
Numerous cybersecurity tools exist to help organizations protect their data, people, and systems. There are different tools that check emails[…]
Leggi di più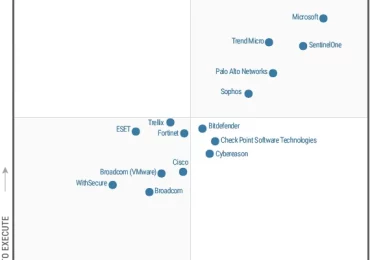
It’s no secret that ransomware is top of mind for many chief information security officers (CISOs) as the number of[…]
Leggi di più
The security landscape is changing fast. In 2023, we saw a record-high 30 billion attempted password attacks per month, a[…]
Leggi di più
Since mid-November 2023, Microsoft Threat Intelligence has observed threat actors, including financially motivated actors like Storm-0569, Storm-1113, Sangria Tempest, and[…]
Leggi di più
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Along with every merger[…]
Leggi di più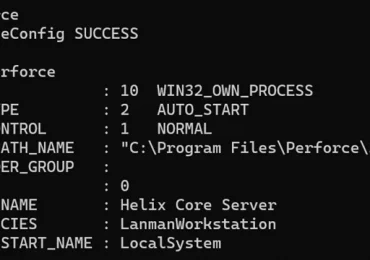
Microsoft discovered, responsibly disclosed, and helped remediate four vulnerabilities that could be remotely exploited by unauthenticated attackers in Perforce Helix[…]
Leggi di più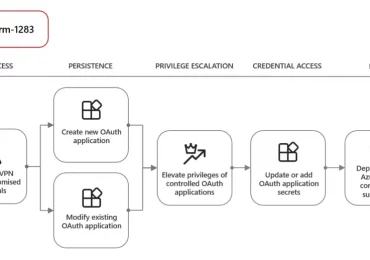
Threat actors are misusing OAuth applications as an automation tool in financially motivated attacks. OAuth is an open standard for[…]
Leggi di piùThe post Strengthening identity protection in the face of highly sophisticated attacks appeared first on Microsoft Security Blog. Source:[…]
Leggi di più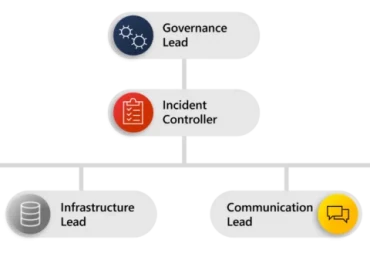
As enterprise networks grow in both size and complexity, securing them from motivated cyberthreat actors becomes more challenging. The incident[…]
Leggi di più
In the past few years, we have witnessed how digital and cloud transformation has accelerated the growth of data. With[…]
Leggi di piùMicrosoft Threat Intelligence continues to track and disrupt malicious activity attributed to a Russian state-sponsored actor we track as Star[…]
Leggi di più
First announced in March 2023, Microsoft Security Copilot—Microsoft’s first generative AI security product—has sparked major interest. The widespread enthusiasm was[…]
Leggi di più