Notizie per Categorie
Articoli Recenti
- Microsoft helps media customers capitalize on AI for greater ROI 2 Aprile 2025
- [In preview] Public Preview: Multi-cluster Eviction and Disruption Budgets with Azure Kubernetes Fleet Manager 2 Aprile 2025
- Microsoft Adaptive Cloud: Advancing edge computing in the defense sector 2 Aprile 2025
- [Launched] Generally Available: Network isolated cluster in AKS 2 Aprile 2025
- [In preview] Public Preview: Multiple Load Balancers for AKS 2 Aprile 2025
- [In preview] Public Preview: Service Allowed IP Ranges in AKS 2 Aprile 2025
- [Launched] Generally Available: Cilium Endpoint Slices in AKS 2 Aprile 2025
- [In preview] Public Preview: Advanced Container Networking Services Cilium L7 Policies Support in AKS 2 Aprile 2025
- [Launched] Generally Available: Azure CNI Node Subnet + Cilium Support 2 Aprile 2025
- [Launched] Generally Available: AKS Cost Recommendations in Azure Advisor 2 Aprile 2025
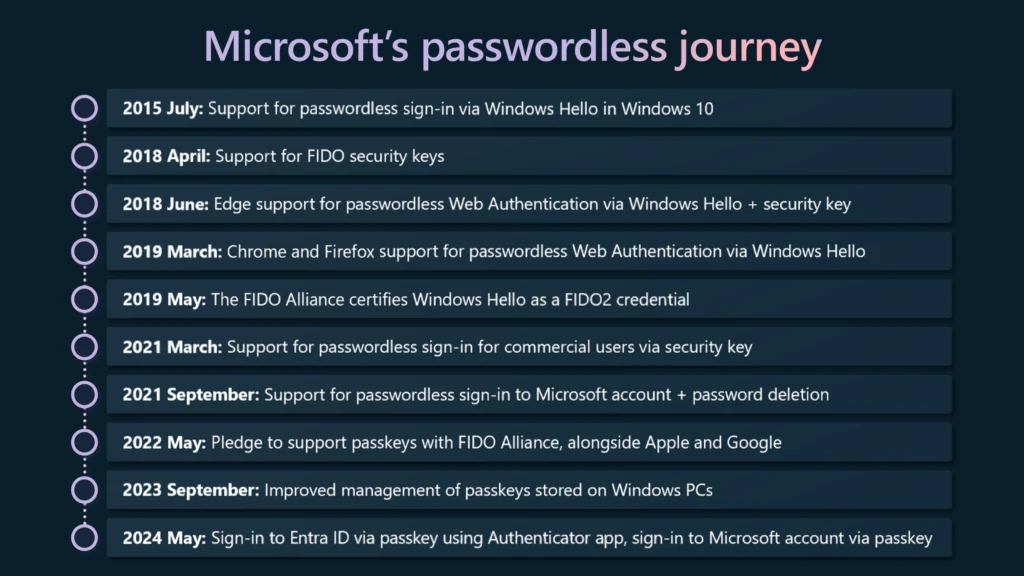
Ten years ago, Microsoft envisioned a bold future: a world free of passwords. Every year, we celebrate World Password Day by updating you on our progress toward eliminating passwords for good. Today, we’re announcing passkey support for Microsoft consumer accounts, the next step toward our vision of simple,[…]
Read More
Microsoft discovered a path traversal-affiliated vulnerability pattern in multiple popular Android applications that could enable a malicious application to overwrite files in the vulnerable application’s home directory. The implications of this vulnerability pattern include arbitrary code execution and token theft, depending on an application’s implementation. Arbitrary code execution[…]
Read MoreThe post Investigating industrial control systems using Microsoft’s ICSpector open-source framework appeared first on Microsoft Security Blog. Source: Microsoft Security
Read More
The cloud security market continues to evolve, reflecting the diligent efforts of security professionals globally. They are at the forefront of developing innovative solutions and strategies to address the sophisticated tactics of cyberattackers. The necessity for these solutions to stay ahead of potential exploitation methods is clear. One[…]
Read More
There’s an increasing demand for skilled cybersecurity professionals. It’s being driven by a surge in cyberthreats and more sophisticated attackers. However, many employers are hesitant to fill open cybersecurity roles and are hiring conservatively in case of economic downturn—even though they understand the importance of having the right[…]
Read More
Microsoft Threat Intelligence is publishing results of our longstanding investigation into activity by the Russian-based threat actor Forest Blizzard (STRONTIUM) using a custom tool to elevate privileges and steal credentials in compromised networks. Since at least June 2020 and possibly as early as April 2019, Forest Blizzard has[…]
Read More
Leading organizations worldwide are harnessing Microsoft Power Platform to revolutionize their operations, with 33 million monthly active users driving innovation and transformation. From groundbreaking applications to significant outcomes, our customer stories vividly illustrate the tangible impact of our technology. We’re thrilled to showcase some of these inspiring stories[…]
Read More
Attackers are constantly seeking new vulnerabilities to compromise Kubernetes environments. Microsoft recently uncovered an attack that exploits new critical vulnerabilities in OpenMetadata to gain access to Kubernetes workloads and leverage them for cryptomining activity. OpenMetadata is an open-source platform designed to manage metadata across various data sources. It[…]
Read More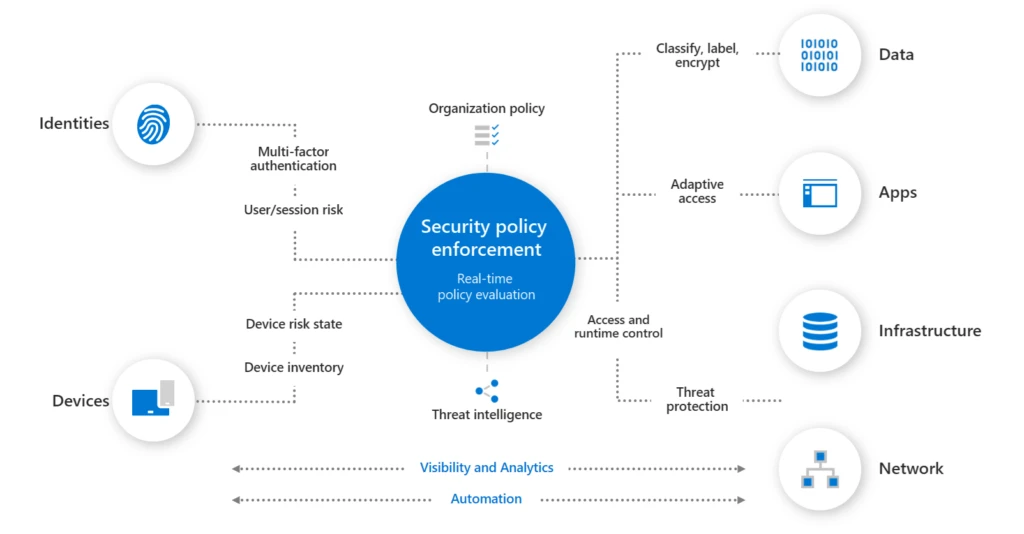
The Department of Defense (DoD) Zero Trust Strategy1 and accompanying execution roadmap2 sets a path for achieving enterprise-wide target-level Zero Trust by 2027. The roadmap lays out vendor-agnostic Zero Trust activities that DoD Components and Defense Industrial Base (DIB) partners should complete to achieve Zero Trust capabilities and[…]
Read More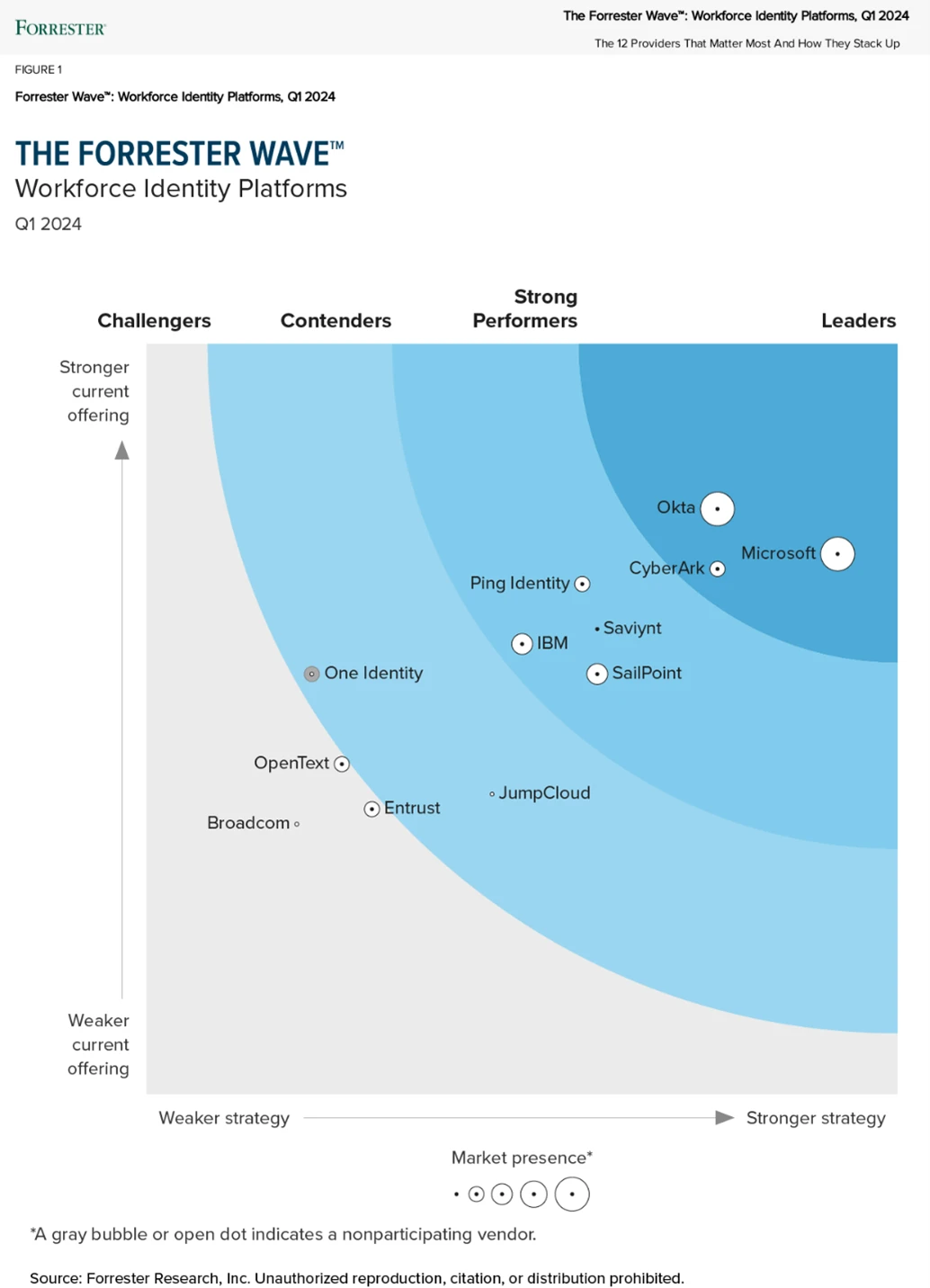
We’re thrilled to announce that Forrester has recognized Microsoft as a Leader in the Forrester Wave™: Workforce Identity Platforms, Q1 2024 report. We’re proud of this recognition, which we believe reflects our commitment to delivering advanced solutions that cater to the evolving needs of our customers in the[…]
Read More