Notizie per Categorie
Articoli Recenti
- Retirement: Canonical Ubuntu 20.04 LTS Reaching End of Standard Support on May 31, 2025 9 Aprile 2025
- Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI 9 Aprile 2025
- [In preview] Public Preview: Power BI Connector for vCore-based Azure Cosmos DB for MongoDB 9 Aprile 2025
- [In preview] Public Preview: Fabric Mirroring for Azure Database for PostgreSQL – flexible server 9 Aprile 2025
- [Launched] Generally Available: Azure SQL Updates for Early-April 2025 9 Aprile 2025
- [Launched] Generally Available: I/O Performance Analysis—SQL Server on Azure Virtual Machines 9 Aprile 2025
- [In preview] Public Preview: Self-serve enablement for all versions and deletes mode in Azure Cosmos DB for NoSQL 9 Aprile 2025
- How cyberattackers exploit domain controllers using ransomware 9 Aprile 2025
- [In preview] Public Preview: New Enhancements to Carbon Optimization – Expanded API limits, Subscription Reader Access, and Filtering Options 8 Aprile 2025
- Exploitation of CLFS zero-day leads to ransomware activity 8 Aprile 2025
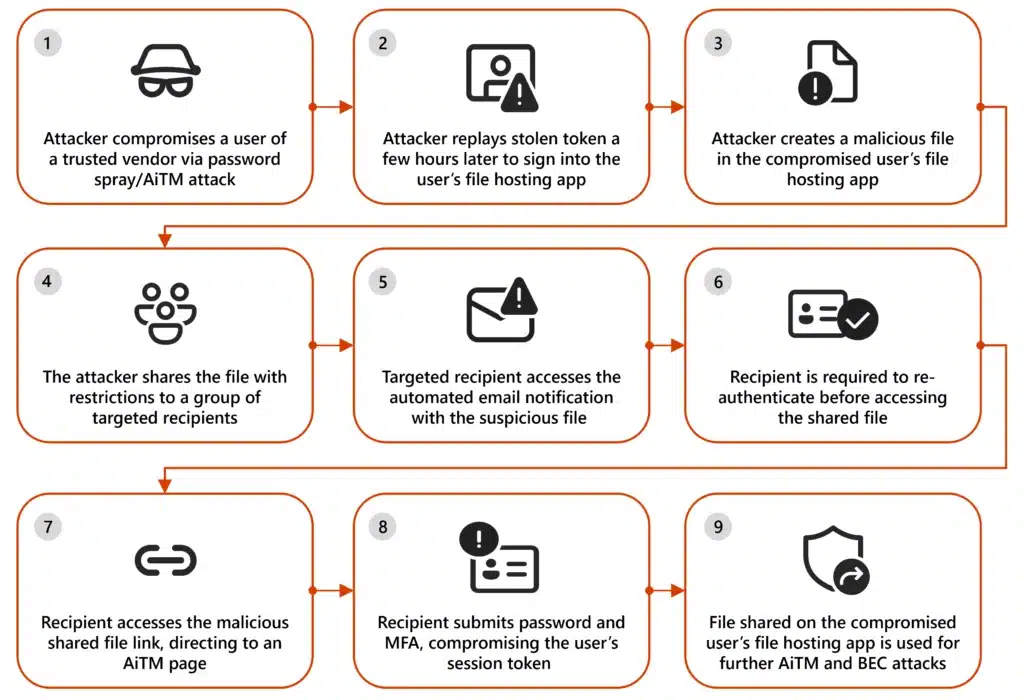
Microsoft has observed campaigns misusing legitimate file hosting services increasingly use defense evasion tactics involving files with restricted access and view-only restrictions. While these campaigns are generic and opportunistic in nature, they involve sophisticated techniques to perform social engineering, evade detection, and expand threat actor reach to other[…]
Read More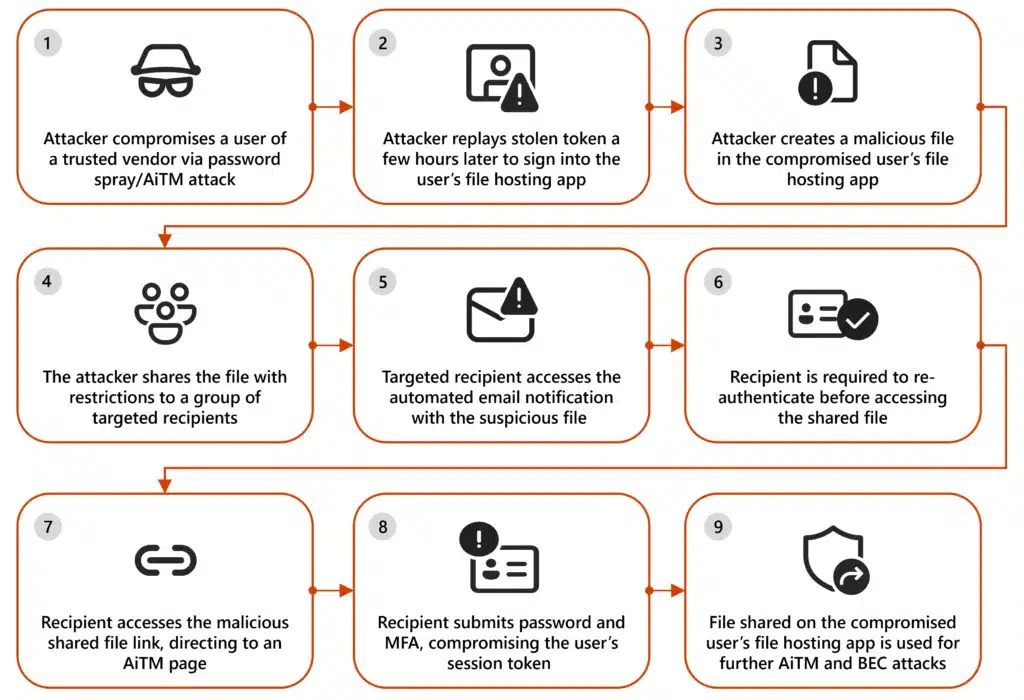
Microsoft has observed campaigns misusing legitimate file hosting services increasingly use defense evasion tactics involving files with restricted access and view-only restrictions. While these campaigns are generic and opportunistic in nature, they involve sophisticated techniques to perform social engineering, evade detection, and expand threat actor reach to other[…]
Read More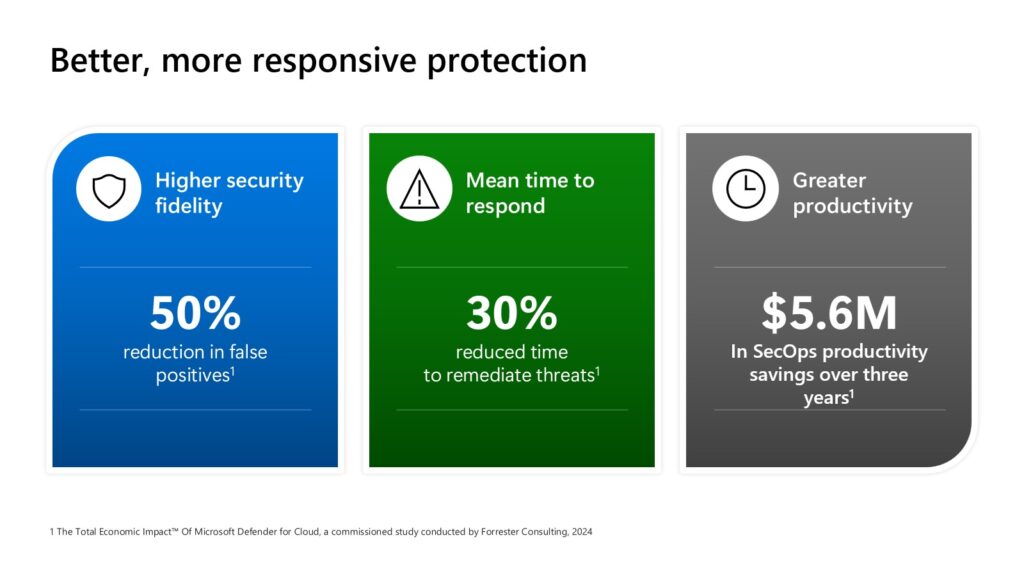
The broad adoption of multicloud and hybrid infrastructures has introduced new complexity to the cloud estates of many businesses. With this complexity comes a broader attack surface for would-be data thieves. Sophisticated ransomware attacks that exploit vulnerabilities in cloud infrastructure are on the rise, as are supply chain[…]
Read More
As Cybersecurity Awareness Month marks its 21st year, it’s clear that this year stands out. Phishing emails have become more convincing, and fraud has increased, making cyberattackers seem legitimate—as if they were Microsoft support or even the fraud detection services from your bank.1 And threat actors are taking[…]
Read More
Microsoft has observed the threat actor tracked as Storm-0501 launching a multi-staged attack where they compromised hybrid cloud environments and performed lateral movement from on-premises to cloud environment, leading to data exfiltration, credential theft, tampering, persistent backdoor access, and ransomware deployment. The said attack targeted multiple sectors in[…]
Read More
Since 2023, Microsoft has seen a 2.75 times increase in the number of organizations encountering ransomware campaigns.1 And up to 90% of successful ransomware campaigns leverage unmanaged endpoints, which are typically personal devices that people bring to work.1 While the number of ransomware attempts has increased drastically, Microsoft[…]
Read More
This week, teams across Microsoft Fabric and Microsoft Purview are gathered in Stockholm, Sweden, for the inaugural European Microsoft Fabric Community Conference. Attendees are in for an immersive experience with 130 sessions, 4 keynotes, 10 workshops, an expo hall, and a vibrant community lounge. The Microsoft Purview team[…]
Read MoreAs AI advances, we all have a role to play to unlock AI’s positive impact for organizations and communities around the world. That’s why we’re focused on helping customers use and build AI that is trustworthy, meaning AI that is secure, safe and private. At Microsoft, we have commitments to ensure Trustworthy AI[…]
Read More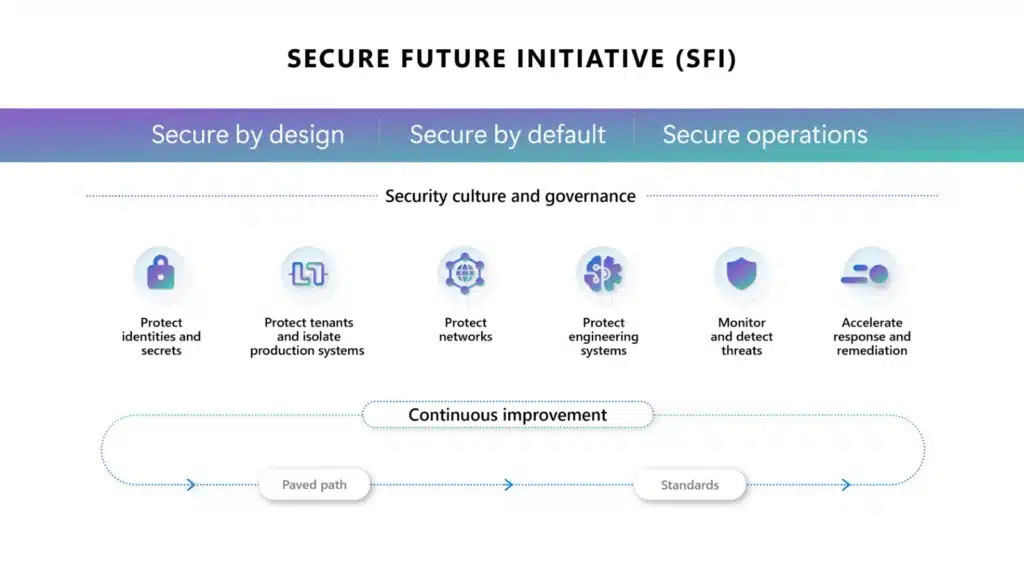
In November 2023, we introduced the Secure Future Initiative (SFI) to advance cybersecurity protection for Microsoft, our customers, and the industry. In May 2024, we expanded the initiative to focus on six key security pillars, incorporating industry feedback and our own insights. Since the initiative began, we’ve dedicated the[…]
Read More
For security professionals and teams, AI offers a significant advantage, empowering organizations of all sizes and industries to tip the scales in favor of defenders. It also introduces new uncertainties and risks that require organizations to create a culture of security to stay protected. Now, more than ever,[…]
Read More