Notizie per Categorie
Articoli Recenti
- Retirement: Canonical Ubuntu 20.04 LTS Reaching End of Standard Support on May 31, 2025 9 Aprile 2025
- Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI 9 Aprile 2025
- [In preview] Public Preview: Power BI Connector for vCore-based Azure Cosmos DB for MongoDB 9 Aprile 2025
- [In preview] Public Preview: Fabric Mirroring for Azure Database for PostgreSQL – flexible server 9 Aprile 2025
- [Launched] Generally Available: Azure SQL Updates for Early-April 2025 9 Aprile 2025
- [Launched] Generally Available: I/O Performance Analysis—SQL Server on Azure Virtual Machines 9 Aprile 2025
- [In preview] Public Preview: Self-serve enablement for all versions and deletes mode in Azure Cosmos DB for NoSQL 9 Aprile 2025
- How cyberattackers exploit domain controllers using ransomware 9 Aprile 2025
- [In preview] Public Preview: New Enhancements to Carbon Optimization – Expanded API limits, Subscription Reader Access, and Filtering Options 8 Aprile 2025
- Exploitation of CLFS zero-day leads to ransomware activity 8 Aprile 2025
Today, the third edition of Cyber Signals was released spotlighting security trends and insights gathered from Microsoft’s 43 trillion daily security signals and 8,500 security experts. In this edition, we share new insights on wider risks that converging IT, Internet of Things (IoT), and operational technology (OT) systems pose[…]
Read MoreWhat does it mean to be a multicloud organization? As the name implies, the term describes a model of cloud computing where an organization uses multiple clouds—two or more public clouds, private clouds, or a combination of public, private, and edge clouds—to distribute applications and services. Subscribing to[…]
Read More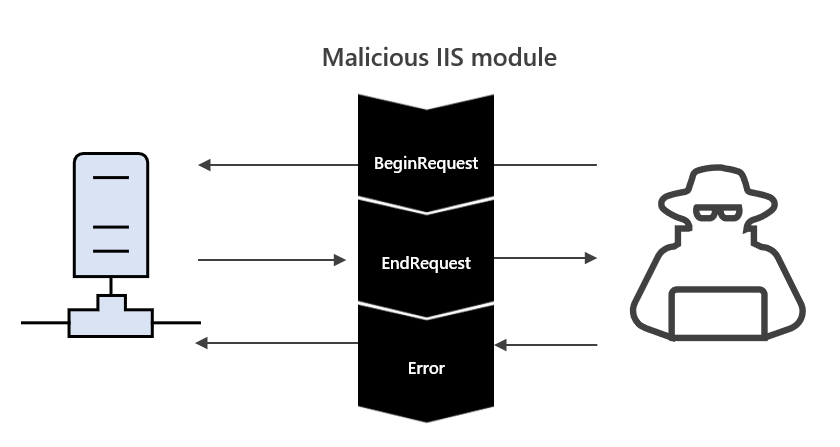
Web exploitation and web shells are some of the most common entry points in the current threat landscape. Web servers provide an external avenue directly into your corporate network, which often results in web servers being an initial intrusion vector or mechanism of persistence. Monitoring for exploitation and[…]
Read More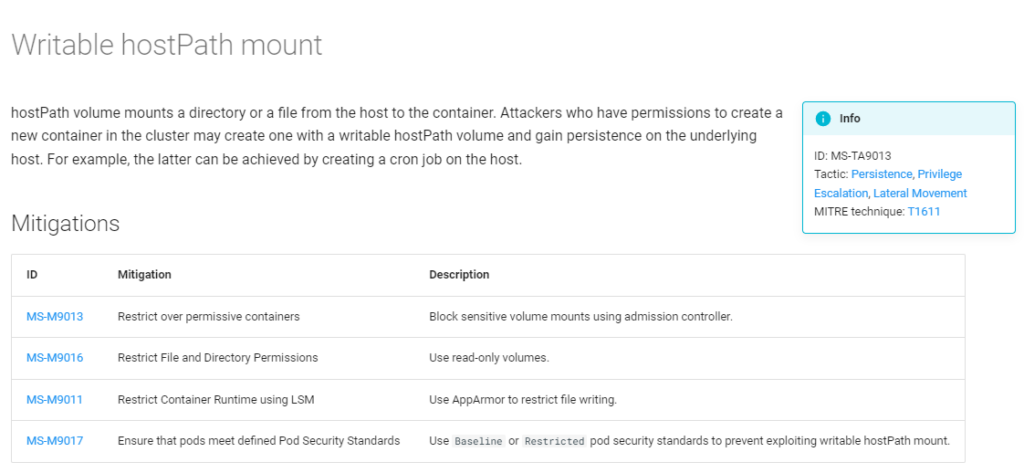
Today, we are glad to release the third version of the threat matrix for Kubernetes, an evolving knowledge base for security threats that target Kubernetes clusters. The matrix, first released by Microsoft in 2020, was the first attempt to systematically cover the attack landscape of Kubernetes. Since then,[…]
Read More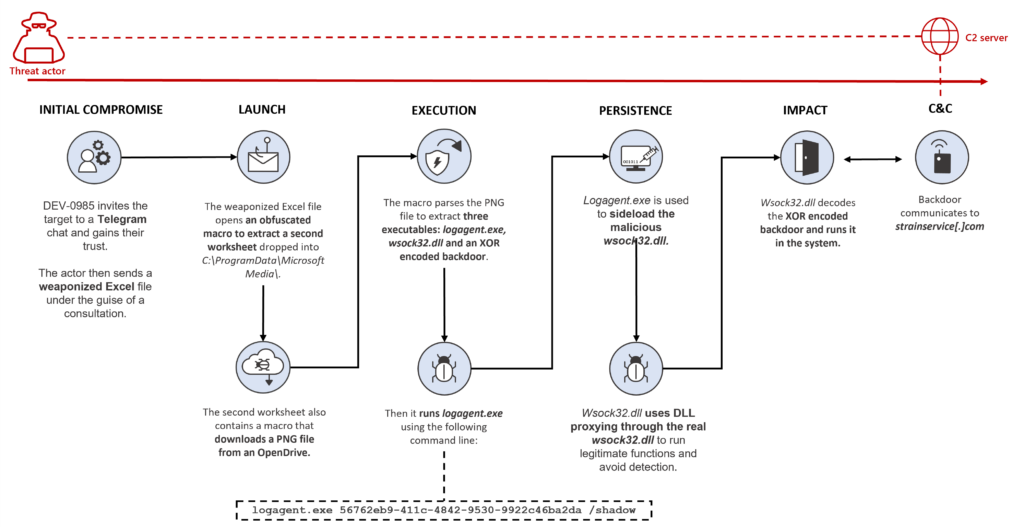
Over the past several years, the cryptocurrency market has considerably expanded, gaining the interest of investors and threat actors. Cryptocurrency itself has been used by cybercriminals for their operations, notably for ransom payment in ransomware attacks, but we have also observed threat actors directly targeting organizations within the[…]
Read More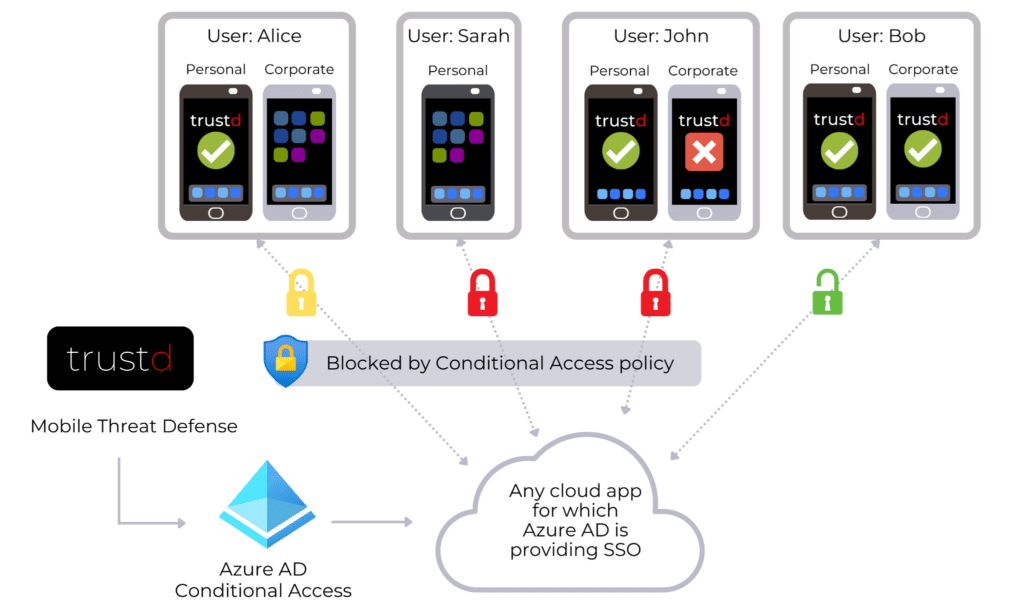
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. As more employees work remotely on a variety of devices and networks, businesses need a security model that supports this new operational efficiency. An expanding perimeter poses challenges for organizational security, exposing[…]
Read More
Microsoft Power Platform recently commissioned a Forrester Total Economic Impact study to help customers better understand the value of Microsoft Power Platform premium capabilities. This study expounds on how premium capabilities empower enterprises to unlock more business value using the platform.The study accomplishes this by highlighting three key[…]
Read More
The Department of Defense (DoD) released its formal Zero Trust strategy today, marking a major milestone in its goal of achieving enterprise-wide implementation by 2027. The strategy comes at a critical time as United States government networks continue to face nearly half the global nation-state attacks that occur,[…]
Read More
Notebooks are gaining popularity in InfoSec. Used interactively for investigations and hunting or as scheduled processing jobs, notebooks offer plenty of advantages over traditional security operations center (SOC) tools. Sitting somewhere between scripting/macros and a full-blown development environment, they offer easy entry to data analyses and visualizations that[…]
Read More
Vulnerabilities in network components, architecture files, and developer tools have become increasingly popular attack vectors to gain access into secure networks and devices. External tools and products that are managed by vendors and developers can pose a security risk, especially to targets in sensitive industries. Attacks on software[…]
Read More