Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: New Microsoft Dev Box Regional Availability 1 Aprile 2025
- [In preview] Public Preview: CNI Overlay for Application Gateway for Containers and AGIC 1 Aprile 2025
- Transforming public sector security operations in the AI era 1 Aprile 2025
- [In preview] Public Preview: Azure Front Door Custom Cipher Suite 1 Aprile 2025
- [Launched] Public Preview: Azure Monitor Application Insights Auto-Instrumentation for Java and Node Microservices on AKS 1 Aprile 2025
- Retirement: Log Analytics Beta API to Be Retired on March 31, 2026 1 Aprile 2025
- Retirement: Log Analytics Batch API to Be Retired on March 31, 2028 1 Aprile 2025
- [In preview] Public Preview: ExpressRoute Resiliency Enhancements 1 Aprile 2025
- Retirement: Azure Machine Learning SDK v1 Will Be Retired on March 31, 2025 – Transition to Machine Learning SDK v2 31 Marzo 2025
- Retirement: Cloud Services (Extended Support) to Be Retired on March 31, 2027 31 Marzo 2025

In the ever-evolving landscape of cyberthreats, staying ahead of malicious actors is a constant challenge. Microsoft Threat Intelligence has observed that gift cards are attractive targets for fraud and social engineering practices. Unlike credit or debit cards, there’s no customer name or bank account attached to them, which[…]
Read More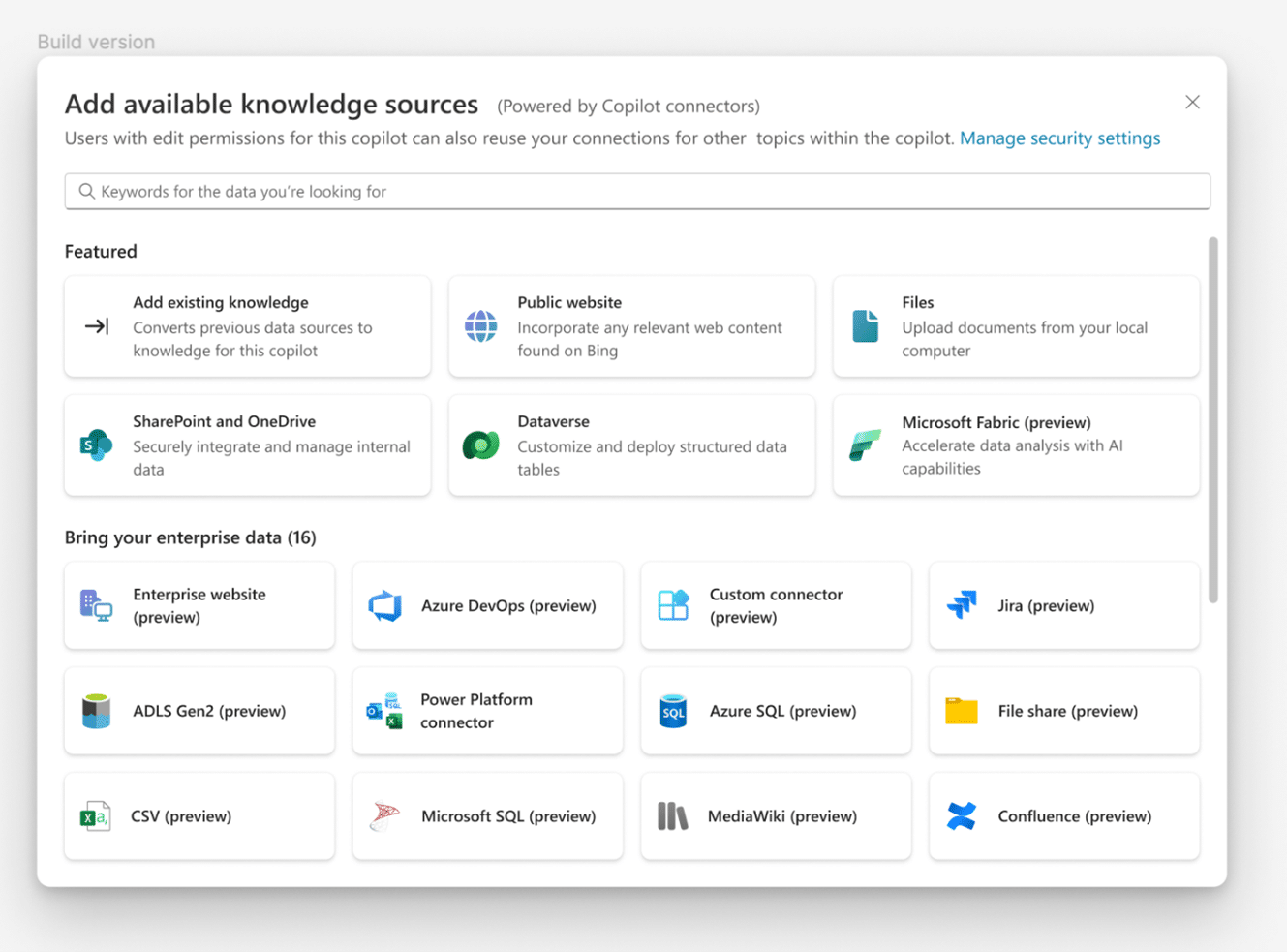
Microsoft Copilot is designed to enhance business productivity by leveraging AI to streamline routine tasks, allowing users to concentrate on strategic and creative endeavors. It boosts organizational efficiency by automating repetitive tasks, freeing up time for the workforce, and enriching solution capabilities with integrated experiences in Microsoft Power[…]
Read More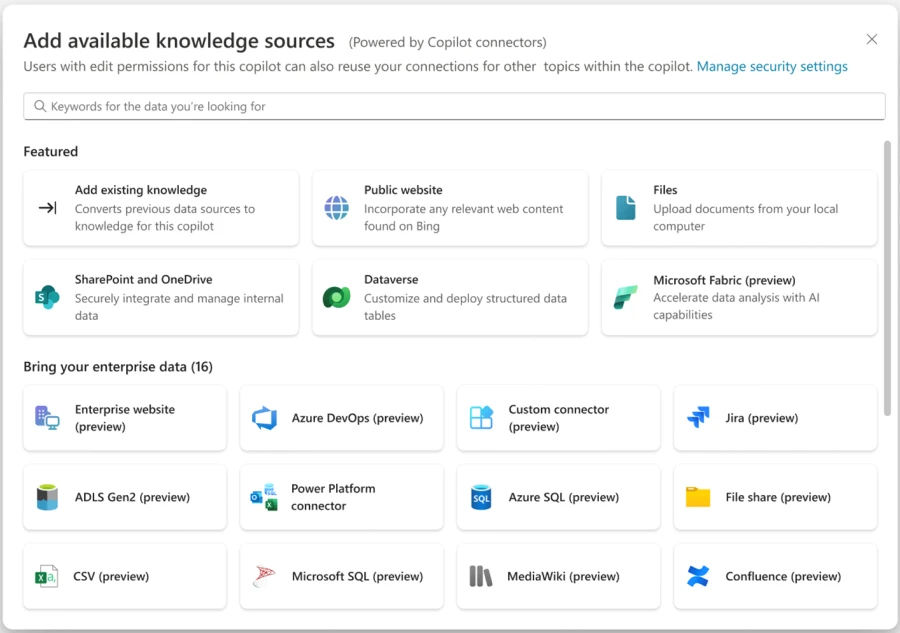
At Microsoft Build 2024, we’re delivering a new set of features for Copilot that enable organizations to achieve their business goals, from Team Copilot to powerful advancements for developers to customize Microsoft Copilot with extensions and connectors or build their own. We’re excited to share the latest AI[…]
Read More
Ahead of the Microsoft Build 2024 conference, we announced a new class of Windows computers, Copilot+ PC. Alongside this exciting new class of PCs, we are introducing important security features and updates that make Windows 11 more secure for users and organizations and give developers the tools to[…]
Read More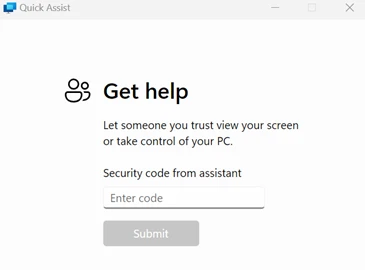
Since mid-April 2024, Microsoft Threat Intelligence has observed the threat actor Storm-1811 misusing the client management tool Quick Assist to target users in social engineering attacks. Storm-1811 is a financially motivated cybercriminal group known to deploy Black Basta ransomware. The observed activity begins with impersonation through voice phishing[…]
Read More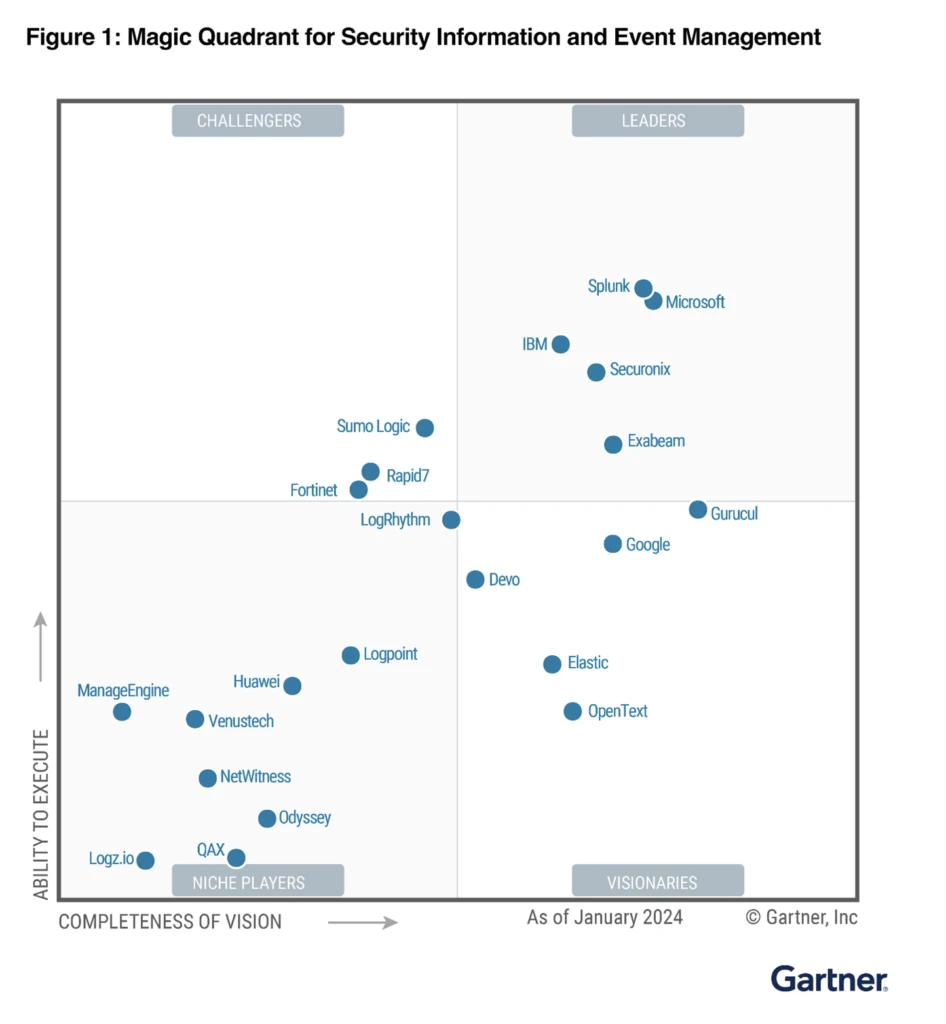
We are pleased to announce that Microsoft has been recognized as a Leader in the Gartner® Magic Quadrant™ for Security Information and Event Management (SIEM).1 We believe our position in the Leaders quadrant validates our vision and continued investments in Microsoft Sentinel making it a best-in-class, cloud-native SIEM[…]
Read More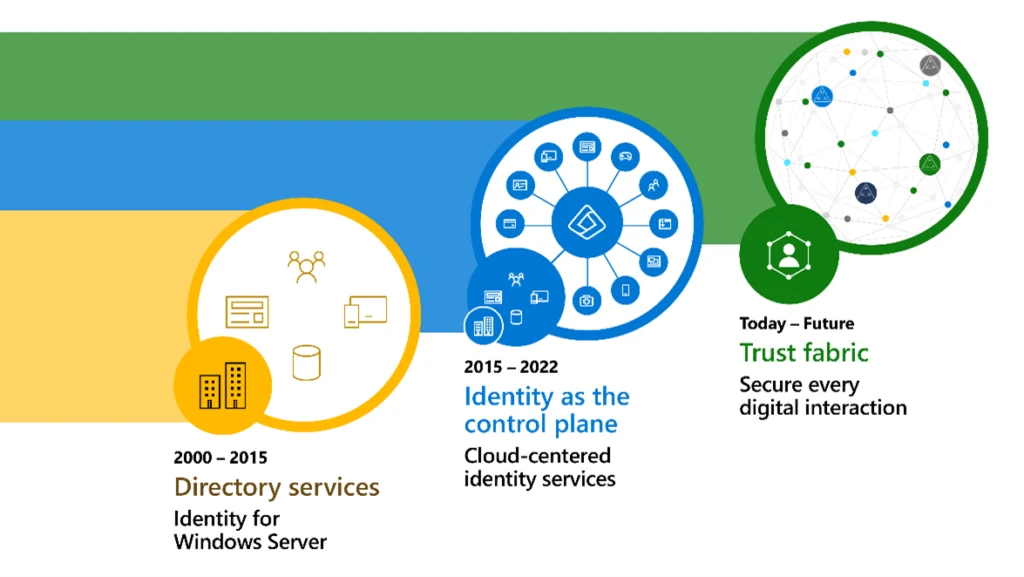
The identity security landscape is transforming rapidly. Every digital experience and interaction is an opportunity for people to connect, share, and collaborate. But first, we need to know we can trust those digital experiences and interactions. Customers note a massive rise in the sheer number of identities they[…]
Read MoreAt this year’s Microsoft Security Excellence Awards, we took a journey through the evolution of cybersecurity from the 1950s to today. While this event theme celebrated the significant technological advancements that have shaped each decade, the main focus was on the Microsoft Intelligent Security Association (MISA) member finalists[…]
Read More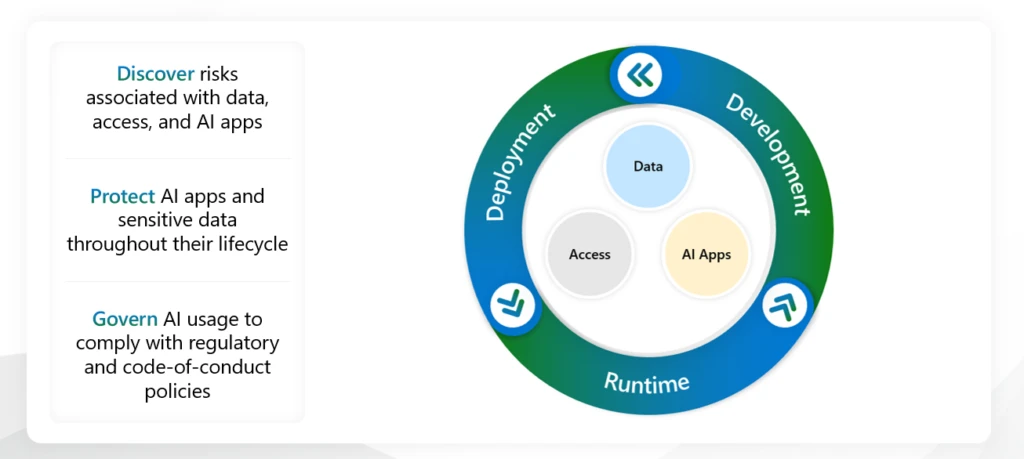
AI is transforming our world, unlocking new possibilities to enhance human abilities and to extend opportunities globally. At the same time, we are also facing an unprecedented threat landscape with the speed, scale, and sophistication of attacks increasing rapidly. To meet these challenges, we must ensure that AI[…]
Read More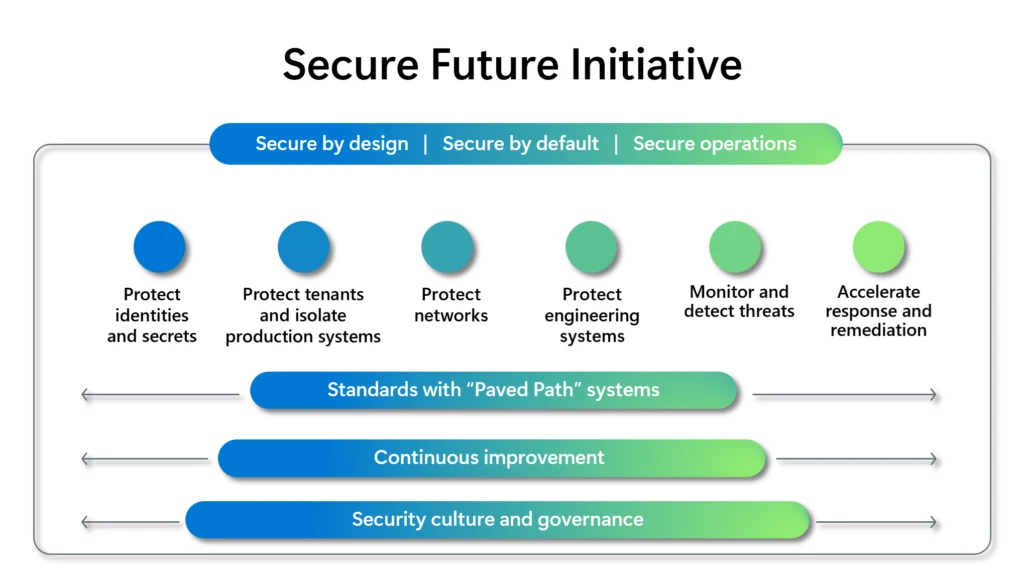
Last November, we launched the Secure Future Initiative (SFI) to prepare for the increasing scale and high stakes of cyberattacks. SFI brings together every part of Microsoft to advance cybersecurity protection across our company and products. Since then, the threat landscape has continued to rapidly evolve, and we[…]
Read More