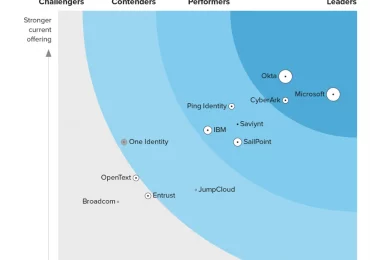
We’re thrilled to announce that Forrester has recognized Microsoft as a Leader in the Forrester Wave™: Workforce Identity Platforms, Q1[…]
Leggi di più
As we continue to integrate generative AI into our daily lives, it’s important to understand the potential harms that can[…]
Leggi di più
Today we launched the 2024 release wave 1 for Microsoft Dynamics 365 and Microsoft Power Platform, a rollout of new features and enhanced capabilities[…]
Leggi di più
The security of your organization directly correlates with your ability to transform and achieve your business objectives. Microsoft can help[…]
Leggi di più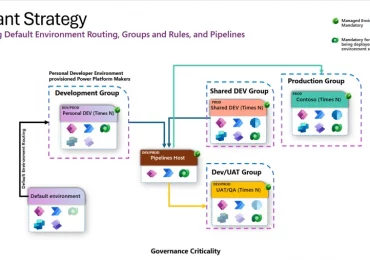
Preview Microsoft Power Platform environment groups and rules As organizations expand their Microsoft Power Platform footprint to meet the needs[…]
Leggi di più
Today, I am excited to announce the public preview of our unified security operations platform. When we announced a limited[…]
Leggi di più
We know managing privacy is harder than ever. The increasing complexity of regulatory requirements and constantly changing regulations make day-to-day[…]
Leggi di più
Are you curious about some of the innovations that make Microsoft Power Platform a game-changer for businesses of all sizes[…]
Leggi di più
The past 12 months marked the beginning of the era of AI. In March 2023, Microsoft took the lead in[…]
Leggi di più
We live in a world where data is constantly multiplying. According to IDC, the global datasphere, which is the amount[…]
Leggi di più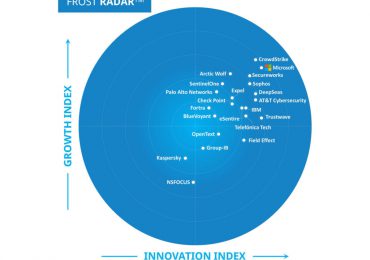
We are excited to share that Microsoft has been named a Leader by Frost & Sullivan in the Frost Radar™:[…]
Leggi di più
The potential for AI at work is practically endless—and understanding how your teams can accomplish more with generative AI is[…]
Leggi di più