Notizie per Categorie
Articoli Recenti
- Retirement: Announcing the 3-Year Retirement of Current Architecture for AKS on Windows Server 2019 and Windows Server 2022 29 Marzo 2025
- Retirement: Azure Intelligent Recommendation Service to Be Retired 29 Marzo 2025
- [Launched] Generally Availability: AzAcSnap 11 — Azure Application Consistent Snapshot Tool Updates 28 Marzo 2025
- Retirement: Azure Maps Traffic APIs Version 1.0 to Be Retired on March 31, 2028 28 Marzo 2025
- Retirement: Ubuntu 20.04 Node Pools in AKS 28 Marzo 2025
- Retirement: Azure SQL Database FSV2-Series Offer 28 Marzo 2025
- The future of manufacturing with Microsoft Dynamics 365 is here—are you ready? 28 Marzo 2025
- [Launched] Generally Available: Reminder – End of Limited Time Promotional Discounts on Azure Databricks Serverless Compute Services 28 Marzo 2025
- US Department of Labor’s journey to Zero Trust security with Microsoft Entra ID 27 Marzo 2025
- Beyond productivity: How industry-specific AI fuels growth 27 Marzo 2025
Executive summary:Microsoft Threat Intelligence identified a shift in tactics by Silk Typhoon, a Chinese espionage group, now targeting common IT solutions like remote management tools and cloud applications to gain initial access. While they haven’t been observed directly targeting Microsoft cloud services, they do exploit unpatched applications that[…]
Read MoreExecutive summary:Microsoft Threat Intelligence identified a shift in tactics by Silk Typhoon, a Chinese espionage group, now targeting common IT solutions like remote management tools and cloud applications to gain initial access. While they haven’t been observed directly targeting Microsoft cloud services, they do exploit unpatched applications that[…]
Read MoreNew generative AI models with a broad range of capabilities are emerging every week. In this world of rapid innovation, when choosing the models to integrate into your AI system, it is crucial to make a thoughtful risk assessment that ensures a balance between leveraging new advancements and[…]
Read More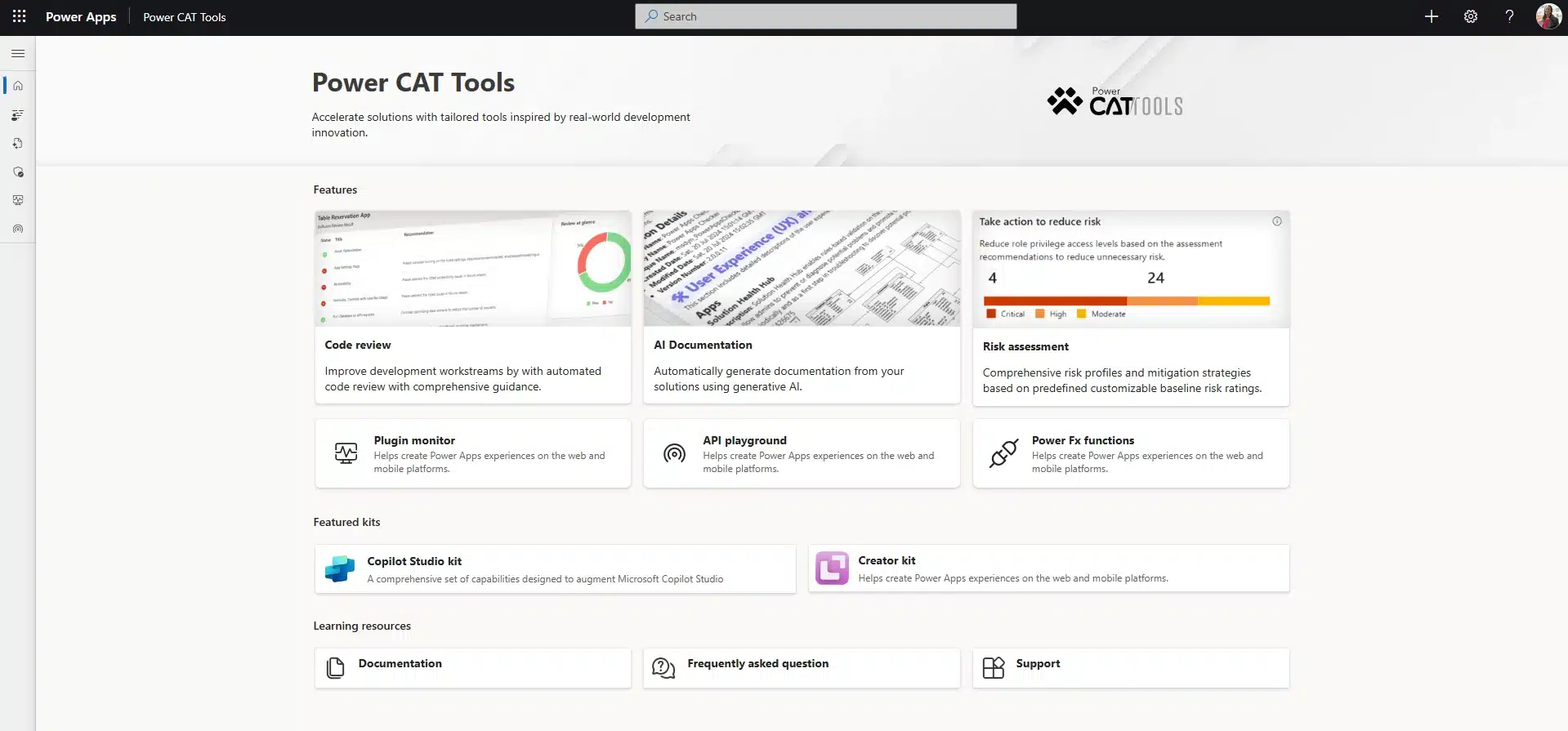
We are thrilled to announce the launch of Power CAT Tools, a comprehensive suite of features designed to enhance your development experience within the Microsoft Power Platform. Whether you’re a seasoned Microsoft Power Platform maker, an administrator looking for ways to optimize development efficiency, or just getting started[…]
Read MoreThe recent breach of the United States Treasury underscores a stark reality: cyber adversaries are no longer just looking for gaps in traditional network security—they are actively exploiting the tools organizations rely on for daily operations. Remote assistance technologies, essential for IT support and business continuity, have become[…]
Read MoreGenerative AI is reshaping almost every industry and the legal field is no different. A Thompson Reuters Institute study of legal professionals found “a remarkable 79% of law firm respondents anticipate AI will have a high or transformational impact on their work within the next five years—a significant[…]
Read More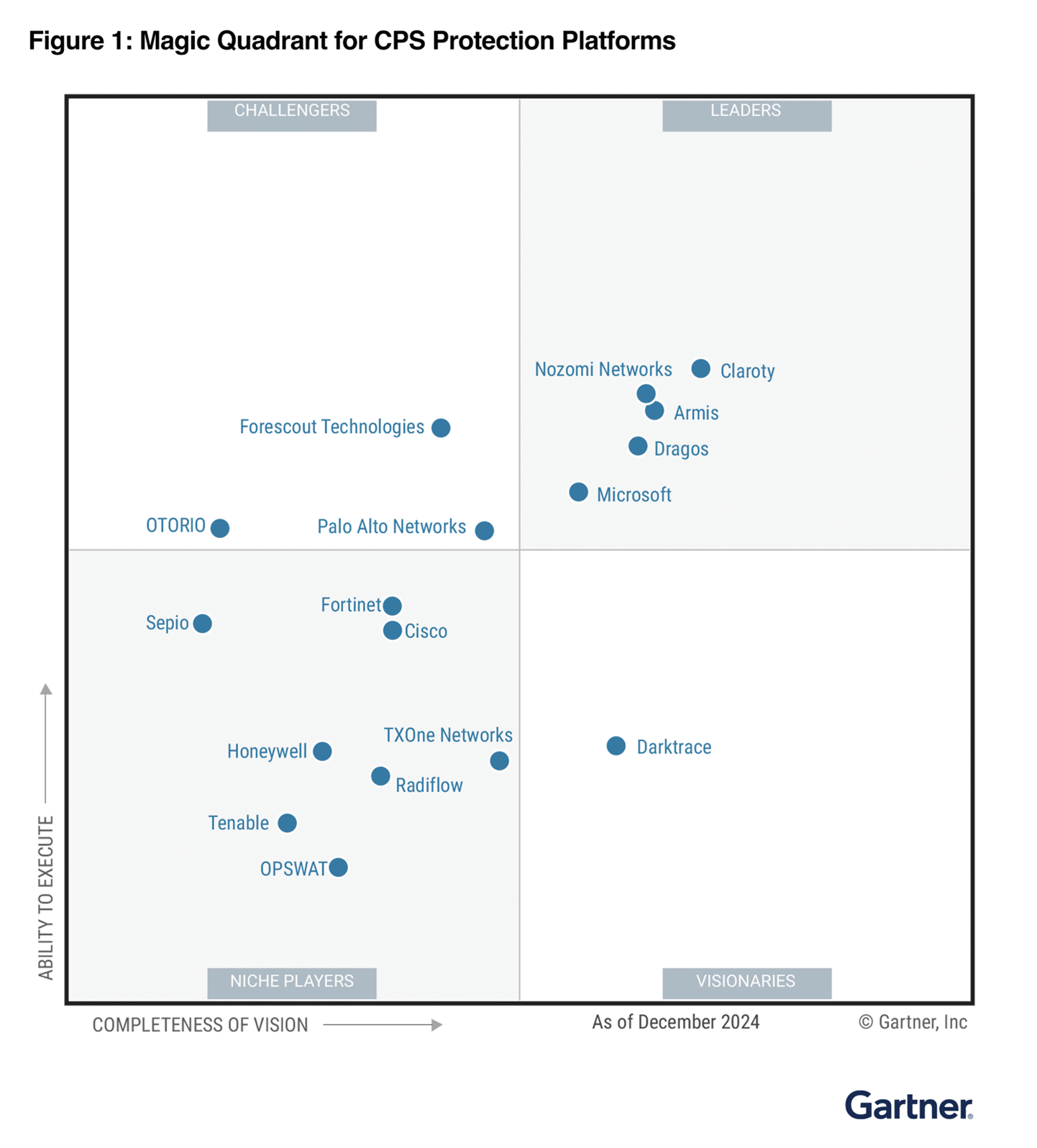
Critical infrastructure is a key target of both physical and cyberattacks. Microsoft has observed an increase in reported attacks on internet-exposed operational technology (OT) devices that control real-world critical processes—like water and wastewater systems, as well as critical functions across industries including healthcare, manufacturing, energy, and more.1 Our[…]
Read More
AI adoption is picking up speed. Many companies are growing their technology estates by embracing powerful new solutions like generative AI. But to maximize the benefits of new technology with confidence, security professionals need to stay compliant with the evolving regulatory and audit requirements in the age of[…]
Read More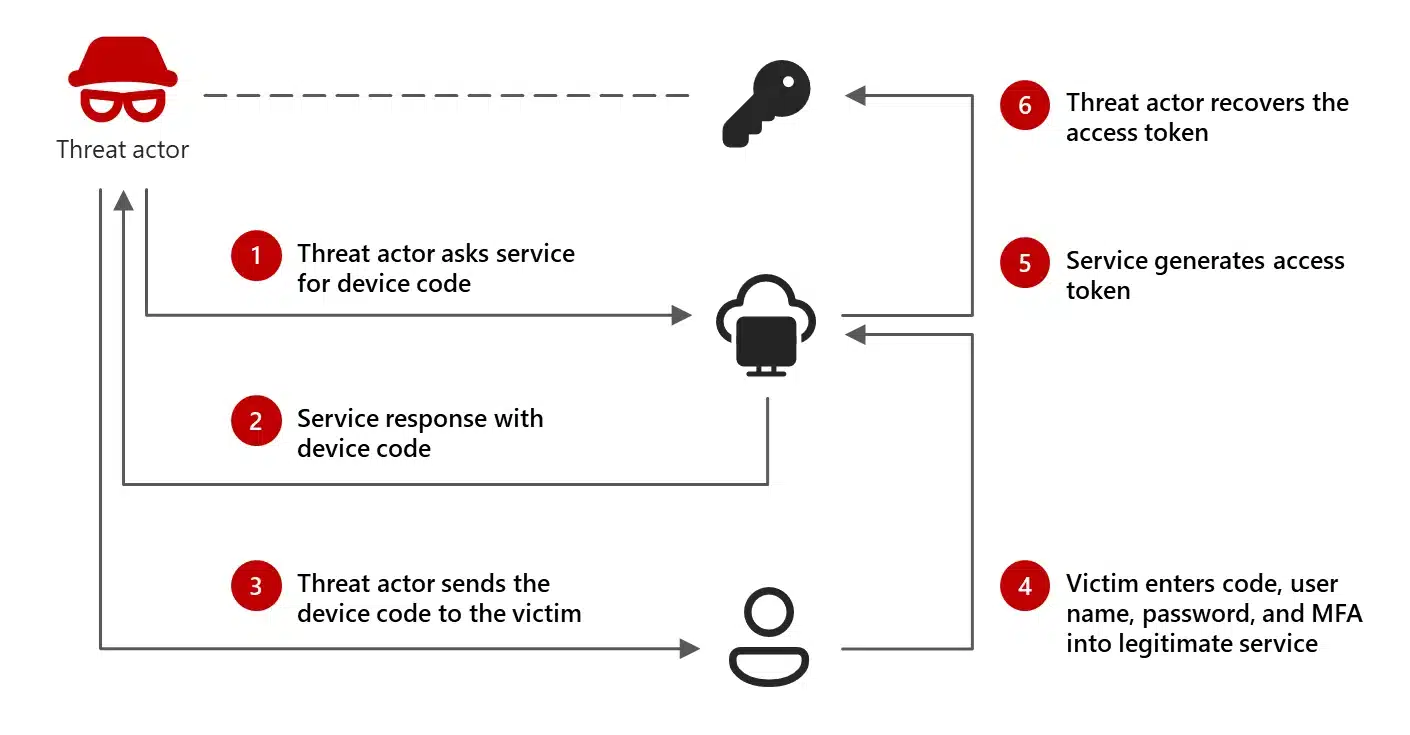
Executive summary Today we’re sharing that Microsoft discovered cyberattacks being launched by a group we call Storm-2372, who we assess with medium confidence aligns with Russia’s interests and tradecraft. The attacks appear to have been ongoing since August 2024 and have targeted governments, NGOs, and a wide range[…]
Read More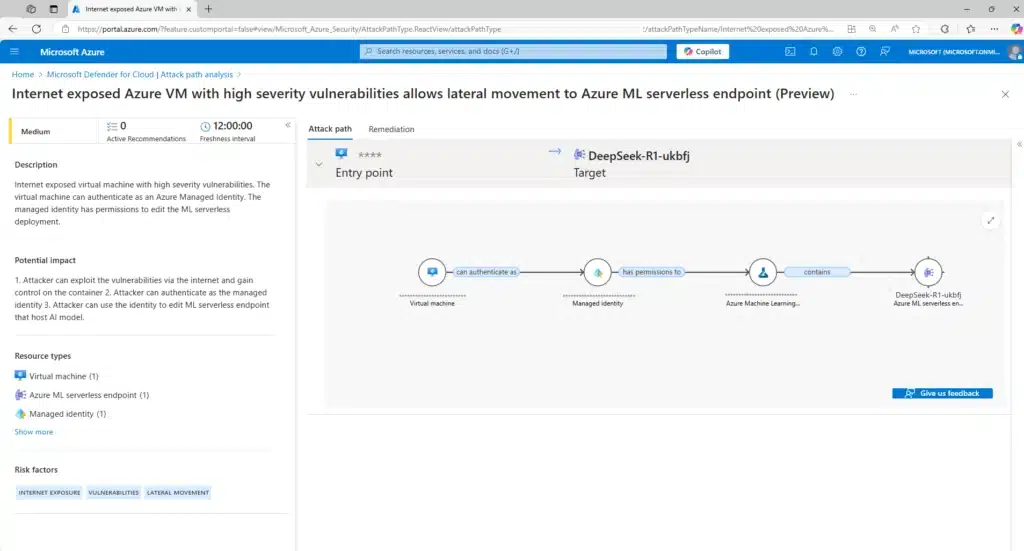
A successful AI transformation starts with a strong security foundation. With a rapid increase in AI development and adoption, organizations need visibility into their emerging AI apps and tools. Microsoft Security provides threat protection, posture management, data security, compliance, and governance to secure AI applications that you build[…]
Read More