At Microsoft Inspire 2023, we celebrate our partners and thank them for their innovation, contributions, and support over the past[…]
Leggi di più
Cybersecurity is one of the most pressing challenges of our time. With an ever-changing threat landscape and siloed data across[…]
Leggi di piùOn July 18, 2023, we published the 2023 release wave 2 plans for Microsoft Dynamics 365 and Microsoft Power Platform, a compilation of new capabilities[…]
Leggi di piùExecutive summary On July 11, 2023, Microsoft published two blogs detailing a malicious campaign by a threat actor tracked as[…]
Leggi di più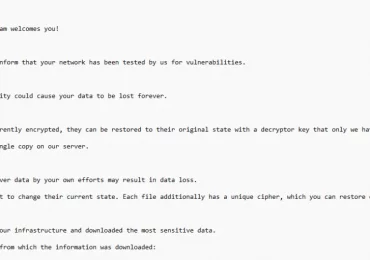
Microsoft has identified a phishing campaign conducted by the threat actor tracked as Storm-0978 targeting defense and government entities in[…]
Leggi di più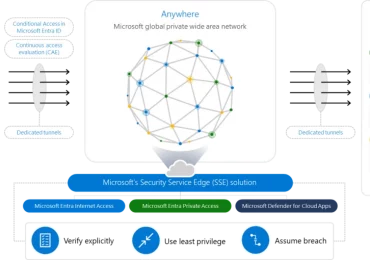
A year ago when we announced the Microsoft Entra product family, we asked what the world could achieve if we[…]
Leggi di più
We know customers of every size face ever-increasing security risks. In just the last 12 months the speed of attackers[…]
Leggi di più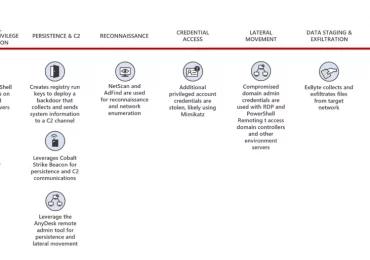
As ransomware attacks continue to grow in number and sophistication, threat actors can quickly impact business operations if organizations are[…]
Leggi di più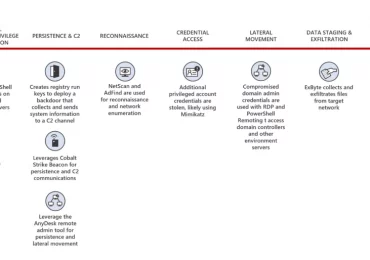
As ransomware attacks continue to grow in number and sophistication, threat actors can quickly impact business operations if organizations are[…]
Leggi di più
Microsoft security researchers tracked a 130.4 percent increase in organizations that have encountered ransomware over the last year. Endpoints are[…]
Leggi di più
Microsoft security researchers tracked a 130.4 percent increase in organizations that have encountered ransomware over the last year. Endpoints are[…]
Leggi di più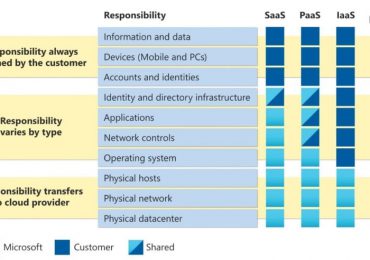
In today’s digital age, cloud computing has become an essential part of businesses, enabling them to store and access their[…]
Leggi di più