
In mid-November 2024, Microsoft Threat Intelligence observed the Russian threat actor we track as Star Blizzard sending their typical targets[…]
Leggi di piùAs our Microsoft AI Tour reached Brussels, Paris, and Berlin toward the end of last year, we met with European organizations that[…]
Leggi di più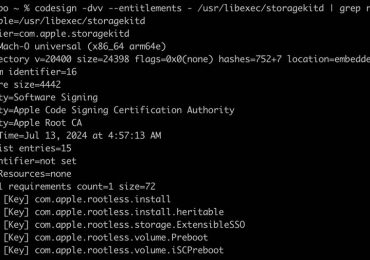
Microsoft Threat Intelligence discovered a new macOS vulnerability that could allow attackers to bypass Apple’s System Integrity Protection (SIP) in[…]
Leggi di più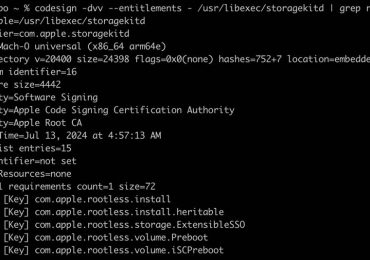
Microsoft Threat Intelligence discovered a new macOS vulnerability that could allow attackers to bypass Apple’s System Integrity Protection (SIP) in[…]
Leggi di più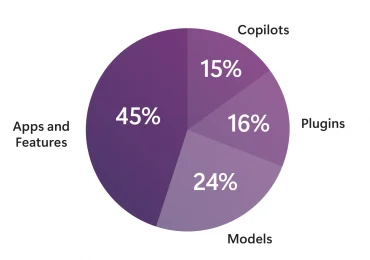
Microsoft’s AI red team is excited to share our whitepaper, “Lessons from Red Teaming 100 Generative AI Products.” The AI[…]
Leggi di più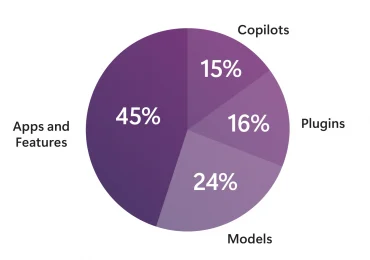
Microsoft’s AI red team is excited to share our whitepaper, “Lessons from Red Teaming 100 Generative AI Products.” The AI[…]
Leggi di più
The expanding attack surface is creating more opportunities for exploitation and adding to the pressure on security leaders and teams.[…]
Leggi di più
The Cybersecurity Infrastructure Security Agency (CISA) Zero Trust Maturity Model (ZTMM) assists agencies in development of their Zero Trust strategies[…]
Leggi di più
Microsoft observes more than 600 million ransomware, phishing, and identity attacks each day.¹ One major theme from our analysis of[…]
Leggi di più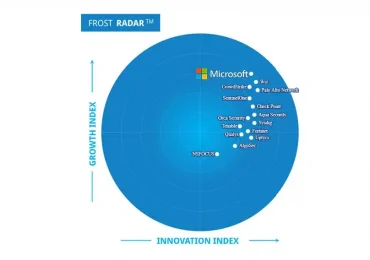
In the ever-evolving landscape of cloud security, Microsoft continues to assert its dominance with its comprehensive and innovative solutions. The[…]
Leggi di più
Traditional security approaches don’t work for AI. Generative AI technology is already transforming our world and has immense positive potential[…]
Leggi di più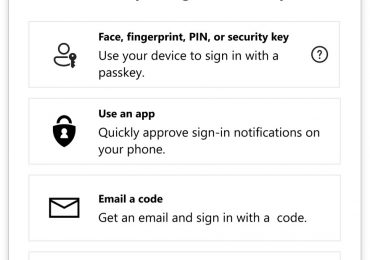
There’s no doubt about it: The password era is ending. Bad actors know it, which is why they’re desperately accelerating[…]
Leggi di più