Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
- [In preview] Private Preview: DCesv6 and ECesv6 series confidential VMs with Intel® TDX 17 Aprile 2025
- [Launched] Generally Available: ExpressRoute Metro Peering locations and Global Reach are now available in more regions 17 Aprile 2025
- [Launched] Generally Available: Azure Front Door custom cipher suite 17 Aprile 2025
- Microsoft’s Secure by Design journey: One year of success 17 Aprile 2025
- [In development] Private Preview: Azure Backup for AKS Now Supports Azure File Share-based Persistent Volumes 16 Aprile 2025
- [In preview] Public Preview: Remote Model Context Protocol (MCP) support in Azure Functions 16 Aprile 2025
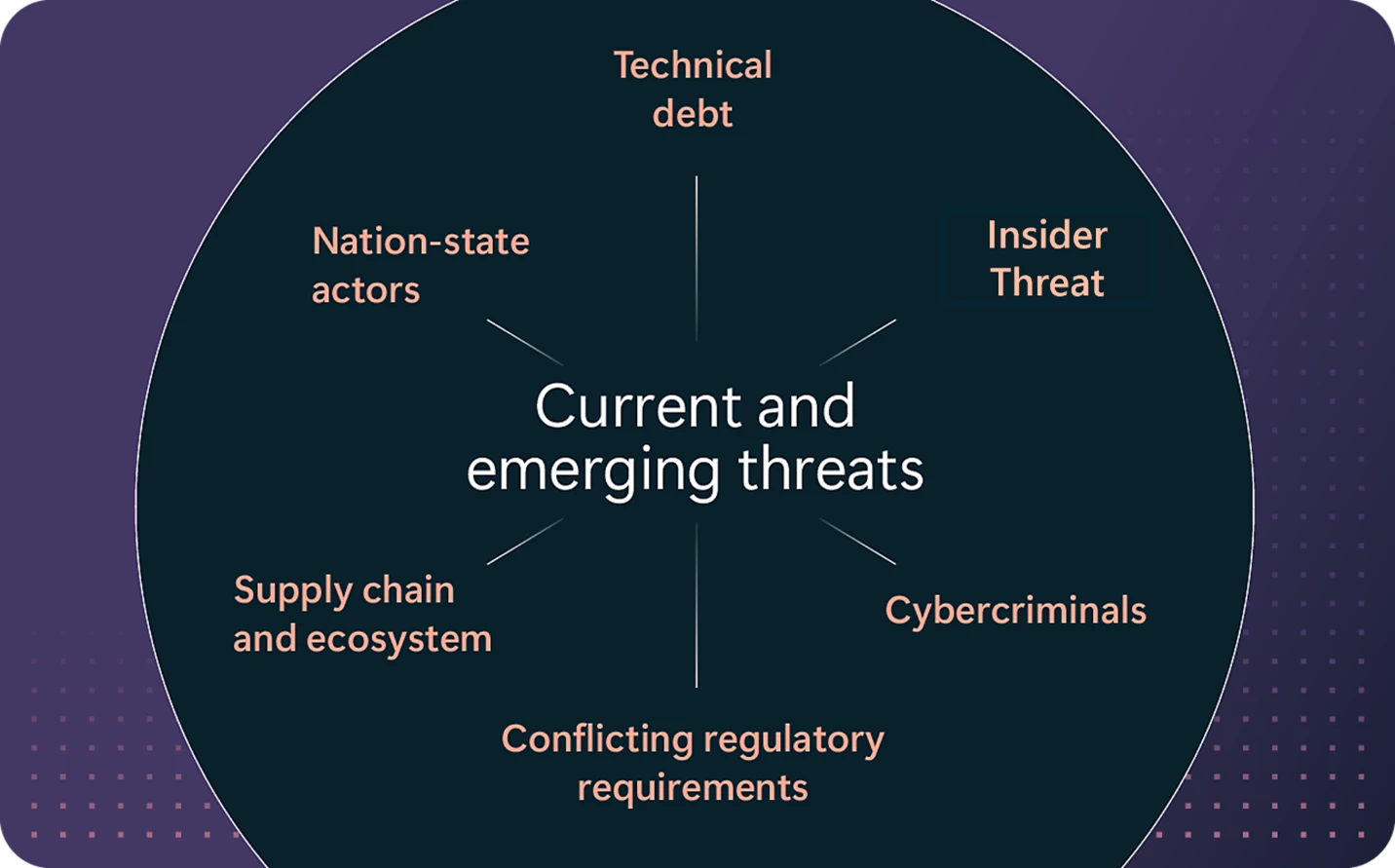
Cybersecurity is one of the top risks facing businesses. Organizations are struggling to navigate the ever-evolving cyberthreat landscape in which 600 million identity attacks are carried out daily.1 The median time for a cyberattacker to access private data from phishing is 1 hour and 12 minutes, and nation-state[…]
Read More
Introduction | Security snapshot | Threat briefingDefending against attacks | Expert profile Microsoft maintains a continuous effort to protect its platforms and customers from fraud and abuse. From blocking imposters on Microsoft Azure and adding anti-scam features to Microsoft Edge, to fighting tech support fraud with new features[…]
Read More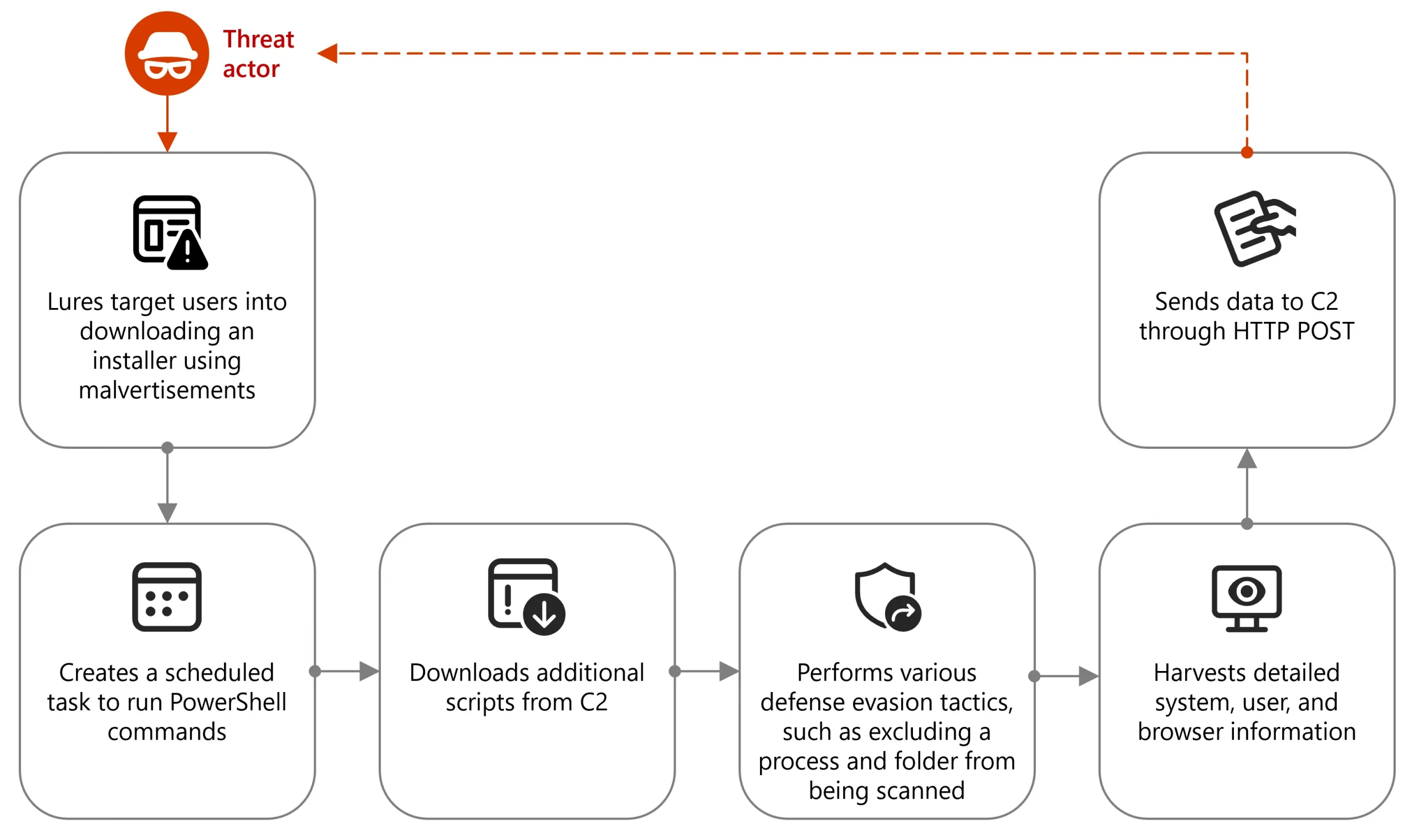
Since October 2024, Microsoft Defender Experts (DEX) has observed and helped multiple customers address campaigns leveraging Node.js to deliver malware and other payloads that ultimately lead to information theft and data exfiltration. While traditional scripting languages like Python, PHP, and AutoIT remain widely used in threats, threat actors[…]
Read More
Just as nature sheds its winter coat, it’s time to prune outdated security measures and plant the seeds of a more robust defense. For years, Microsoft Secure Score has served as a foundational tool for organizations to assess their security posture. By providing a numerical representation of security[…]
Read MoreAs organizations develop, use, and increasingly rely on AI applications, they must address new and amplified security risks. Are you prepared to secure your environment for AI adoption? How about identifying threats to your AI and safeguarding data? Register to attend one or all our Learn Live sessions.Register[…]
Read More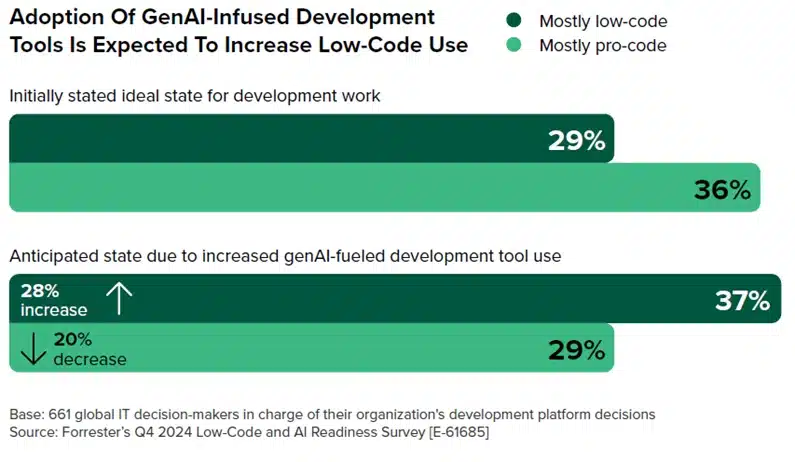
In an era where innovation drives success, organizations are eager to shift to an AI-first development approach, blurring the lines between no-code, low-code, and pro-code development. Using AI tools within Microsoft Power Platform—a comprehensive suite that allows its users to create business applications, workflows, and custom AI-powered agents[…]
Read More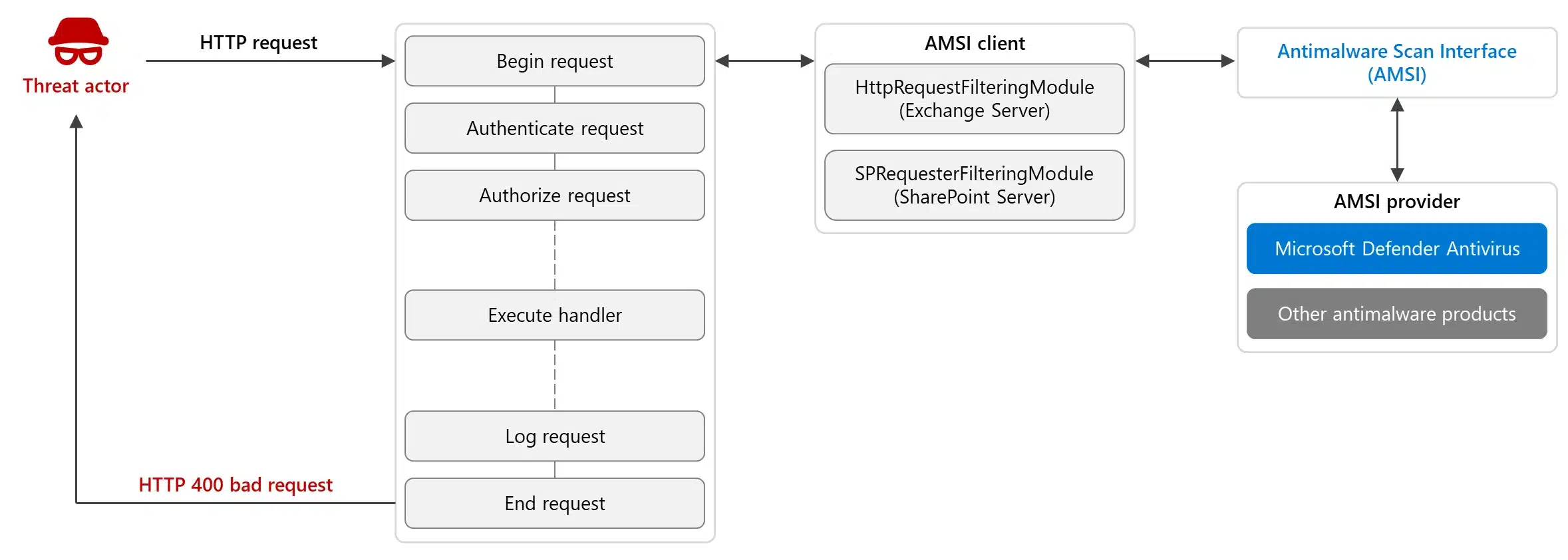
Exchange Server and SharePoint Server are business-critical assets and considered crown jewels for many organizations, making them attractive targets for attacks. To help customers protect their environments and respond to these attacks, Exchange Server and SharePoint Server now integrate with the Windows Antimalware Scan Interface (AMSI), a versatile[…]
Read More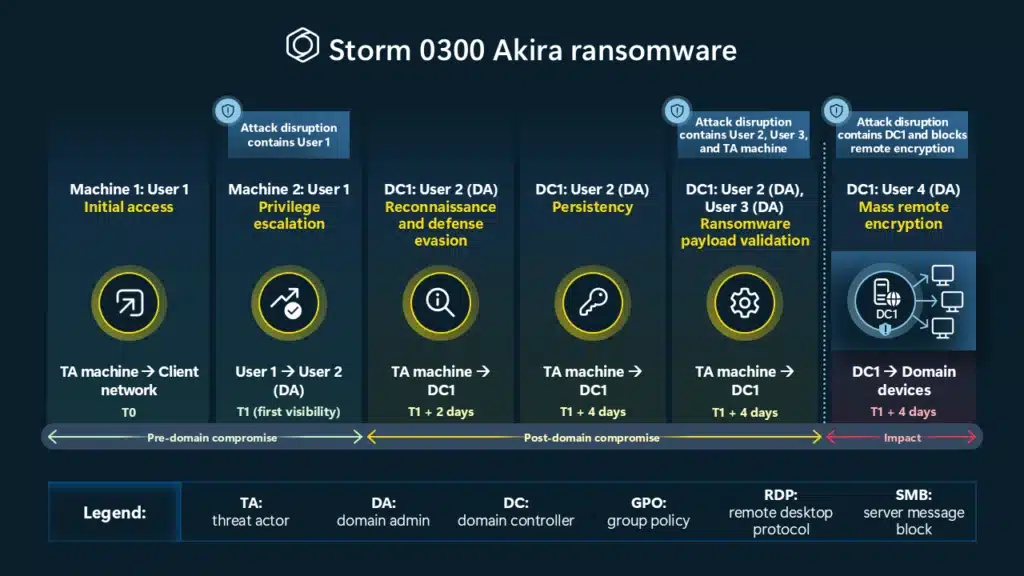
In recent years, human-operated cyberattacks have undergone a dramatic transformation. These attacks, once characterized by sporadic and opportunistic attacks, have evolved into highly sophisticated, targeted campaigns aimed at causing maximum damage to organizations, with the average cost of a ransomware attack reaching $9.36 million in 2024.1 A key[…]
Read MoreMicrosoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC) have discovered post-compromise exploitation of a zero-day elevation of privilege vulnerability in the Windows Common Log File System (CLFS) against a small number of targets. The targets include organizations in the information technology (IT) and real estate[…]
Read More
Microsoft launched its Cybersecurity Governance Council in 2024, and with it, named a group of deputy chief information security officers that ensure comprehensive oversight of the company’s cybersecurity risk, defense, and compliance. These leaders work in tandem with product and engineering leaders across the company to create accountability[…]
Read More