At this year’s Microsoft Security Excellence Awards, we took a journey through the evolution of cybersecurity from the 1950s to[…]
Leggi di più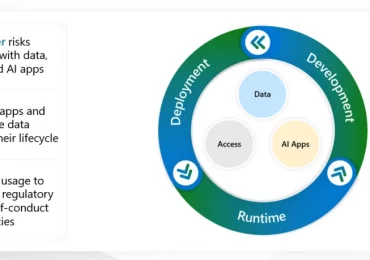
AI is transforming our world, unlocking new possibilities to enhance human abilities and to extend opportunities globally. At the same[…]
Leggi di più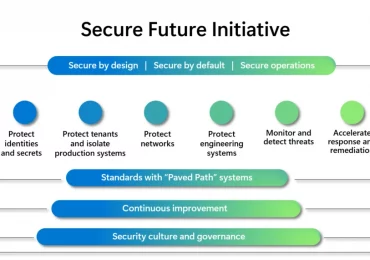
Last November, we launched the Secure Future Initiative (SFI) to prepare for the increasing scale and high stakes of cyberattacks.[…]
Leggi di più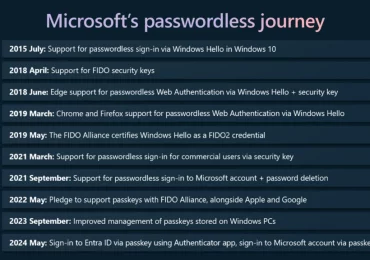
Ten years ago, Microsoft envisioned a bold future: a world free of passwords. Every year, we celebrate World Password Day[…]
Leggi di più
Microsoft discovered a path traversal-affiliated vulnerability pattern in multiple popular Android applications that could enable a malicious application to overwrite[…]
Leggi di piùThe post Investigating industrial control systems using Microsoft’s ICSpector open-source framework appeared first on Microsoft Security Blog. Source: Microsoft[…]
Leggi di più
The cloud security market continues to evolve, reflecting the diligent efforts of security professionals globally. They are at the forefront[…]
Leggi di più
There’s an increasing demand for skilled cybersecurity professionals. It’s being driven by a surge in cyberthreats and more sophisticated attackers.[…]
Leggi di piùMicrosoft Threat Intelligence is publishing results of our longstanding investigation into activity by the Russian-based threat actor Forest Blizzard (STRONTIUM)[…]
Leggi di più
Leading organizations worldwide are harnessing Microsoft Power Platform to revolutionize their operations, with 33 million monthly active users driving innovation[…]
Leggi di piùAttackers are constantly seeking new vulnerabilities to compromise Kubernetes environments. Microsoft recently uncovered an attack that exploits new critical vulnerabilities[…]
Leggi di più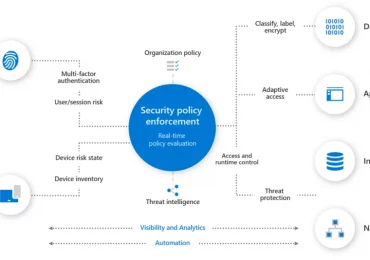
The Department of Defense (DoD) Zero Trust Strategy1 and accompanying execution roadmap2 sets a path for achieving enterprise-wide target-level Zero[…]
Leggi di più