC 1 Aprile 2025
- Transforming public sector security operations in the AI era 1 Aprile 2025
- [In preview] Public Preview: Azure Front Door Custom Cipher Suite 1 Aprile 2025
- [Launched] Public Preview: Azure Monitor Application Insights Auto-Instrumentation for Java and Node Microservices on AKS 1 Aprile 2025
- Retirement: Log Analytics Beta API to Be Retired on March 31, 2026 1 Aprile 2025
- Retirement: Log Analytics Batch API to Be Retired on March 31, 2028 1 Aprile 2025
- [In preview] Public Preview: ExpressRoute Resiliency Enhancements 1 Aprile 2025
- Retirement: Azure Machine Learning SDK v1 Will Be Retired on March 31, 2025 – Transition to Machine Learning SDK v2 31 Marzo 2025
- Retirement: Cloud Services (Extended Support) to Be Retired on March 31, 2027 31 Marzo 2025
Today marks an exciting milestone in Microsoft’s AI journey. This morning, at an event in New York City, we made several major announcements to empower people across work and life—you can read more about Microsoft Bing and Edge with Copilot, what’s new from Microsoft 365 Copilot and Bing[…]
Read More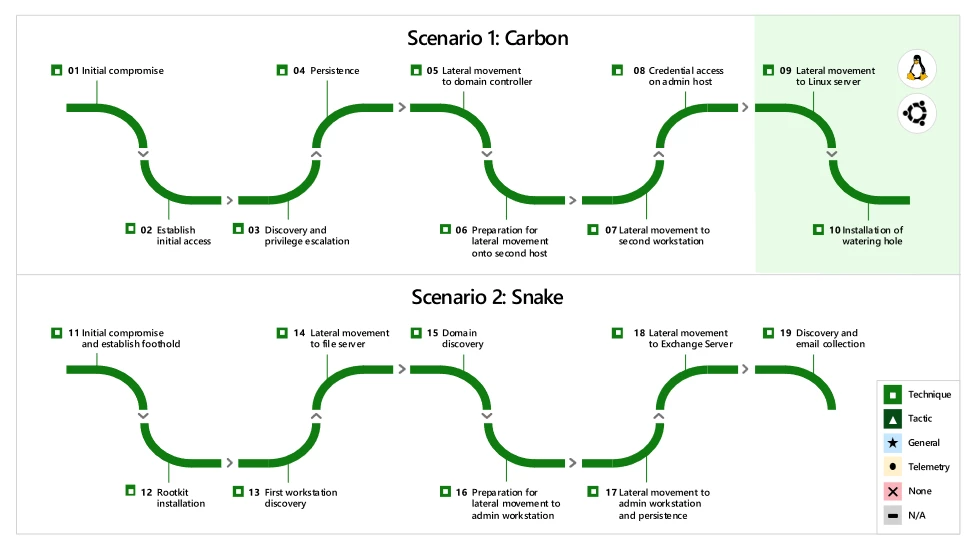
For the fifth consecutive year, Microsoft 365 Defender demonstrated industry-leading extended detection and response (XDR) capabilities in the independent MITRE Engenuity ATT&CK® Evaluations: Enterprise. The attack used during the test highlights the importance of a unified XDR platform and showcases Microsoft 365 Defender as a leading solution, enabled[…]
Read More
Microsoft is proud to be recognized as a Leader in the Forrester Wave™: Zero Trust Platform Providers, Q3 2023 report. At Microsoft, we understand modernizing security is a complex task in this era of ever-evolving cyberthreats and complex digital environments. Serious threats have necessitated a paradigm shift in[…]
Read More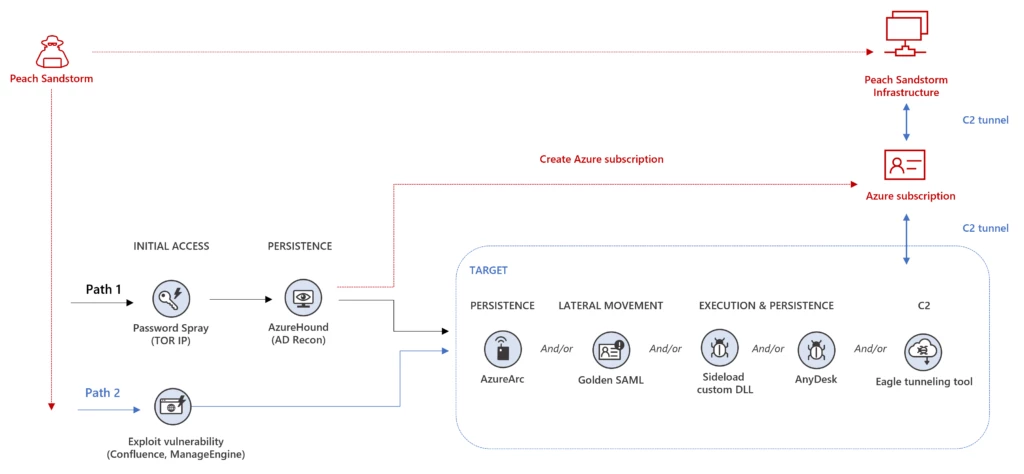
Since February 2023, Microsoft has observed password spray activity against thousands of organizations carried out by an actor we track as Peach Sandstorm (HOLMIUM). Peach Sandstorm is an Iranian nation-state threat actor who has recently pursued organizations in the satellite, defense, and pharmaceutical sectors around the globe. Based[…]
Read More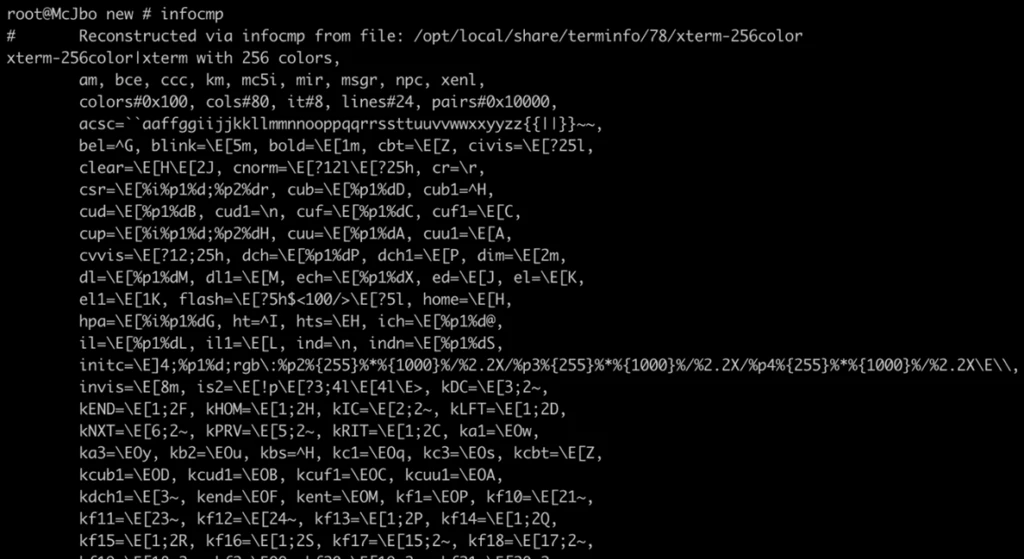
Microsoft has discovered a set of memory corruption vulnerabilities in a library called ncurses, which provides APIs that support text-based user interfaces (TUI). Released in 1993, the ncurses library is commonly used by various programs on Portable Operating System Interface (POSIX) operating systems, including Linux, macOS, and FreeBSD.[…]
Read More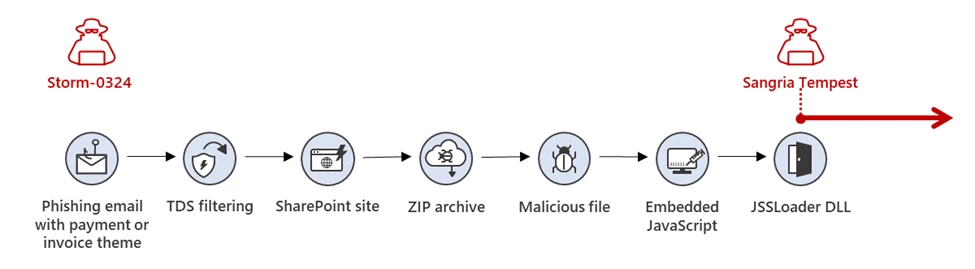
The threat actor that Microsoft tracks as Storm-0324 is a financially motivated group known to gain initial access using email-based initial infection vectors and then hand off access to compromised networks to other threat actors. These handoffs frequently lead to ransomware deployment. Beginning in July 2023, Storm-0324 was[…]
Read More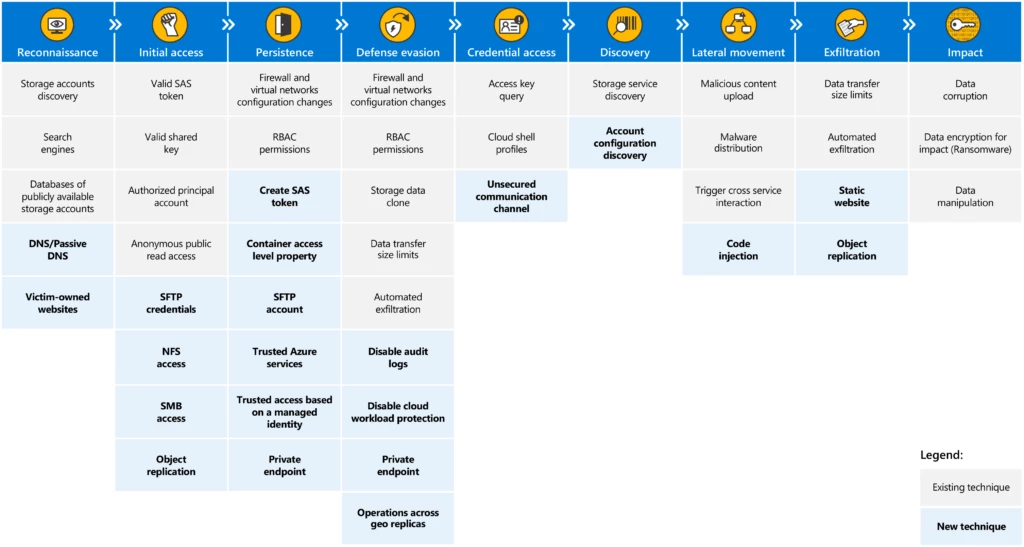
Today, we announce the release of a second version of the threat matrix for storage services, a structured tool that assists in identifying and analyzing potential security threats on data stored in cloud storage services. The matrix, first released in April 2021 as detailed in the blog post[…]
Read More
Data protection and privacy have become business imperatives. In a global survey conducted by Microsoft and leaders in the academic privacy space, 90 percent of respondents said they would not buy from an organization that does not properly protect its data.1 More than ever, people have a high[…]
Read More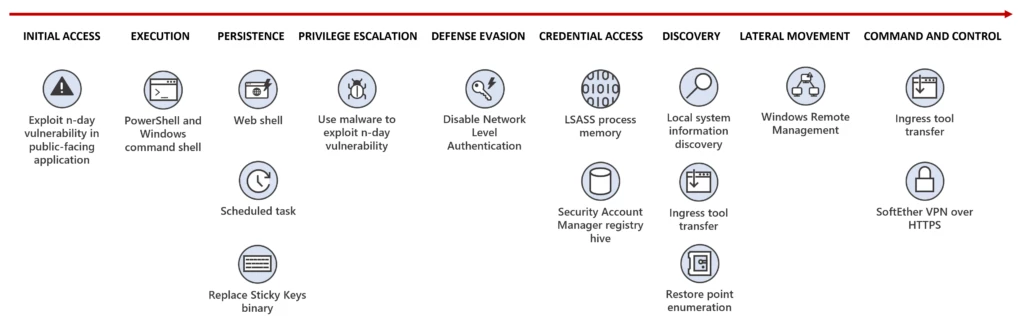
Summary Microsoft has identified a nation-state activity group tracked as Flax Typhoon, based in China, that is targeting dozens of organizations in Taiwan with the likely intention of performing espionage. Flax Typhoon gains and maintains long-term access to Taiwanese organizations’ networks with minimal use of malware, relying on[…]
Read More
Each year, organizations face tens of billions of malware, phishing, and credential threats—with real-world impacts. When an attack succeeds, it can result in grave impacts on any industry. For example, it could delay a police or fire department’s response to an emergency, prevent a hospital from accessing lifesaving[…]
Read More