Notizie per Categorie
Articoli Recenti
- Retirement: Canonical Ubuntu 20.04 LTS Reaching End of Standard Support on May 31, 2025 9 Aprile 2025
- Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI 9 Aprile 2025
- [In preview] Public Preview: Power BI Connector for vCore-based Azure Cosmos DB for MongoDB 9 Aprile 2025
- [In preview] Public Preview: Fabric Mirroring for Azure Database for PostgreSQL – flexible server 9 Aprile 2025
- [Launched] Generally Available: Azure SQL Updates for Early-April 2025 9 Aprile 2025
- [Launched] Generally Available: I/O Performance Analysis—SQL Server on Azure Virtual Machines 9 Aprile 2025
- [In preview] Public Preview: Self-serve enablement for all versions and deletes mode in Azure Cosmos DB for NoSQL 9 Aprile 2025
- How cyberattackers exploit domain controllers using ransomware 9 Aprile 2025
- [In preview] Public Preview: New Enhancements to Carbon Optimization – Expanded API limits, Subscription Reader Access, and Filtering Options 8 Aprile 2025
- Exploitation of CLFS zero-day leads to ransomware activity 8 Aprile 2025

We’ve launched 2024 release wave 2 for Microsoft Dynamics 365, Microsoft Power Platform, and role-based Microsoft Copilot offerings—introducing a rollout of new features and enhanced capabilities releasing between October 2024 and March 2025. These updates include advanced Copilot capabilities for Microsoft 365 Copilot for Sales, Copilot for Service,[…]
Read MoreHealthcare organizations are an increasingly attractive target for threat actors. In a new Microsoft Threat Intelligence report, US healthcare at risk: strengthening resiliency against ransomware attacks, our researchers identified that ransomware continues to be among the most common and impactful cyberthreats targeting organizations. The report offers a holistic[…]
Read MoreHealthcare organizations are an increasingly attractive target for threat actors. In a new Microsoft Threat Intelligence report, US healthcare at risk: strengthening resiliency against ransomware attacks, our researchers identified that ransomware continues to be among the most common and impactful cyberthreats targeting organizations. The report offers a holistic[…]
Read More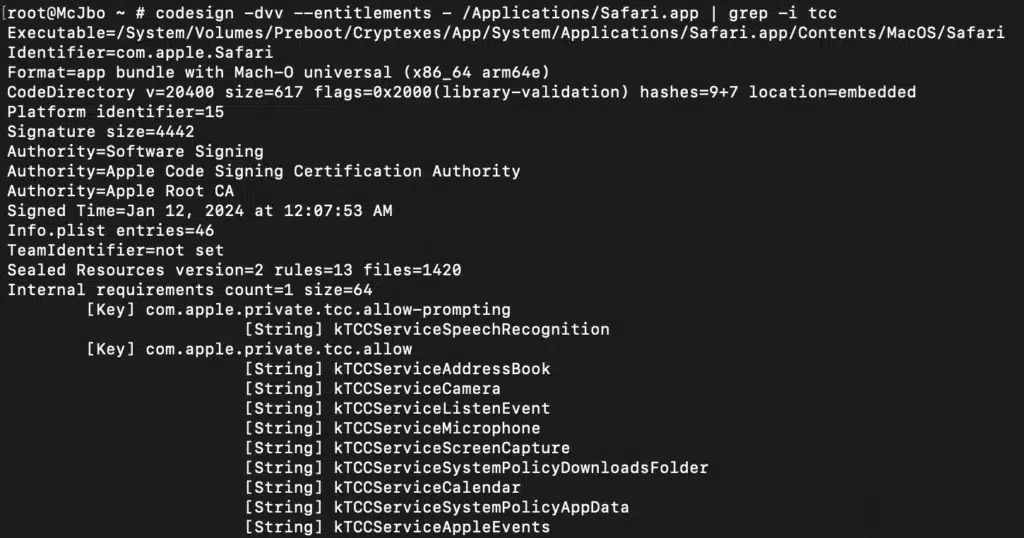
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent, and Control (TCC) technology and gain unauthorized access to a user’s protected data. The vulnerability, which we refer to as “HM Surf”, involves removing the TCC protection for[…]
Read More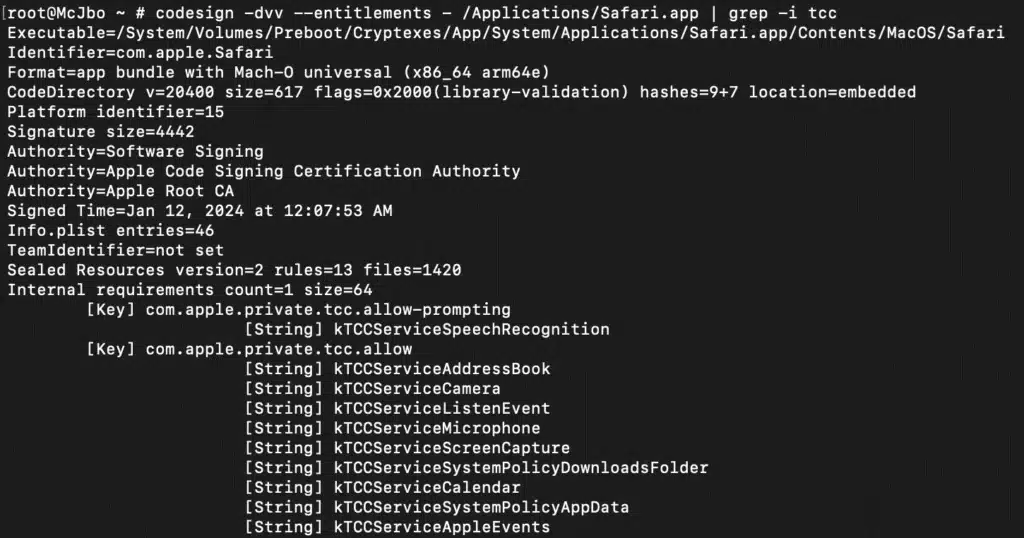
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent, and Control (TCC) technology and gain unauthorized access to a user’s protected data. The vulnerability, which we refer to as “HM Surf”, involves removing the TCC protection for[…]
Read More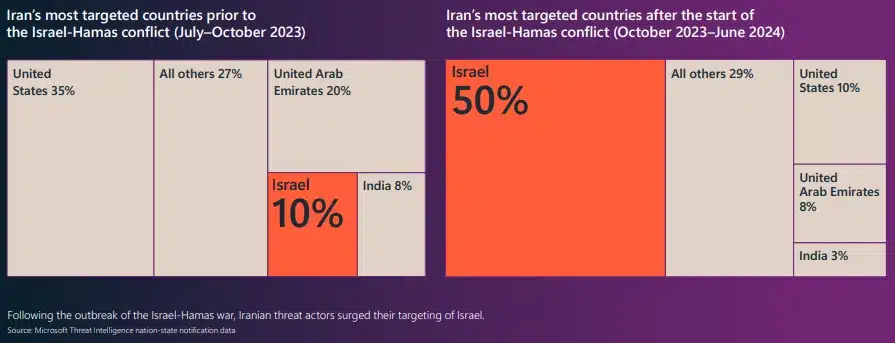
Microsoft customers face more than 600 million cybercriminal and nation-state attacks every day, ranging from ransomware to phishing to identity attacks. Once again, nation-state affiliated threat actors demonstrated that cyber operations—whether for espionage, destruction, or influence—play a persistent supporting role in broader geopolitical conflicts. Also fueling the escalation[…]
Read MoreAs cyberthreats continue to evolve, it’s essential for security professionals to stay informed about the latest attack vectors and defense mechanisms. Kerberoasting is a well-known Active Directory (AD) attack vector whose effectiveness is growing because of the use of GPUs to accelerate password cracking techniques. Because Kerberoasting enables cyberthreat[…]
Read MoreAs cyberthreats continue to evolve, it’s essential for security professionals to stay informed about the latest attack vectors and defense mechanisms. Kerberoasting is a well-known Active Directory (AD) attack vector whose effectiveness is growing because of the use of GPUs to accelerate password cracking techniques. Because Kerberoasting enables cyberthreat[…]
Read More
Introduction | Security snapshot | Threat briefingDefending against attacks | Expert profile Education is essentially an “industry of industries,” with K-12 and higher education enterprises handling data that could include health records, financial data, and other regulated information. At the same time, their facilities can host payment processing[…]
Read More
Introduction | Security snapshot | Threat briefingDefending against attacks | Expert profile Education is essentially an “industry of industries,” with K-12 and higher education enterprises handling data that could include health records, financial data, and other regulated information. At the same time, their facilities can host payment processing[…]
Read More