
Since we first introduced Microsoft Security Experts in May 2022, we’ve worked hard to expand our new security services category.[…]
Leggi di più
AI is here, and it’s ready to support work. On complex challenges like analyzing troves of data, speeding up time-consuming[…]
Leggi di più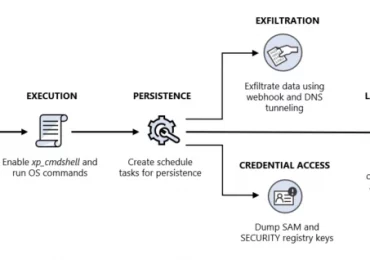
Microsoft security researchers recently identified a campaign where attackers attempted to move laterally to a cloud environment through a SQL[…]
Leggi di più
Welcome to the second Microsoft Power Platform Conference! Since the first conference, there has been a seismic shift in how[…]
Leggi di più
This year marks the twentieth anniversary of Cybersecurity Awareness Month, when we partner with the National Cybersecurity Alliance, the United[…]
Leggi di più
During the past few years, we’ve managed a lot of change and disruption in our security work, in our lives,[…]
Leggi di più
While attacks are getting more sophisticated, so are our defenses. With recent innovations like secured-core PCs that are 60 percent[…]
Leggi di piùToday marks an exciting milestone in Microsoft’s AI journey. This morning, at an event in New York City, we made[…]
Leggi di più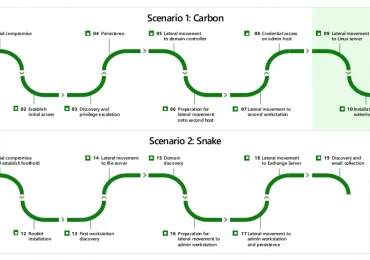
For the fifth consecutive year, Microsoft 365 Defender demonstrated industry-leading extended detection and response (XDR) capabilities in the independent MITRE[…]
Leggi di più
Microsoft is proud to be recognized as a Leader in the Forrester Wave™: Zero Trust Platform Providers, Q3 2023 report.[…]
Leggi di più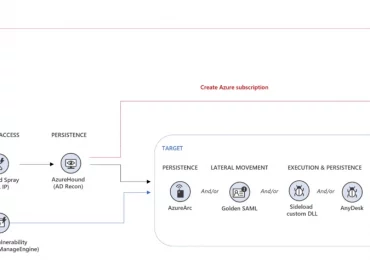
Since February 2023, Microsoft has observed password spray activity against thousands of organizations carried out by an actor we track[…]
Leggi di più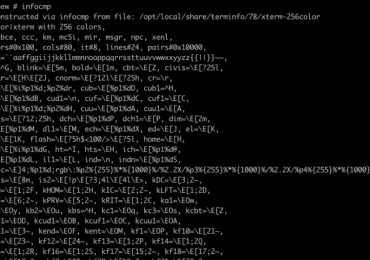
Microsoft has discovered a set of memory corruption vulnerabilities in a library called ncurses, which provides APIs that support text-based[…]
Leggi di più