Public preview of Azure CNI powered by Cilium using Node Subnet for Linux clusters in AKS is now available. This[…]
Leggi di piùMicrosoft is excited to announce the general availability (GA) of Vaulted Backups by Azure Backup for Azure Database for PostgreSQL[…]
Leggi di piùYou can now develop functions using Python 3.12 locally and deploy them to all Azure Functions plans.Python 3.12 builds on[…]
Leggi di più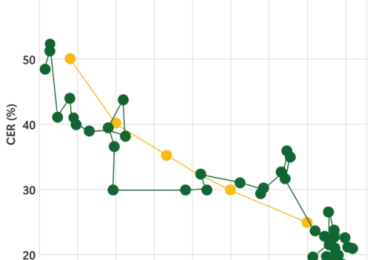
Next time you’re in a public place, stop and look around. Notice how many people are head’s down, staring at their[…]
Leggi di piùAzure Load Testing now allows you to configure notifications to receive updates for key events, such as test completion or[…]
Leggi di più
The keys to success in wealth management are no secret. Research and experience confirm that it comes down to understanding[…]
Leggi di più
The telecommunications industry is experiencing significant AI advancements, emerging as the leading adopter of generative and agentic AI to drive[…]
Leggi di più
Manufacturers around the world grapple with challenges such as fragmented data, inefficient processes, and the need for real-time decision-making directly[…]
Leggi di piùThe Azure Cosmos DB Rust Software Development Kit (SDK) is now in public preview. You can use the Rust SDK[…]
Leggi di piùPostgreSQL minor versions 17.2, 16.6, 15.10, 14.15, 13.18, and 12.22 are now supported by Azure Database for PostgreSQL – Flexible[…]
Leggi di piùEffortlessly migrate your MySQL workloads from on-premises, virtual machines (VMs), or other clouds to Azure Database for MySQL – Flexible[…]
Leggi di piùIn late-February 2025, the following updates and enhancements were made to Azure SQL: Monitor database availability for Azure SQL Database[…]
Leggi di più