
This year’s Power Platform Community Conference (PPCC 2025) was nothing short of extraordinary. Over 7,000 makers, developers, and partners came[…]
Leggi di più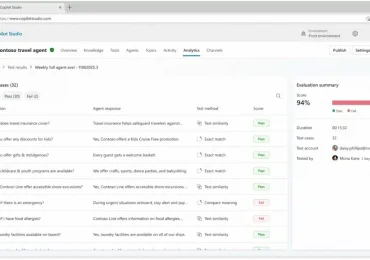
As AI agents take on critical roles in business processes, the need for reliable, repeatable testing becomes essential. In the[…]
Leggi di più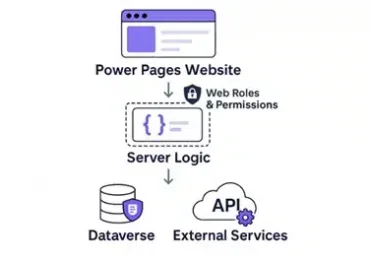
We are happy to announce the new server logic feature in Power Pages to execute business logic securely on the[…]
Leggi di più
As web applications have become central to business operations, securing every line of custom code is more critical than ever.[…]
Leggi di più
In today’s digital-first enterprise, identities have become the new corporate security perimeter. Hybrid work and cloud-first strategies have dissolved traditional[…]
Leggi di più
The latest Microsoft Digital Defense Report 2025 paints a vivid picture of a cyberthreat landscape in flux. The surge in[…]
Leggi di più
On September 30, 2025, Microsoft announced a bold new vision for security: a unified, AI-powered platform designed to help organizations[…]
Leggi di più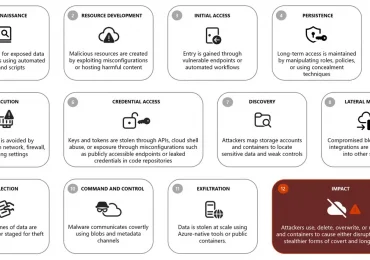
Azure Blob Storage, like any object data service, is a high-value target for threat actors due to its critical role[…]
Leggi di più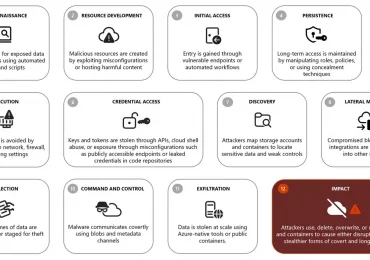
Azure Blob Storage, like any object data service, is a high-value target for threat actors due to its critical role[…]
Leggi di più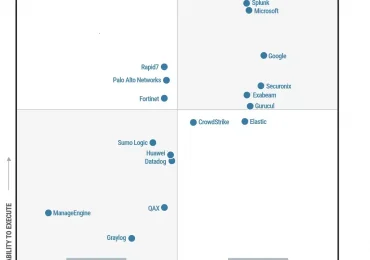
We’re honored to share that Microsoft has again been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for[…]
Leggi di piùIn 80% of the cyber incidents Microsoft’s security teams investigated last year, attackers sought to steal data—a trend driven more[…]
Leggi di più
The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most[…]
Leggi di più