
Businesses today are constantly facing new and bigger challenges. Technology is diversifying and evolving faster than ever to address these[…]
Leggi di piùOrganizations need to protect their sensitive data including intellectual property, trade secrets, customer data, and personally identifiable information from both[…]
Leggi di piùThis blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. You’ve implemented multifactor authentication[…]
Leggi di più
Today, Microsoft announced the successful completion of the Cloud Data Management Capabilities (CDMC) 14 Key Controls and Automations certification, conducted[…]
Leggi di più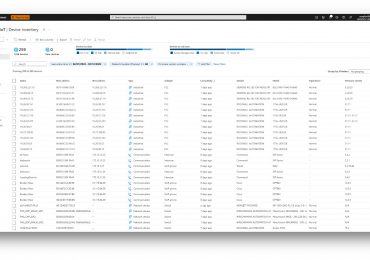
Traditionally, operational technology (OT) and IT have occupied separate sides of enterprise security. But with digital transformation and the advent[…]
Leggi di più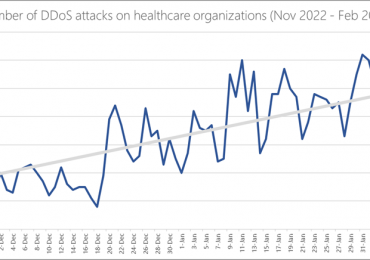
In the last year, geopolitical tension has led to an uptick of reported cybercrime events fueled by hacktivist groups. The[…]
Leggi di piùMicrosoft Secure is our first flagship event designed just for security professionals. On March 28, 2023, we will bring together[…]
Leggi di più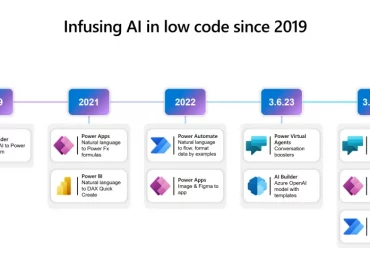
Microsoft Power Platform is reinventing software development with AI-powered no-code development. Today, Microsoft Power Platform is announcing Copilot in Power[…]
Leggi di piùWe’re living in a seismic era for data security. Chief information security officers (CISOs) have to contend with a digital[…]
Leggi di più
Adversary-in-the-middle (AiTM) phishing kits are part of an increasing trend that is observed supplanting many other less advanced forms of[…]
Leggi di piùWomen’s History Month is a special time for me as I reflect on all the great innovations women have made[…]
Leggi di più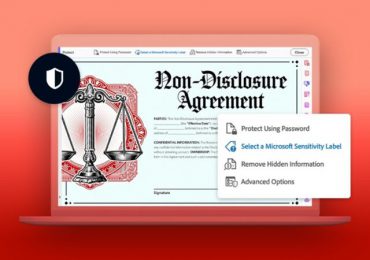
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Data security and compliance[…]
Leggi di più