Hi, Microsoft 365 Insiders and Microsoft Word fans! As we look back one year after our 40th anniversary (happy 41st[…]
Read MoreHi, Microsoft 365 Insiders! My name is Greg MacEachern and I’m a Product Manager on the OneNote team. I’m excited[…]
Read More
Now more than ever is the time for every organization to prioritize security. The use of AI by cyberattackers gives[…]
Read More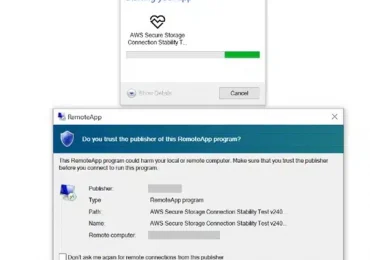
Since October 22, 2024, Microsoft Threat Intelligence has observed Russian threat actor Midnight Blizzard sending a series of highly targeted[…]
Read More
Achieving regulatory compliance and data sovereignty is critical for organizations, particularly within the public sector. As governments and industries with[…]
Read More
We’ve launched 2024 release wave 2 for Microsoft Dynamics 365, Microsoft Power Platform, and role-based Microsoft Copilot offerings—introducing a rollout[…]
Read More