How implementing a trust fabric strengthens identity and network Read the blog At Microsoft, we’re continually evolving our solutions for[…]
Leggi di più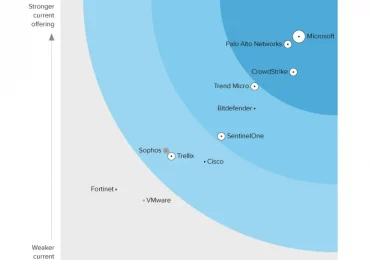
“Defenders think in lists, attackers think in graphs.”1 This remains a reality for the many organizations that operate across siloed[…]
Leggi di più
Since late 2023, Microsoft has observed an increase in reports of attacks focusing on internet-exposed, poorly secured operational technology (OT)[…]
Leggi di più
Multicloud computing has become the foundation for digital businesses, with 86% of organizations having already adopted a multicloud approach.1 However,[…]
Leggi di più
Microsoft has identified a new North Korean threat actor, now tracked as Moonstone Sleet (formerly Storm-1789), that uses both a[…]
Leggi di più
In the ever-evolving landscape of cyberthreats, staying ahead of malicious actors is a constant challenge. Microsoft Threat Intelligence has observed[…]
Leggi di più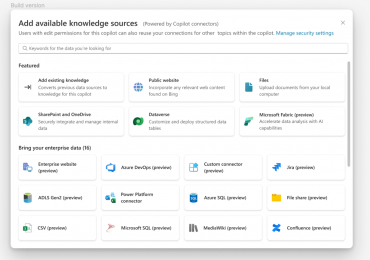
Microsoft Copilot is designed to enhance business productivity by leveraging AI to streamline routine tasks, allowing users to concentrate on[…]
Leggi di più
At Microsoft Build 2024, we’re delivering a new set of features for Copilot that enable organizations to achieve their business[…]
Leggi di più
Ahead of the Microsoft Build 2024 conference, we announced a new class of Windows computers, Copilot+ PC. Alongside this exciting[…]
Leggi di piùSince mid-April 2024, Microsoft Threat Intelligence has observed the threat actor Storm-1811 misusing the client management tool Quick Assist to[…]
Leggi di più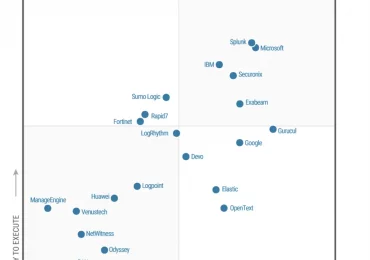
We are pleased to announce that Microsoft has been recognized as a Leader in the Gartner® Magic Quadrant™ for Security[…]
Leggi di più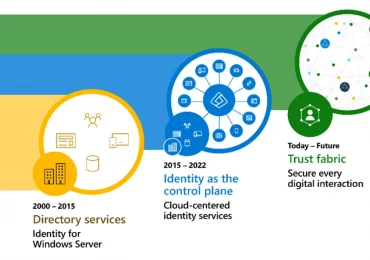
The identity security landscape is transforming rapidly. Every digital experience and interaction is an opportunity for people to connect, share,[…]
Leggi di più