The Azure SQL Migration extension allows offline database migrations of on-premises and cloud SQL Server databases to Azure SQL Database,[…]
Read More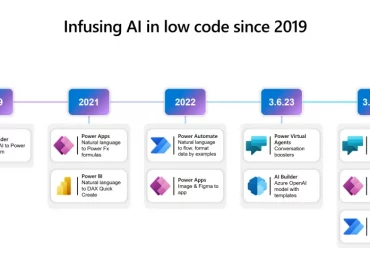
Microsoft Power Platform is reinventing software development with AI-powered no-code development. Today, Microsoft Power Platform is announcing Copilot in Power[…]
Read MoreUse the Azure Database for MySQL – Flexible Server connector to connect to MySQL data and build with Power Apps[…]
Read MoreTake advantage of the features in OpenShift version 4.11. Source: Microsoft Azure – aggiornamenti
Read MoreYou can now use an identity-based connection to access Azure Storage, instead of embedding secrets in connection strings. Source: Microsoft[…]
Read MoreImprove development velocity and efficiency via modern REST and GraphQL API using the new data API builder with support for[…]
Read More