Notizie per Categorie
Articoli Recenti
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
- Microsoft named an overall leader in KuppingerCole Leadership Compass for Generative AI Defense 15 Dicembre 2025
- Update: The retirement date for default outbound access has been extended to March 31, 2026. 12 Dicembre 2025
- [In preview] Public Preview: Azure Databricks Dashboard subscriptions now support Microsoft Teams 11 Dicembre 2025
- [Launched] Generally Available: Azure Sphere OS version 25.12 is now available for evaluation 11 Dicembre 2025
- Imposter for hire: How fake people can gain very real access 11 Dicembre 2025
- From awareness to action: Building a security-first culture for the agentic AI era 10 Dicembre 2025
- Clarity in complexity: New insights for transparent email security 10 Dicembre 2025
- Shai-Hulud 2.0: Guidance for detecting, investigating, and defending against the supply chain attack 9 Dicembre 2025
- Shai-Hulud 2.0: Guidance for detecting, investigating, and defending against the supply chain attack 9 Dicembre 2025

The busier security teams get, the harder it can be to understand the full impact of false positives, queue clutter, tool fragmentation, and more. But what is clear—it all adds up to increased fatigue and an increased potential to miss the cyberthreats that matter most. To help security[…]
Read More
Microsoft Incident Response – Detection and Response Team (DART) researchers uncovered a new backdoor that is notable for its novel use of the OpenAI Assistants Application Programming Interface (API) as a mechanism for command-and-control (C2) communications. Instead of relying on more traditional methods, the threat actor behind this[…]
Read More
Generative AI is reshaping the way security teams operate—accelerating threat detection, automating workflows, and enabling scale. But as defenders embrace AI to strengthen their posture, cyberattackers are doing the same to evolve faster than traditional defenses can adapt. Microsoft’s 2025 Digital Threats Report revealed that cyberattackers like Russia,[…]
Read More
Generative AI is reshaping the way security teams operate—accelerating threat detection, automating workflows, and enabling scale. But as defenders embrace AI to strengthen their posture, cyberattackers are doing the same to evolve faster than traditional defenses can adapt. Microsoft’s 2025 Digital Threats Report revealed that cyberattackers like Russia,[…]
Read More
This year’s Power Platform Community Conference (PPCC 2025) was nothing short of extraordinary. Over 7,000 makers, developers, and partners came together to explore the future of innovation, share inspiring stories, and strengthen the bonds that make this community so special. Behind every innovation is a maker, someone who[…]
Read More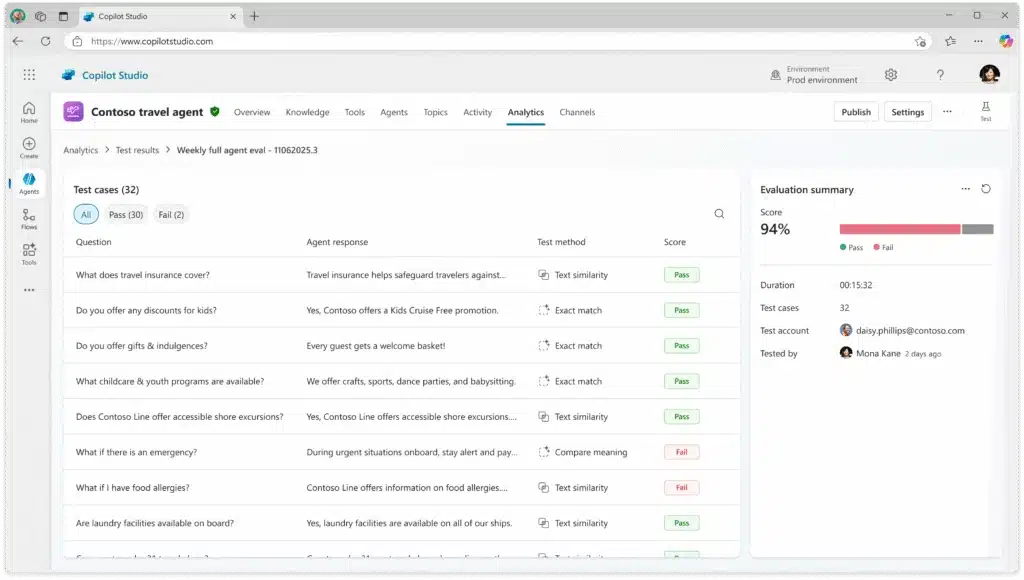
As AI agents take on critical roles in business processes, the need for reliable, repeatable testing becomes essential. In the past, agents have been manually tested—typing in questions, hoping for the right answers, and troubleshooting inconsistencies case by case. That time consuming, unscalable, and inconsistent approach that relies[…]
Read More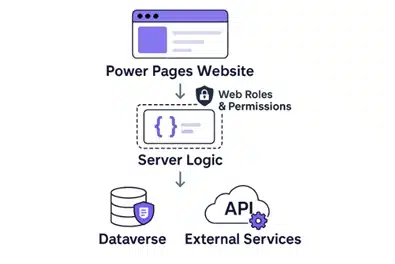
We are happy to announce the new server logic feature in Power Pages to execute business logic securely on the server to build connected, compliant, and intelligent web experiences. Forget the days of jumping through hoops to call external APIs, orchestrate complex actions or securely handle sensitive tasks.[…]
Read More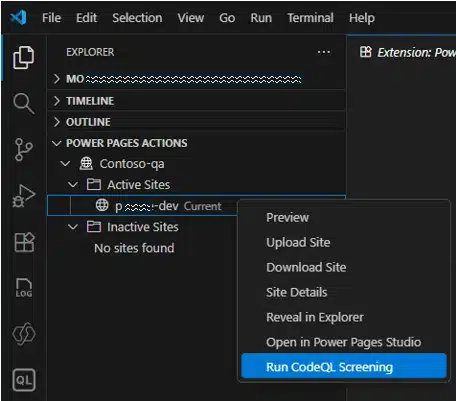
As web applications have become central to business operations, securing every line of custom code is more critical than ever. With the introduction of CodeQL scan in Power Pages toolset, we are empowering developers with static code analysis directly within their development workflow. Why CodeQL Security vulnerabilities can[…]
Read More
In today’s digital-first enterprise, identities have become the new corporate security perimeter. Hybrid work and cloud-first strategies have dissolved traditional network boundaries and dramatically increased the complexity of identity fabrics. Security teams are left managing a constellation of users, infrastructure, and tools scattered across hybrid environments or even[…]
Read More
The latest Microsoft Digital Defense Report 2025 paints a vivid picture of a cyberthreat landscape in flux. The surge in financially motivated cyberattacks and the persistent risk of nation-state actors demand urgent attention. But for those of us in the Office of the Chief Information Security Officer (CISO),[…]
Read More