Ultimi Aggiornamenti di Azure Microsoft Cloud

On January 25, 2024, we published the 2024 release wave 1 plans for Microsoft Dynamics 365 and Microsoft Power Platform, a compilation of new capabilities[…]
Leggi di piùThe graph-match operator in Kusto Query Language (KQL) allows you to query your data as a graph and find matches[…]
Leggi di piùAzure Automation introduces Runtime environment (preview) and enables support for Azure CLI commands in runbooks. Source: Microsoft Azure – aggiornamenti
Leggi di più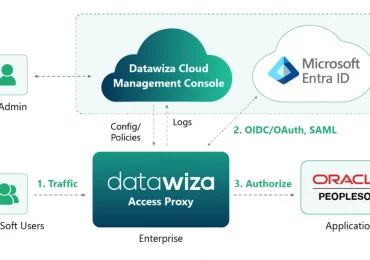
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. In a scenario familiar[…]
Leggi di piùWe’re happy to announce automatic image creation using Azure Image Builder is now generally available. This feature improves your speed[…]
Leggi di piùAzure Monitor VM Insights now supports Dependency Agent for RHEL 8.6 Linux VMs, enabling you to monitor their network connections[…]
Leggi di piùNow you can use the FHIR service in Azure Health Data Services with Azure Active Directory B2C (Azure AD B2C). This[…]
Leggi di piùAdvisor is a personalized cloud consultant that helps you follow best practices to optimize your Azure deployments. It analyzes your[…]
Leggi di piùCustomers now have the capability to configure the circuit breaker property in the backend resource, providing protection for a backend[…]
Leggi di piùCustomers have the ability to create a load balancer that directs traffic to multiple endpoints. Source: Microsoft Azure – aggiornamenti
Leggi di piùRecent updates to the Enterprise plan include improved response caching in Spring Cloud Gateway, a more secure try-out option in[…]
Leggi di piùPrivate preview for the support for Azure VMs using Premium SSD v2 in Azure Site Recovery. Source: Microsoft Azure –[…]
Leggi di più