As the most influential technology of our lifetime, AI has the power to reshape how organizations secure their environments. AI’s[…]
Leggi di piùToday we are releasing an open automation framework, PyRIT (Python Risk Identification Toolkit for generative AI), to empower security professionals[…]
Leggi di piùThe process of writing, refining, and optimizing inputs—or “prompts”—to encourage generative AI systems to create specific, high-quality outputs is called[…]
Leggi di più
The Network and Information Security Directive 2 (NIS2) is a continuation and expansion of the previous European Union (EU) cybersecurity[…]
Leggi di più
The world of cybersecurity is undergoing a massive transformation. AI is at the forefront of this change, and has the[…]
Leggi di piùOver the last year, the speed, scale, and sophistication of attacks has increased alongside the rapid development and adoption of[…]
Leggi di più
Industry leading organizations across the globe are using Microsoft Power Platform to build applications, automate business processes, and drive innovation.[…]
Leggi di più
Organizations everywhere are on a lightning-fast learning trajectory to understand the potential of generative AI and its implications for their[…]
Leggi di più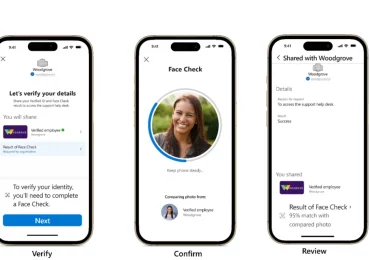
Today, I’m thrilled to announce the expansion of Microsoft Entra Verified ID to include Face Check—a privacy-respecting facial matching feature[…]
Leggi di più
In the cybersecurity industry, there are many events to choose from. You as a cybersecurity professional are left wondering which[…]
Leggi di più
The power of endpoint management Learn how to empower your workforce Today, we are taking a significant step in completing[…]
Leggi di più
Jupyter notebooks are continuing to grow in popularity in information security as an alternative or supplement to mainstream security operations[…]
Leggi di più