We’re excited and honored to be positioned in the Leaders Category in the IDC MarketScape: Worldwide SIEM (security information and[…]
Leggi di più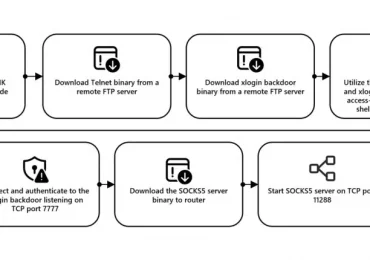
Since August 2023, Microsoft has observed intrusion activity targeting and successfully stealing credentials from multiple Microsoft customers that is enabled[…]
Leggi di più
As October draws to a close, marking 21 years of Cybersecurity Awareness Month, cyberattacks continue to be a challenge for[…]
Leggi di più
Now more than ever is the time for every organization to prioritize security. The use of AI by cyberattackers gives[…]
Leggi di più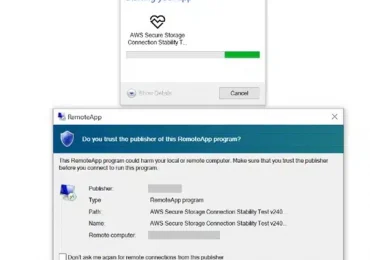
Since October 22, 2024, Microsoft Threat Intelligence has observed Russian threat actor Midnight Blizzard sending a series of highly targeted[…]
Leggi di più
We’ve launched 2024 release wave 2 for Microsoft Dynamics 365, Microsoft Power Platform, and role-based Microsoft Copilot offerings—introducing a rollout[…]
Leggi di piùHealthcare organizations are an increasingly attractive target for threat actors. In a new Microsoft Threat Intelligence report, US healthcare at[…]
Leggi di piùHealthcare organizations are an increasingly attractive target for threat actors. In a new Microsoft Threat Intelligence report, US healthcare at[…]
Leggi di più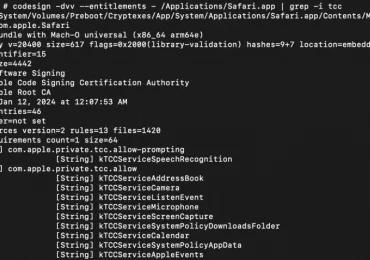
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent,[…]
Leggi di più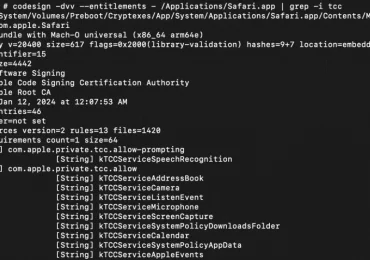
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent,[…]
Leggi di più
Microsoft customers face more than 600 million cybercriminal and nation-state attacks every day, ranging from ransomware to phishing to identity[…]
Leggi di piùAs cyberthreats continue to evolve, it’s essential for security professionals to stay informed about the latest attack vectors and defense[…]
Leggi di più