Notizie per Categorie
Articoli Recenti
- Retirement: Canonical Ubuntu 20.04 LTS Reaching End of Standard Support on May 31, 2025 9 Aprile 2025
- Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI 9 Aprile 2025
- [In preview] Public Preview: Power BI Connector for vCore-based Azure Cosmos DB for MongoDB 9 Aprile 2025
- [In preview] Public Preview: Fabric Mirroring for Azure Database for PostgreSQL – flexible server 9 Aprile 2025
- [Launched] Generally Available: Azure SQL Updates for Early-April 2025 9 Aprile 2025
- [Launched] Generally Available: I/O Performance Analysis—SQL Server on Azure Virtual Machines 9 Aprile 2025
- [In preview] Public Preview: Self-serve enablement for all versions and deletes mode in Azure Cosmos DB for NoSQL 9 Aprile 2025
- How cyberattackers exploit domain controllers using ransomware 9 Aprile 2025
- [In preview] Public Preview: New Enhancements to Carbon Optimization – Expanded API limits, Subscription Reader Access, and Filtering Options 8 Aprile 2025
- Exploitation of CLFS zero-day leads to ransomware activity 8 Aprile 2025
Recent activity from the threat actor that Microsoft tracks as DEV-0569, known to distribute various payloads, has led to the deployment of the Royal ransomware, which first emerged in September 2022 and is being distributed by multiple threat actors. Observed DEV-0569 attacks show a pattern of continuous innovation,[…]
Read More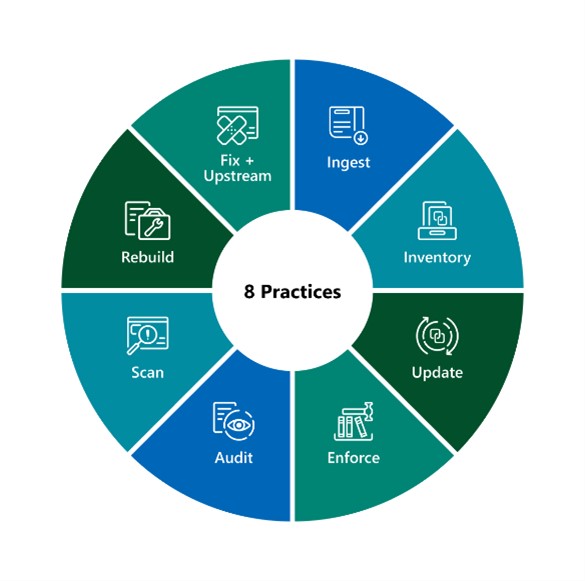
On August 4, 2022, Microsoft publicly shared a framework that it has been using to secure its own development practices since 2019, the Secure Supply Chain Consumption Framework (S2C2F), previously the Open Source Software-Supply Chain Security (OSS-SSC) Framework. As a massive consumer of and contributor to open source,[…]
Read More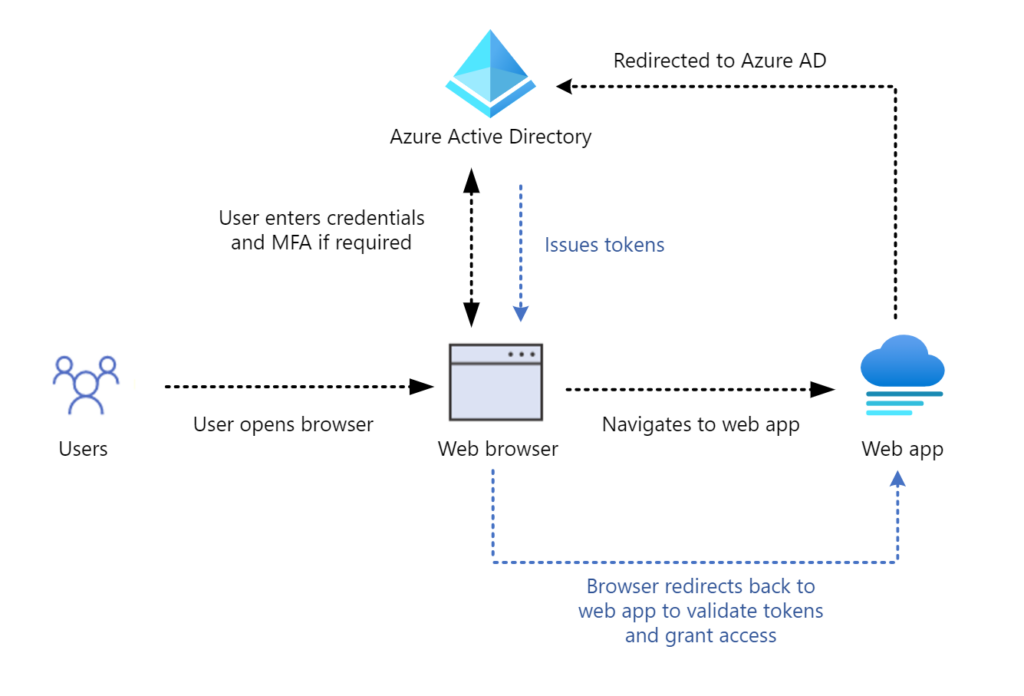
As organizations increase their coverage of multifactor authentication (MFA), threat actors have begun to move to more sophisticated techniques to allow them to compromise corporate resources without needing to satisfy MFA. Recently, the Microsoft Detection and Response Team (DART) has seen an increase in attackers utilizing token theft[…]
Read More
The holiday season is an exciting time for many people as they get to relax, connect with friends and family, and celebrate traditions. Organizations also have much to rejoice about during the holidays (for example, more sales for retailers and more players for gaming companies). Unfortunately, cyber attackers[…]
Read More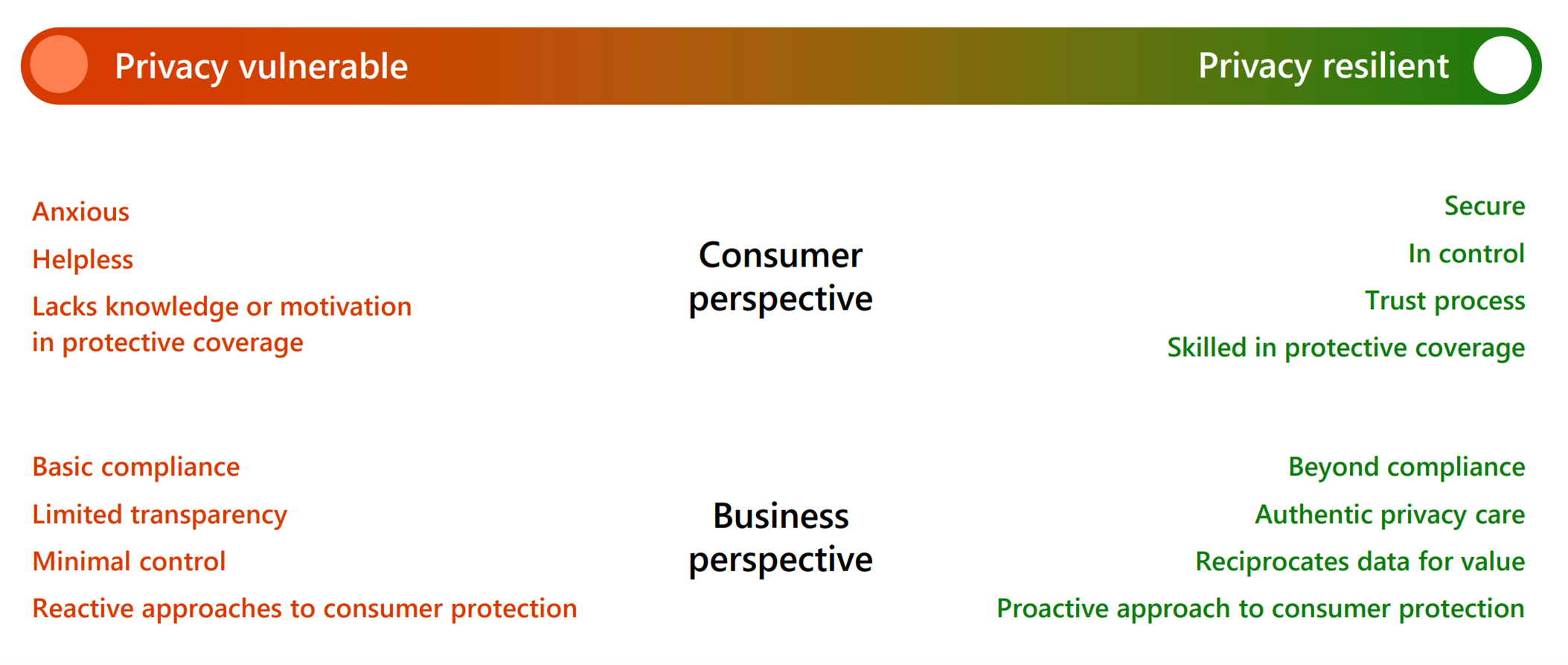
The General Data Protection Regulation (GDPR) came into effect in 2018 and set a new standard for the level of control individuals in the European Union had on the personal data they shared online. Since then, the number of privacy regulations around the world has flourished and impacted[…]
Read More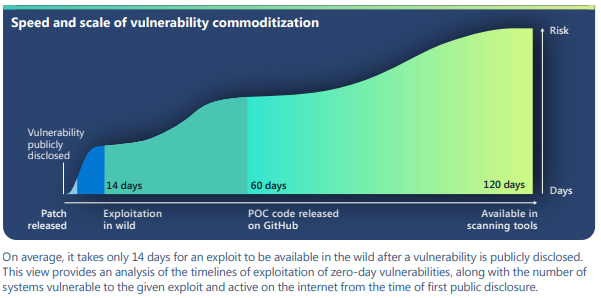
At CyberWarCon 2022, Microsoft and LinkedIn analysts presented several sessions detailing analysis across multiple sets of actors and related activity. This blog is intended to summarize the content of the research covered in these presentations and demonstrates Microsoft Threat Intelligence Center’s (MSTIC) ongoing efforts to track threat actors,[…]
Read More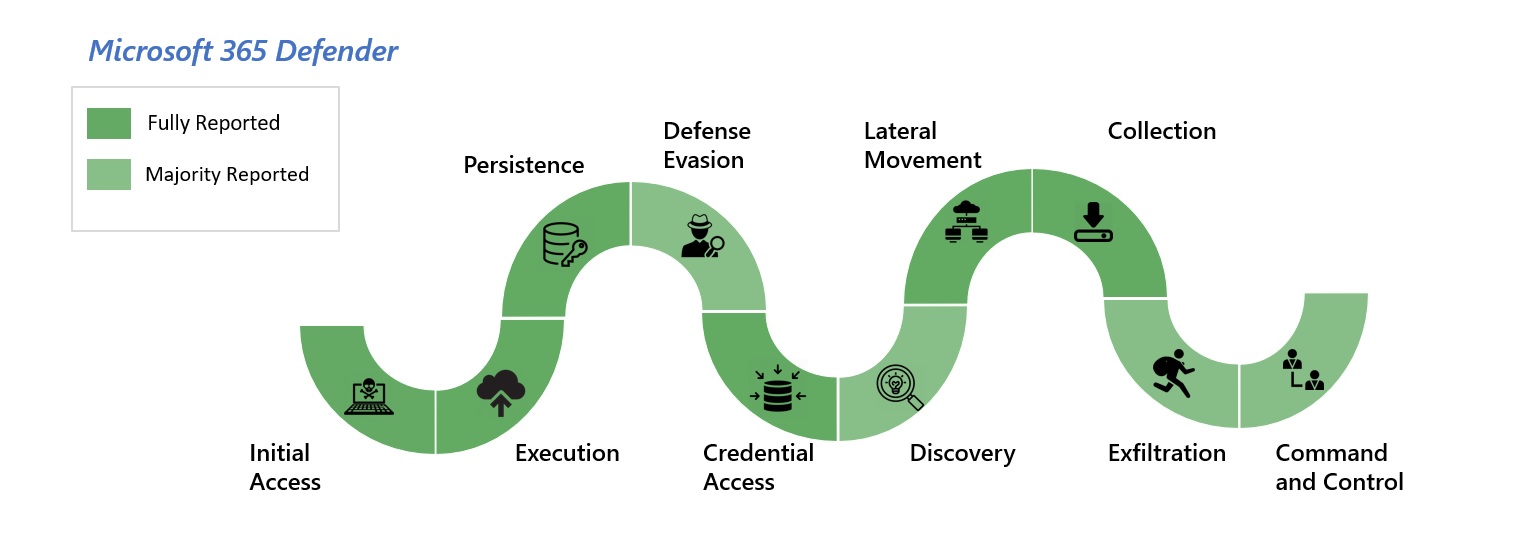
Microsoft Defender Experts for Hunting, our newest managed threat hunting service, delivered industry-leading results during the inaugural MITRE Engenuity ATT&CK® Evaluations for Managed Services. We provided a seamless, comprehensive, and rapid response to the simulated attack using expert-led threat hunting and an industry-leading extended detection and response (XDR)[…]
Read More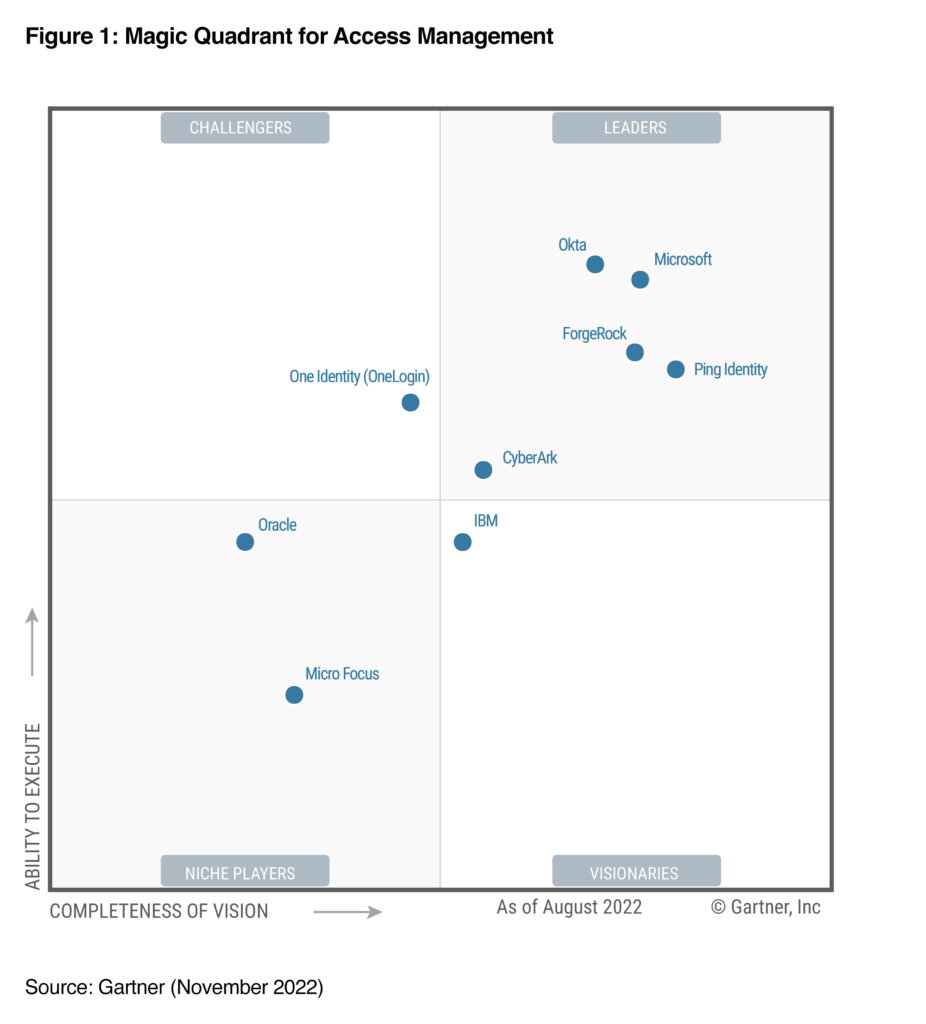
We are honored to announce that Microsoft has been named a Leader in the 2022 Gartner® Magic QuadrantTM for Access Management for Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra. We thank our customers who guide our strategy and product innovation, engage with us deeply in[…]
Read More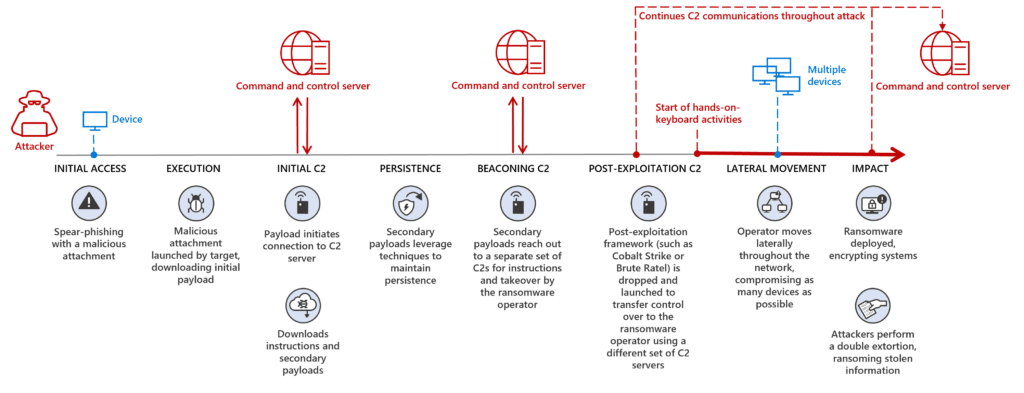
Command-and-control (C2) servers are an essential part of ransomware, commodity, and nation-state attacks. They are used to control infected devices and perform malicious activities like downloading and launching payloads, controlling botnets, or commanding post-exploitation penetration frameworks to breach an organization as part of a ransomware attack. Blocking these[…]
Read MoreThe security community is continuously changing, growing, and learning from each other to better position the world against cyberthreats. In the latest post of our Community Voices blog series, Microsoft Security Senior Product Marketing Manager Brooke Lynn Weenig talks with Matthew Hickey, Co-founder, Chief Executive Officer (CEO), and hacker of Hacker House. The thoughts below[…]
Read More