Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
- [In preview] Private Preview: DCesv6 and ECesv6 series confidential VMs with Intel® TDX 17 Aprile 2025
- [Launched] Generally Available: ExpressRoute Metro Peering locations and Global Reach are now available in more regions 17 Aprile 2025
- [Launched] Generally Available: Azure Front Door custom cipher suite 17 Aprile 2025
- Microsoft’s Secure by Design journey: One year of success 17 Aprile 2025
- [In development] Private Preview: Azure Backup for AKS Now Supports Azure File Share-based Persistent Volumes 16 Aprile 2025
- [In preview] Public Preview: Remote Model Context Protocol (MCP) support in Azure Functions 16 Aprile 2025
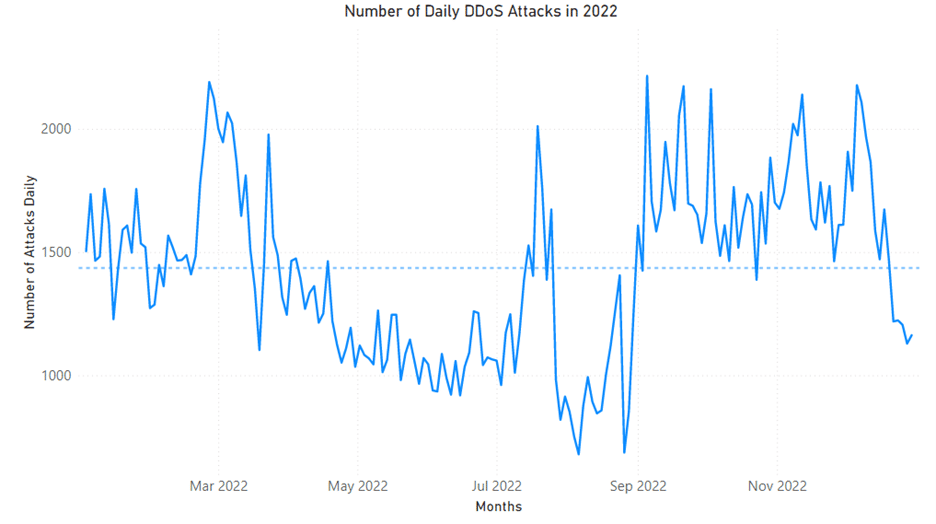
As organizations strengthen their defenses and take a more proactive approach to protection, attackers are adapting their techniques and increasing the sophistication of their operations. Cybercrime continues to rise with the industrialization of the cybercrime economy providing cybercriminals with greater access to tools and infrastructure. In the first[…]
Read More
In today’s world where hybrid and remote work are on the rise, and companies rely on email now more than ever, phishing remains one of the most prominent and sophisticated techniques that malicious actors utilize to attack organizations and gain access to their most sensitive information. Twenty-seven percent[…]
Read More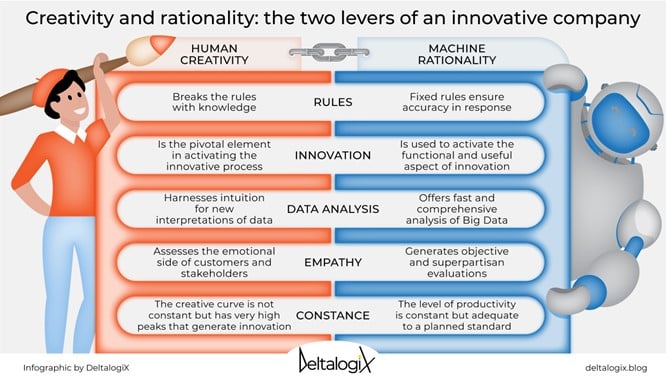
The security community is continuously changing, growing, and learning from each other to better position the world against cyberthreats. In the latest post of our Community Voices blog series, Microsoft Security Senior Product Marketing Manager Brooke Lynn Weenig talks with Linda Grasso, the founder and chief executive officer of DeltalogiX, a blog that provides business leaders with the latest technology news.[…]
Read More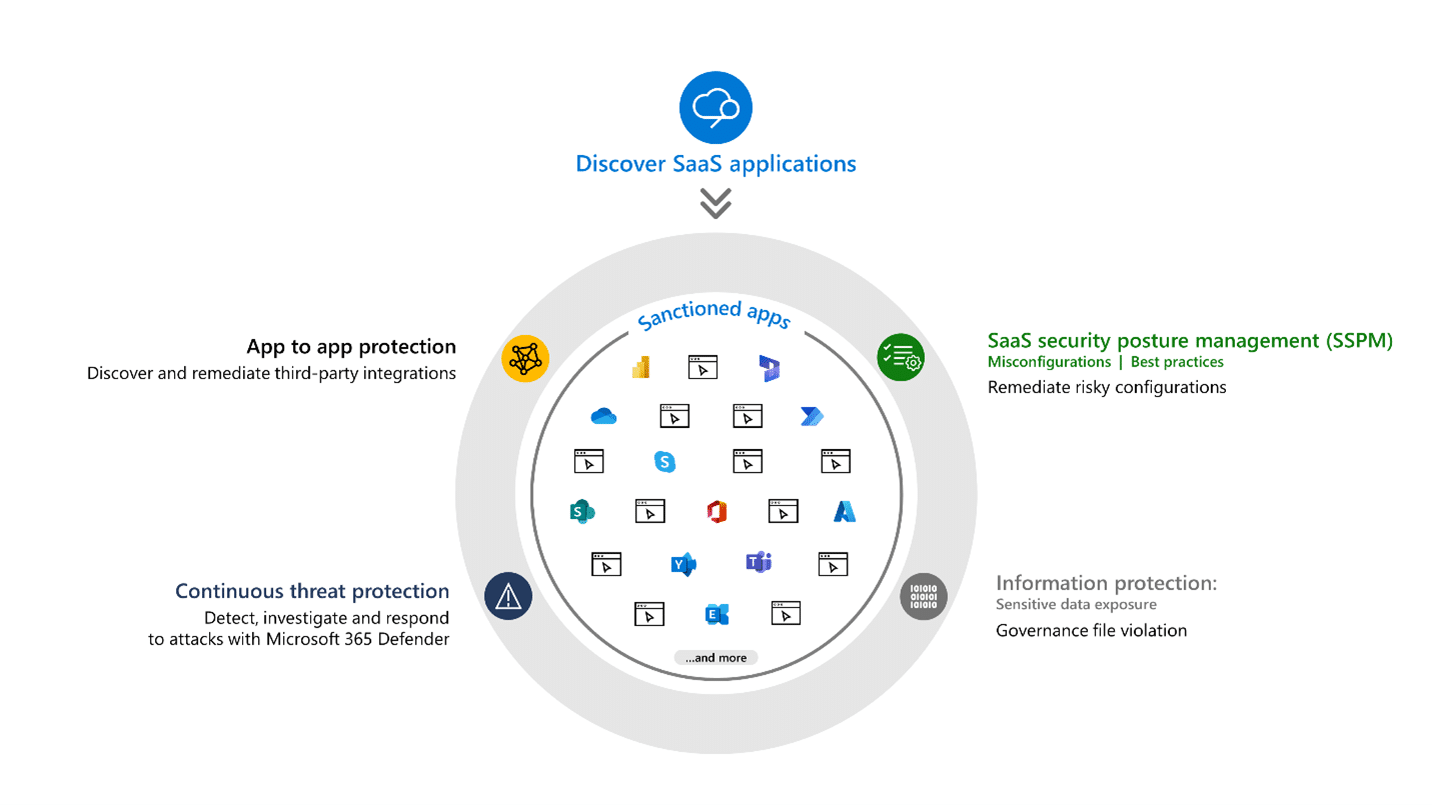
Software as a service (SaaS) apps are ubiquitous, hybrid work is the new normal, and protecting them and the important data they store is a big challenge for organizations. Today, 59 percent of security professionals find the SaaS sprawl challenging to manage1 and have identified cloud misconfigurations as[…]
Read More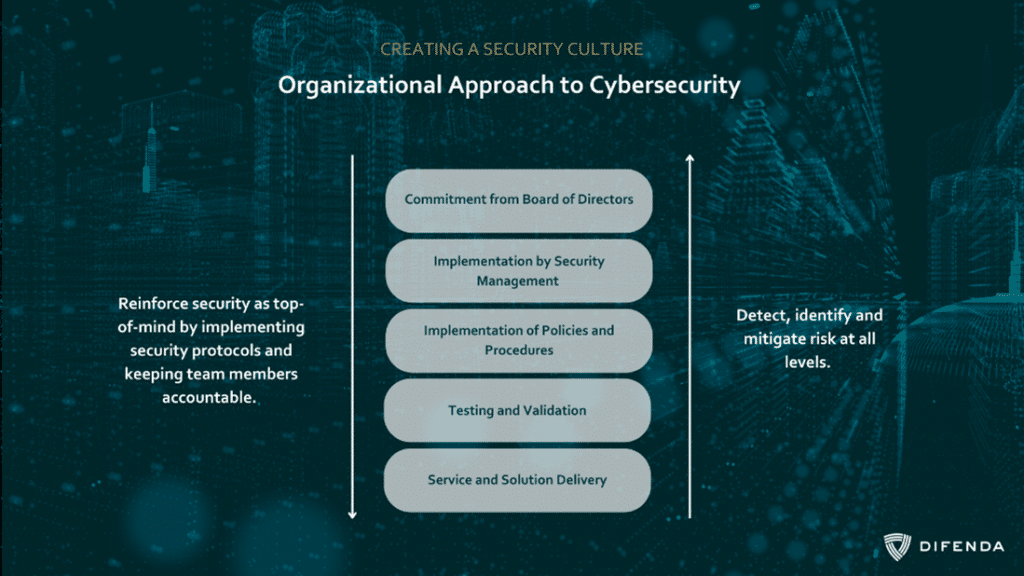
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Cybersecurity is no longer simply a lone silo or regulatory process; it is a business issue that affects every aspect of an organization. From financial losses to reputational damage, the impact of[…]
Read More
Maintaining security across today’s vast digital ecosystem is a team effort. AI and machine learning have helped to detect threats quickly and respond effectively. Yet we all know that the best defense still requires human wisdom and experience. From a frontline security operations admin to the chief information[…]
Read MoreOur story begins with eight Microsoft Detection and Response Team (DART) analysts gathered around a customer’s conference room to solve a cybersecurity mystery. Joined by members of the customer’s cybersecurity team, they were there to figure out how a Russia-based nation-state hacking group known as NOBELIUM had bypassed[…]
Read More
At Microsoft, we never stop working to protect you and your data. If the evolving cyberattacks over the past three years have taught us anything, it’s that threat actors are both cunning and committed. At every level of your enterprise, attackers never stop looking for a way in.[…]
Read MoreAgile and DevOps are without any doubt two of the biggest security trends of recent years. The rapid rise of the cloud has only fueled the need for flexibility and dynamicity. Therefore, it’s natural for developers and organizations to seek methodologies and tools for addressing new requirements faster[…]
Read More
Welcome to 2023! I wanted to kick this year off by having a quick look at the trends in identity security, what you can do about it, and what Microsoft is doing to help you. One of the things we talk about on the team is “shiny object[…]
Read More