
There’s no doubt we are living through a time of rapid technological change. Advances in ubiquitous computing and ambient intelligence[…]
Leggi di più
In a world where the digital frontier is expanding and cyberattacks are becoming more sophisticated with speed and scale, the[…]
Leggi di più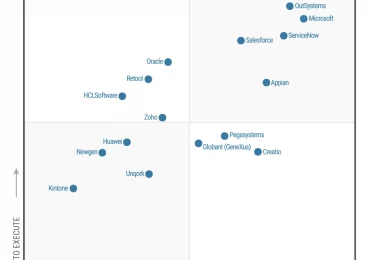
Source: Gartner (August 2023)* We are thrilled to announce that for the fifth time in a row, Microsoft has been[…]
Leggi di più
Today Microsoft Incident Response is excited to announce a new collaboration with PwC to expand our joint incident response and[…]
Leggi di più
Microsoft has been tracking activity related to the financially motivated threat actor Octo Tempest, whose evolving campaigns represent a growing[…]
Leggi di più
A whopping 74 percent of organizations recently surveyed experienced at least one data security incident with their business data exposed[…]
Leggi di più
Today, at the Microsoft Business Applications Launch Event, we kicked off the 2023 release wave 2 for Microsoft Dynamics 365[…]
Leggi di più
We are excited to share that Microsoft has been named a Leader in The Forrester Wave™: Endpoint Security, Q4 2023.[…]
Leggi di più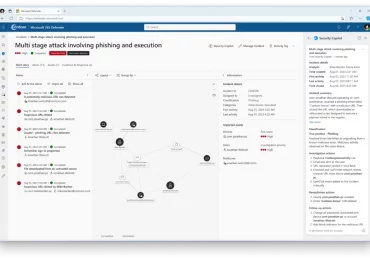
The era of AI brings unprecedented opportunities for us, and at the same time we are also facing an unprecedented[…]
Leggi di più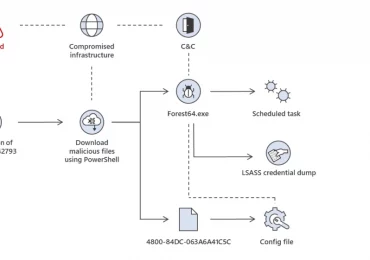
Since early October 2023, Microsoft has observed two North Korean nation-state threat actors – Diamond Sleet and Onyx Sleet –[…]
Leggi di più
Since our announcement in July 2023, we have made significant efforts to enhance the access to Microsoft Purview’s audit logging.1[…]
Leggi di più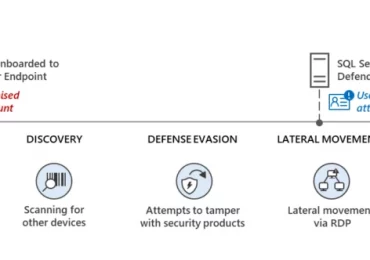
Our experience and insights from real-world incidents tell us that the swift containment of compromised user accounts is key to[…]
Leggi di più