Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: New Microsoft Dev Box Regional Availability 1 Aprile 2025
- [In preview] Public Preview: CNI Overlay for Application Gateway for Containers and AGIC 1 Aprile 2025
- Transforming public sector security operations in the AI era 1 Aprile 2025
- [In preview] Public Preview: Azure Front Door Custom Cipher Suite 1 Aprile 2025
- [Launched] Public Preview: Azure Monitor Application Insights Auto-Instrumentation for Java and Node Microservices on AKS 1 Aprile 2025
- Retirement: Log Analytics Beta API to Be Retired on March 31, 2026 1 Aprile 2025
- Retirement: Log Analytics Batch API to Be Retired on March 31, 2028 1 Aprile 2025
- [In preview] Public Preview: ExpressRoute Resiliency Enhancements 1 Aprile 2025
- Retirement: Azure Machine Learning SDK v1 Will Be Retired on March 31, 2025 – Transition to Machine Learning SDK v2 31 Marzo 2025
- Retirement: Cloud Services (Extended Support) to Be Retired on March 31, 2027 31 Marzo 2025
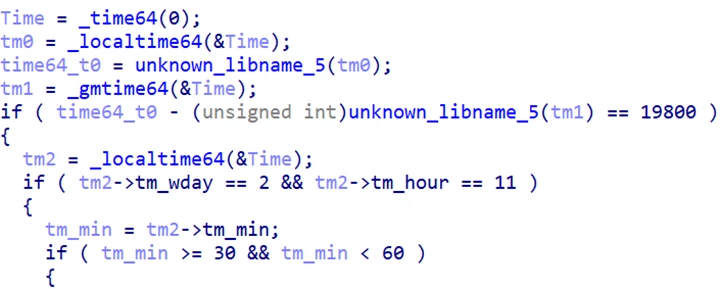
Microsoft Threat Intelligence has uncovered a supply chain attack by the North Korea-based threat actor Diamond Sleet (ZINC) involving a malicious variant of an application developed by CyberLink Corp., a software company that develops multimedia software products. This malicious file is a legitimate CyberLink application installer that has[…]
Read More
Protecting identity from compromise is top of mind for security professionals as identity attacks continue to intensify. Earlier this year we reported that we had observed a nearly three-fold increase in password attacks per second in the last two years, from 579 in 2021 to 4,000 in 2023.1[…]
Read More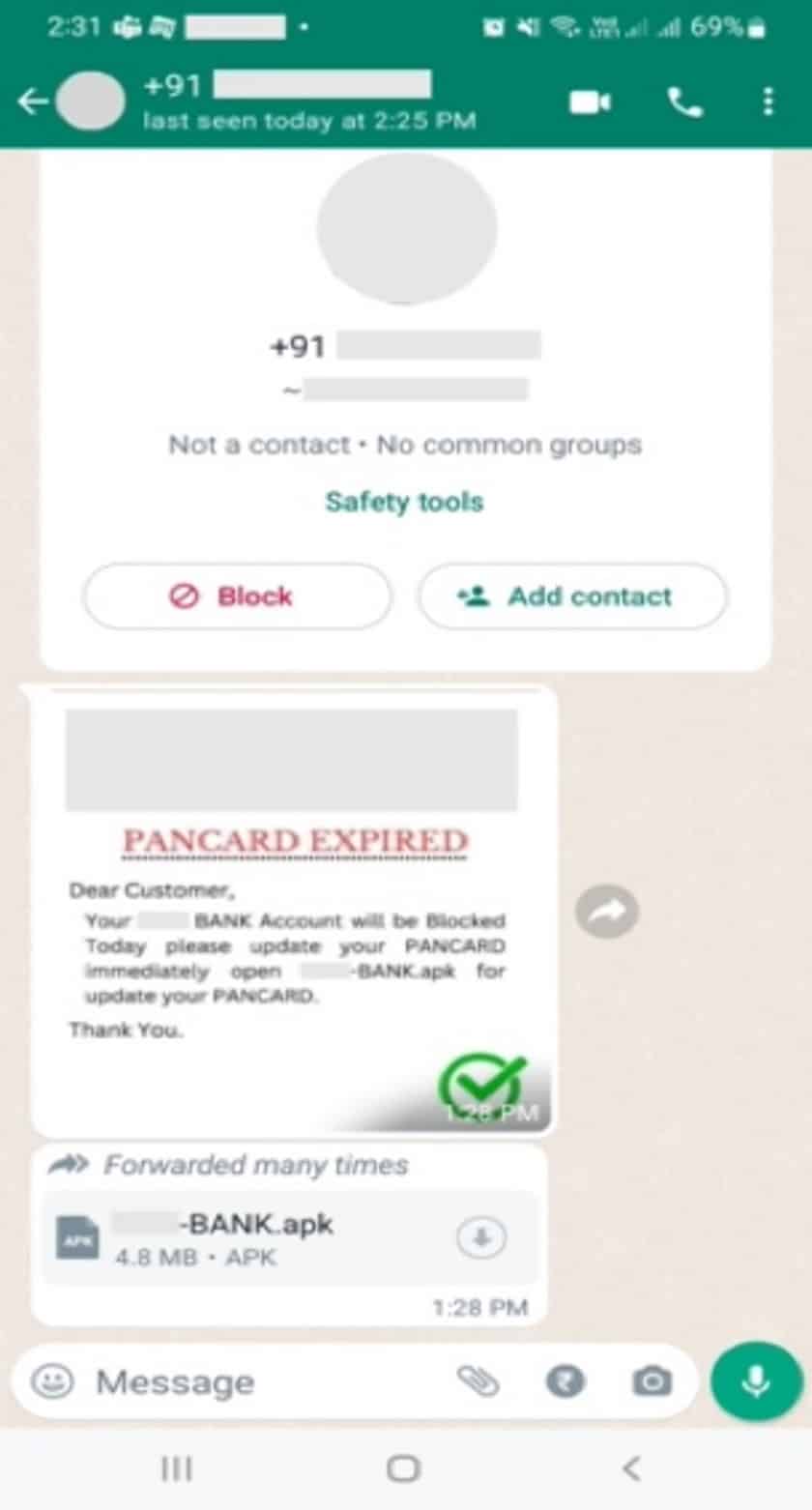
Microsoft has observed ongoing activity from mobile banking trojan campaigns targeting users in India with social media messages designed to steal users’ information for financial fraud. Using social media platforms like WhatsApp and Telegram, attackers are sending messages designed to lure users into installing a malicious app on[…]
Read More
The future of security with AI The increasing speed, scale, and sophistication of recent cyberattacks demand a new approach to security. Traditional tools are no longer enough to keep pace with the threats posed by cybercriminals. In just two years, the number of password attacks detected by Microsoft[…]
Read More
In the ever-evolving landscape of AI, Microsoft Power Platform has the unique opportunity to unlock the vast potential of business application data and logic. Every fragment of enterprise data carries latent insights and untapped productivity. At Microsoft Ignite 2023, witness firsthand how Microsoft Power Platform and Microsoft Dataverse[…]
Read MoreAt the CYBERWARCON 2023 conference, Microsoft and LinkedIn analysts are presenting several sessions detailing analysis across multiple sets of threat actors and related activity. This blog is intended to summarize the content of the research covered in these presentations and demonstrates Microsoft Threat Intelligence’s ongoing efforts to track[…]
Read More
To understand why customers are adopting generative AI solutions like Microsoft Security Copilot, we have to go back to the cyberthreat landscape—which continues to get more challenging. Organizations are facing a surge in cyberattacks while also dealing with a global shortage of security talent. In only the past[…]
Read More
Thousands of security professionals will join us for Microsoft Ignite from November 14 to 17, 2023, where we will share how to embrace the AI era confidently, with protection for people, data, devices, and apps that extends across clouds and platforms. With more than 45 security sessions, there are many[…]
Read More
Extending our commitment to help customers be secure by default, today we’re announcing the auto-rollout of Microsoft Entra Conditional Access policies that will automatically protect tenants based on risk signals, licensing, and usage. We’ve designed these policies based on our deep knowledge of the current cyberthreat landscape to[…]
Read MoreToday Microsoft’s Vice Chair and President Brad Smith shared insight on the global cybersecurity landscape and introduced our Secure Future Initiative. These engineering advances anticipate future cyberthreats, such as increasing digital attacks on identity systems. They also address how we will continue to build secure foundations necessary for[…]
Read More