Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: New Microsoft Dev Box Regional Availability 1 Aprile 2025
- [In preview] Public Preview: CNI Overlay for Application Gateway for Containers and AGIC 1 Aprile 2025
- Transforming public sector security operations in the AI era 1 Aprile 2025
- [In preview] Public Preview: Azure Front Door Custom Cipher Suite 1 Aprile 2025
- [Launched] Public Preview: Azure Monitor Application Insights Auto-Instrumentation for Java and Node Microservices on AKS 1 Aprile 2025
- Retirement: Log Analytics Beta API to Be Retired on March 31, 2026 1 Aprile 2025
- Retirement: Log Analytics Batch API to Be Retired on March 31, 2028 1 Aprile 2025
- [In preview] Public Preview: ExpressRoute Resiliency Enhancements 1 Aprile 2025
- Retirement: Azure Machine Learning SDK v1 Will Be Retired on March 31, 2025 – Transition to Machine Learning SDK v2 31 Marzo 2025
- Retirement: Cloud Services (Extended Support) to Be Retired on March 31, 2027 31 Marzo 2025

The potential for AI at work is practically endless—and understanding how your teams can accomplish more with generative AI is more important than ever. Every day, more companies are turning to AI-powered low-code and no-code solutions to help their employees work more efficiently and stand out among competitors.[…]
Read More
Identity-based cyberthreats are on the rise. 2023 saw a tenfold increase in threats including phishing, ransomware, and more.1 And bad actors continue to evolve their techniques—making them more sophisticated, more overwhelming, and more believable. From an employee’s viewpoint, every ping, click, swipe, buzz, ding, text, and tap takes[…]
Read More
Many organizations feel the urgency and pressure to protect against increasingly sophisticated attacks. At the same time, these organizations are being propelled into the age of AI with employees that are eager to use AI to build apps and adopt AI-assisted business processes. Chief Information Security Officers (CISOs)[…]
Read More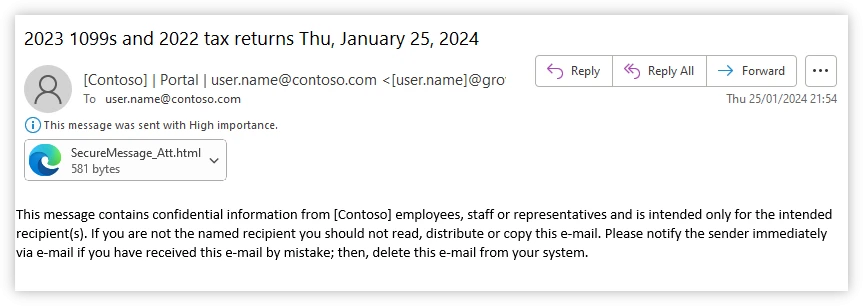
Cybercriminals use social engineering during holidays and important events like tax season to steal user information. Our new Microsoft Threat Intelligence tax season report outlines some of the various techniques that threat actors use to craft their campaigns and mislead taxpayers into revealing sensitive information, making payments to[…]
Read More
In an era defined by rapid technological advancements and digital transformation, protecting it all remains a top challenge. From sophisticated hacking attempts by state-sponsored actors to opportunistic cybercriminals exploiting weaknesses in software and infrastructure, cyberthreats demand constant vigilance and innovative solutions. Traditional security information and event management (SIEM)[…]
Read MoreThe post Microsoft Copilot for Security: General Availability details appeared first on Microsoft Security Blog. Source: Microsoft Security
Read MoreThe post Microsoft named as a Leader in three IDC MarketScapes for Modern Endpoint Security 2024 appeared first on Microsoft Security Blog. Source: Microsoft Security
Read More
Today, we are excited to announce that Microsoft Copilot for Security will be generally available worldwide on April 1, 2024. The industry’s first generative AI solution will help security and IT professionals catch what others miss, move faster, and strengthen team expertise. Copilot is informed by large-scale data[…]
Read MorePrompts are the way to communicate with large language models (LLMs), the driving force behind generative AI technologies like ChatGPT and copilots. They serve as specific instructions that guide and steer the LLM to understand the context of a request to deliver the most relevant and accurate response.[…]
Read MoreMarch is a meaningful month for me personally as we honor Women’s History Month and International Women’s Day. Some of the most powerful role models in my own life are the women who raised me and the community of women who’ve provided the support and encouragement that continues to[…]
Read More