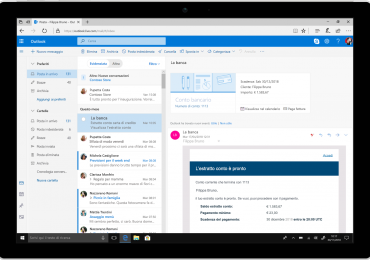
E-mail a cui rispondere, questioni di cui occuparti e luoghi diversi tra cui dividerti: le nuove funzionalità di Outlook, per[…]
Leggi di piùMany small and medium-sized businesses (SMBs) are concerned about their ability to protect their business from cyberattacks and keep their[…]
Leggi di piùSono molte le aziende di piccole e medie dimensioni (PMI) che sono ben consapevoli dell’importanza di proteggersi dai cyberattacchi e[…]
Leggi di più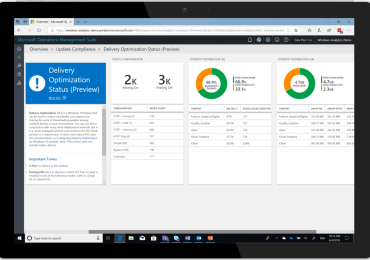
There is a simple way to explain one of the biggest threats to any organization’s infrastructure. It’s just one word:[…]
Leggi di più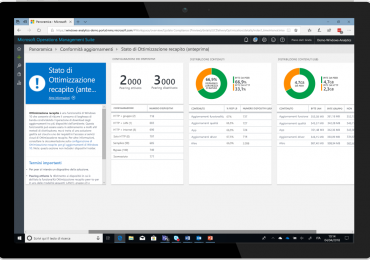
Per descrivere una delle più grandi minacce per l’infrastruttura di qualsiasi organizzazione basta una parola: complessità. La complessità è il[…]
Leggi di piùToday, we’re seeing a new culture of work take shape before our eyes. For many companies, the amount of time[…]
Leggi di piùToday, we’re seeing a new culture of work take shape before our eyes. For many companies, the amount of time[…]
Leggi di più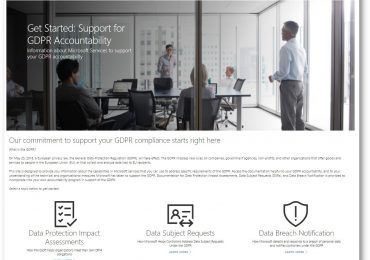
Microsoft has extensive expertise in protecting data, championing privacy, and complying with complex regulations. Microsoft adheres to a set of privacy[…]
Leggi di più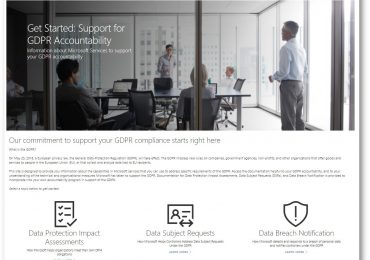
Microsoft has extensive expertise in protecting data, championing privacy, and complying with complex regulations. Microsoft adheres to a set of privacy[…]
Leggi di più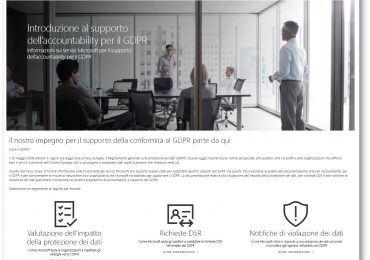
Microsoft vanta una lunga esperienza nella protezione dei dati, nella tutela della privacy e nella conformità a normative complesse. Microsoft[…]
Leggi di piùToday’s post was written by Bryan Ackermann, senior vice president and chief information officer at Korn Ferry. Korn Ferry is[…]
Leggi di piùToday’s post was written by Bryan Ackermann, senior vice president and chief information officer at Korn Ferry. Korn Ferry is[…]
Leggi di piùUltimi Aggiornamenti di Azure Microsoft Cloud
Transport Layer Security (TLS) 1.0 and 1.1 are security protocols for establishing encryption channels over computer networks. Starting March 1,[…]
Leggi di piùStarting February 1, 2025, Azure Automation will discontinue execution of all runbooks that use AzureRM modules. The AzureRM PowerShell module[…]
Leggi di piùStarting April 1, 2025, all jobs running on agent-based User Hybrid Runbook Worker will be stopped. Azure Automation Agent-based User[…]
Leggi di più
The newest wave of business and operating model transformation in corporate banking is underway in one of the oldest domains[…]
Leggi di piùWe’ve published the 2025 release wave 1 plans for Microsoft Dynamics 365, Microsoft Power Platform, and Role-based Copilot offerings. These[…]
Leggi di più
Transforming the customer experience requires a solid foundation of data that is accurate, accessible, and secure. A strong data estate[…]
Leggi di piùWe are excited to announce the release of an Amazon API Gateway integration for Azure API Center. This new feature[…]
Leggi di piùAzure Confidential Ledger is now ISO 27001 certified. ISO 27001 is an internationally recognized standard for information security management systems[…]
Leggi di più
Organizations are experiencing a tidal shift from voluntary to mandatory environmental, social, and governance (ESG) reporting requirements. The European Union’s[…]
Leggi di piùStarting January 15, 2025, Azure Automation is revising its Service and Subscription limits to ensure fair distribution of cloud resources[…]
Leggi di piùWe are excited to announce the general availability of customer managed unplanned failover for Azure Data Lake Storage (ADLS) and[…]
Leggi di piùAdvanced inference with retrieval-augmented generation (RAG) is now supported in open-source KAITO. RAG can be used on a base model[…]
Leggi di più