Some IT teams seem like they’re constantly stuck in never-ending loops of repetitive tasks. Day in, day out, they tackle[…]
Leggi di più
We’re announcing new capabilities to help accelerate your transition to a Zero Trust security model with the general availability of[…]
Leggi di piùMicrosoft discovered and responsibly disclosed two vulnerabilities in Rockwell Automation PanelView Plus that could be remotely exploited by unauthenticated attackers,[…]
Leggi di più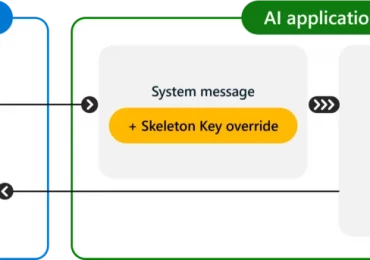
In generative AI, jailbreaks, also known as direct prompt injection attacks, are malicious user inputs that attempt to circumvent an[…]
Leggi di più
I serve on the board of a publicly traded company. I fostered the creation of the board’s cybersecurity committee and[…]
Leggi di più
Innovative organizations worldwide harness Microsoft Power Platform to revolutionize operations and achieve exceptional outcomes. Our customer stories underscore the significant[…]
Leggi di più
Cyberthreats are evolving with alarming sophistication, making it crucial for organizations to react swiftly to incidents and prepare for potential[…]
Leggi di più
Microsoft Defender Experts for XDR demonstrated excellent managed extended detection and response (MXDR) by unifying our human-driven services and Microsoft[…]
Leggi di più
Explore how effective incident response helps organizations detect, address, and stop cyberattacks Learn more As part of any robust incident[…]
Leggi di piùThe post How to achieve cloud-native endpoint management with Microsoft Intune appeared first on Microsoft Security Blog. Source: Microsoft[…]
Leggi di più
In today’s fast-paced digital landscape, enterprise organizations are grappling with an ever-expanding application backlog, with hundreds of millions of new[…]
Leggi di più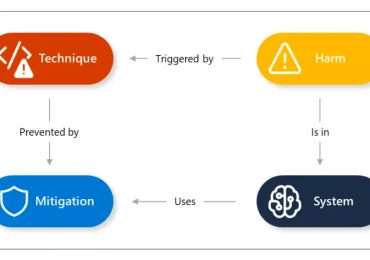
Generative AI systems are made up of multiple components that interact to provide a rich user experience between the human[…]
Leggi di più