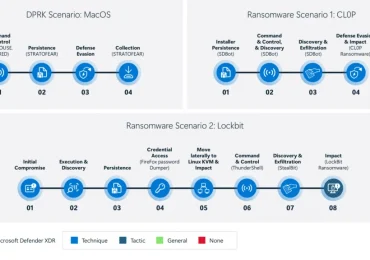
Delivering industry-leading detection for a sixth consecutive year For the sixth year in a row, Microsoft Defender XDR demonstrated industry-leading[…]
Leggi di piùAfter co-opting the tools and infrastructure of another nation-state threat actor to facilitate espionage activities, as detailed in our last[…]
Leggi di più
Security information and event management (SIEM) solutions have long served as the indispensable nerve center for the security operations center[…]
Leggi di più
In mid-October, we released our 2024 Microsoft Digital Defense Report, which revealed over 600 million identity attacks per day. As[…]
Leggi di più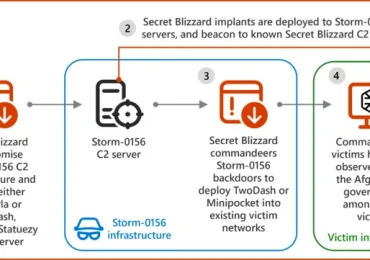
Based on both Microsoft Threat Intelligence’s findings and those reported by governments and other security vendors, we assess that the[…]
Leggi di più
Identity and network access is the foundation of modern cybersecurity, with 66% of attacks involving compromised identities.¹ Equipping identity professionals[…]
Leggi di più
AI transformation starts with security. This was a major theme across the majority of the big news and reveals from[…]
Leggi di più
This year at CYBERWARCON, Microsoft Threat Intelligence analysts are sharing research and insights representing years of threat actor tracking, infrastructure[…]
Leggi di più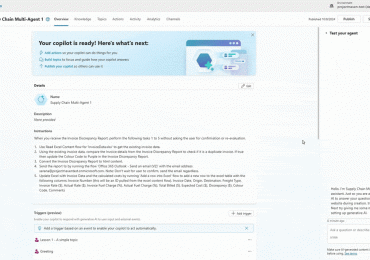
At Microsoft Ignite 2024, it’s incredible to reflect on the transformative journey we’ve had with Microsoft Power Platform. To date,[…]
Leggi di più
In today’s rapidly changing cyberthreat landscape, influenced by global events and AI advancements, security must be top of mind. Over[…]
Leggi di più
Generative AI presents companies of all sizes with opportunities to increase efficiency and drive innovation. With this opportunity comes a[…]
Leggi di più
In 2022, the United States Department of Defense (DoD) released its formal Zero Trust (ZT) Strategy with the goal of[…]
Leggi di più