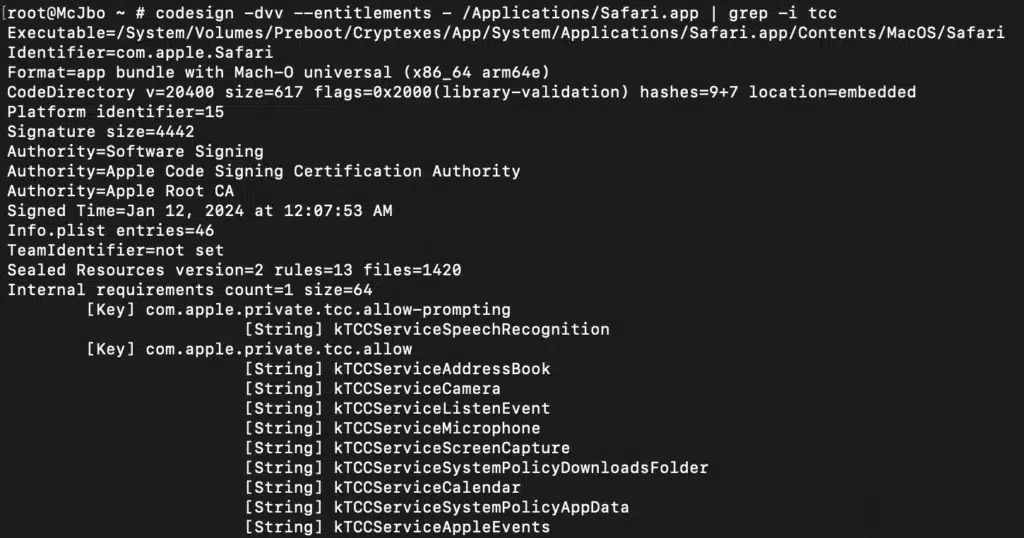
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent, and Control (TCC) technology and gain unauthorized access to a user’s protected data. The vulnerability, which we refer to as “HM Surf”, involves removing the TCC protection for[…]
Read More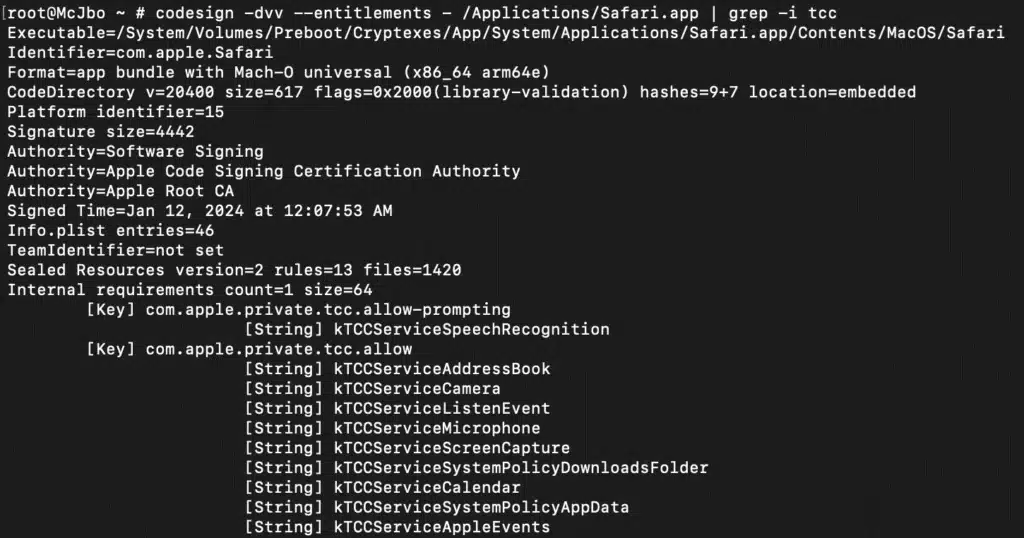
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent, and Control (TCC) technology and gain unauthorized access to a user’s protected data. The vulnerability, which we refer to as “HM Surf”, involves removing the TCC protection for[…]
Read More
Europe’s energy network is facing unprecedented pressure. By 2030, the continent’s energy demand is expected to rise by nearly 20%, while grid flexibility needs will more than double, putting enormous pressure on aging infrastructure.1 As renewable energy integration increases, Europe’s grids will require seven times more flexibility by[…]
Read MoreHi, Microsoft 365 Insiders! My name is Mark Rideout and I’m a Product Manager on the Office AI team. I am excited to share that we’re bringing the Draw and Hold gesture (already available in OneNote) to both Excel and PowerPoint for Windows, making it easier to create[…]
Read More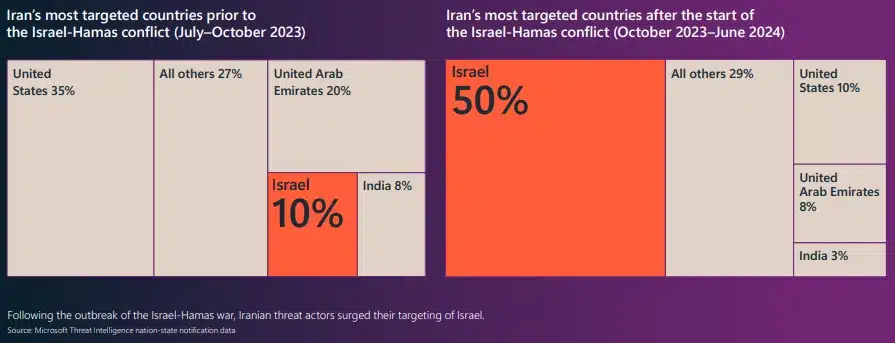
Microsoft customers face more than 600 million cybercriminal and nation-state attacks every day, ranging from ransomware to phishing to identity attacks. Once again, nation-state affiliated threat actors demonstrated that cyber operations—whether for espionage, destruction, or influence—play a persistent supporting role in broader geopolitical conflicts. Also fueling the escalation[…]
Read MoreNotizie per Categorie
Articoli Recenti
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
- [In preview] Private Preview: DCesv6 and ECesv6 series confidential VMs with Intel® TDX 17 Aprile 2025
- [Launched] Generally Available: ExpressRoute Metro Peering locations and Global Reach are now available in more regions 17 Aprile 2025
- [Launched] Generally Available: Azure Front Door custom cipher suite 17 Aprile 2025
- Microsoft’s Secure by Design journey: One year of success 17 Aprile 2025
- [In development] Private Preview: Azure Backup for AKS Now Supports Azure File Share-based Persistent Volumes 16 Aprile 2025
- [In preview] Public Preview: Remote Model Context Protocol (MCP) support in Azure Functions 16 Aprile 2025
