Azure Container Storage is a cloud-based volume management, deployment and orchestration service and works with Azure Kubernetes Service (AKS) to effectively scale across storage services while providing a cost-effective, container-native experience. Cus Source: Microsoft Azure – aggiornamenti
Read MoreGenerative AI is reshaping almost every industry and the legal field is no different. A Thompson Reuters Institute study of legal professionals found “a remarkable 79% of law firm respondents anticipate AI will have a high or transformational impact on their work within the next five years—a significant[…]
Read More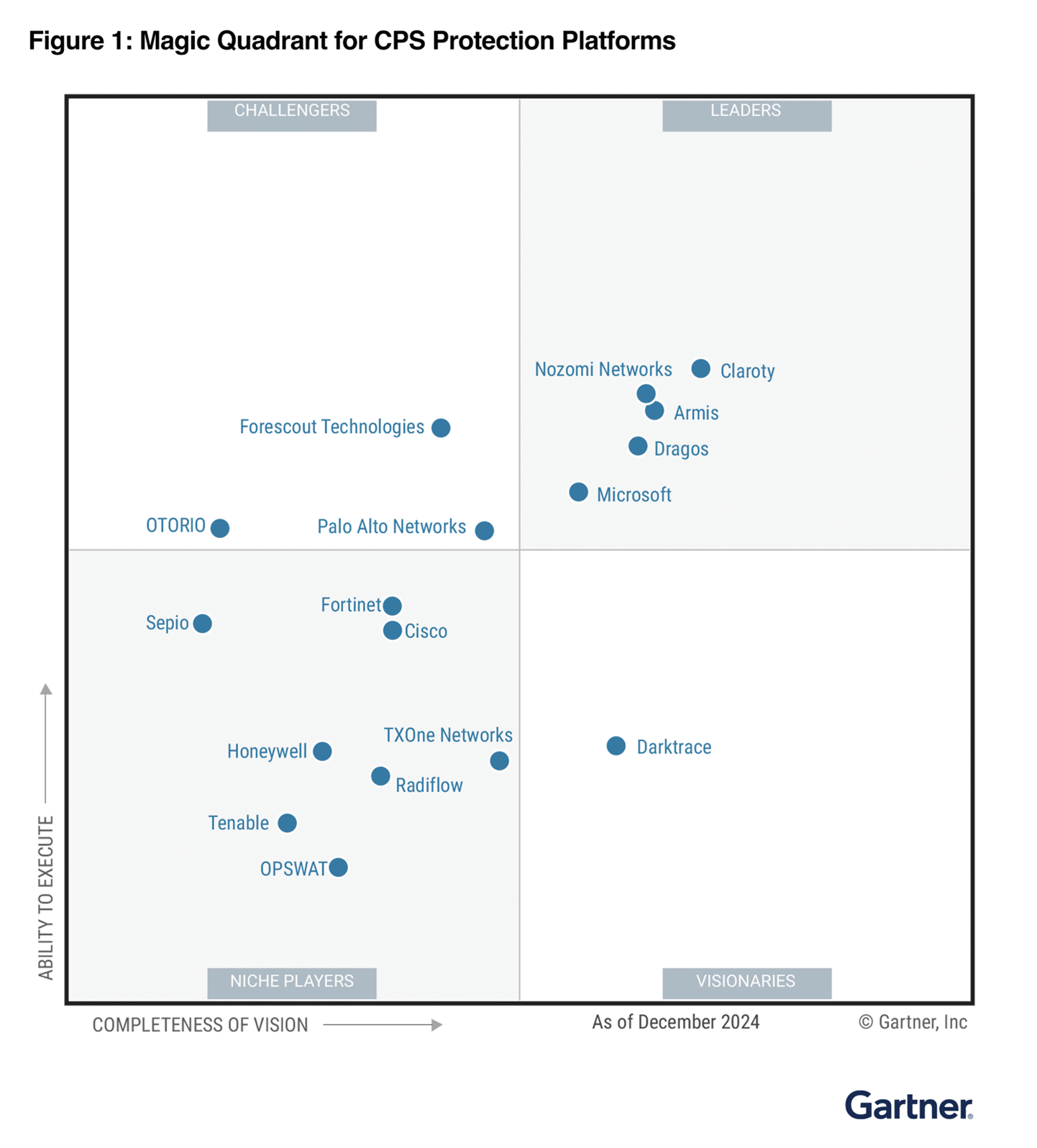
Critical infrastructure is a key target of both physical and cyberattacks. Microsoft has observed an increase in reported attacks on internet-exposed operational technology (OT) devices that control real-world critical processes—like water and wastewater systems, as well as critical functions across industries including healthcare, manufacturing, energy, and more.1 Our[…]
Read MoreThe legal maxim that “justice delayed is justice denied” has long been a rallying cry to encourage judges and courts to operate more efficiently. If legal redress or fair relief are potentially available to an injured party but aren’t promptly provided or supported, that is effectively no remedy[…]
Read More
As generative AI adoption accelerates across the financial services sector, it is important for experts and solution providers to meet customers at their level of understanding. Sharing not just conceptual capabilities but also concrete examples of what this powerful technology can do is essential. Microsoft Cloud for Financial[…]
Read MoreNotizie per Categorie
Articoli Recenti
- Microsoft helps media customers capitalize on AI for greater ROI 2 Aprile 2025
- [In preview] Public Preview: Multi-cluster Eviction and Disruption Budgets with Azure Kubernetes Fleet Manager 2 Aprile 2025
- Microsoft Adaptive Cloud: Advancing edge computing in the defense sector 2 Aprile 2025
- [Launched] Generally Available: Network isolated cluster in AKS 2 Aprile 2025
- [In preview] Public Preview: Multiple Load Balancers for AKS 2 Aprile 2025
- [In preview] Public Preview: Service Allowed IP Ranges in AKS 2 Aprile 2025
- [Launched] Generally Available: Cilium Endpoint Slices in AKS 2 Aprile 2025
- [In preview] Public Preview: Advanced Container Networking Services Cilium L7 Policies Support in AKS 2 Aprile 2025
- [Launched] Generally Available: Azure CNI Node Subnet + Cilium Support 2 Aprile 2025
- [Launched] Generally Available: AKS Cost Recommendations in Azure Advisor 2 Aprile 2025
