If you select a VM SKU that supports Ephemeral OS disks but don’t specify an OS disk size, AKS by default provisions an Ephemeral OS disk with a size that scales according to the total temp storage of the VM SKU so long as the temp is at[…]
Read MoreYou can now monitor your AKS cluster control plane components such as the API server and ETCD using the new Azure platform metrics for control plane. The metrics provide insight into the availability and performance of your managed control plane component Source: Microsoft Azure – aggiornamenti
Read MoreThis feature enables you to check if your network policies allow or disallow traffic between your Azure network resources. There are several moving parts between connectivity, security, routing, and resource-specific configurations — so how do you know wh Source: Microsoft Azure – aggiornamenti
Read MoreIn an era where discovering and rapidly mitigating security vulnerabilities is more important than ever before, the Microsoft Security Response Center (MSRC) is at the center of this work. MSRC focuses on investigating vulnerabilities, coordinating their disclosure, and releasing security updates to help protect customers and Microsoft from[…]
Read More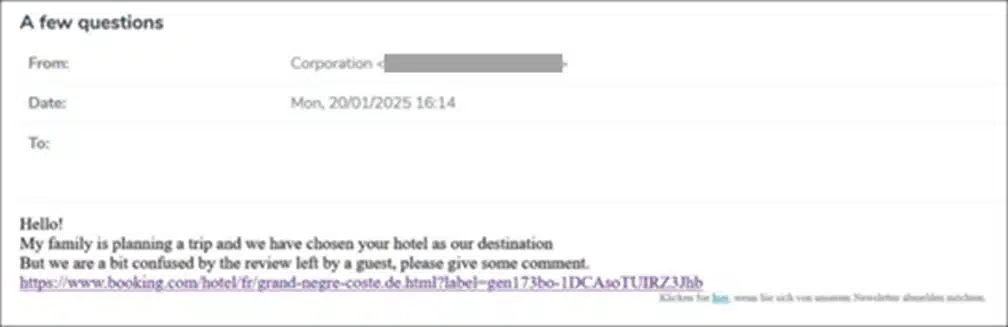
Starting in December 2024, leading up to some of the busiest travel days, Microsoft Threat Intelligence identified a phishing campaign that impersonates online travel agency Booking.com and targets organizations in the hospitality industry. The campaign uses a social engineering technique called ClickFix to deliver multiple credential-stealing malware in[…]
Read MoreNotizie per Categorie
Articoli Recenti
- [Launched] Generally Available: Instance Mix for Virtual Machine Scale Sets 22 Aprile 2025
- [Launched] Generally Available: Announcing the Next generation Azure Data Box Devices 22 Aprile 2025
- [Launched] Generally Available: Cross-Region Data Transfer Capability in Azure Data Box Devices 21 Aprile 2025
- [Launched] Generally Available: Azure Ultra Disk Storage is now available in Spain Central 21 Aprile 2025
- [Launched] Generally Available: Azure Firewall resource specific log tables get Azure Monitor Basic plan support 21 Aprile 2025
- Securing our future: April 2025 progress report on Microsoft’s Secure Future Initiative 21 Aprile 2025
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
