Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
- [In preview] Private Preview: DCesv6 and ECesv6 series confidential VMs with Intel® TDX 17 Aprile 2025
- [Launched] Generally Available: ExpressRoute Metro Peering locations and Global Reach are now available in more regions 17 Aprile 2025
- [Launched] Generally Available: Azure Front Door custom cipher suite 17 Aprile 2025
- Microsoft’s Secure by Design journey: One year of success 17 Aprile 2025
- [In development] Private Preview: Azure Backup for AKS Now Supports Azure File Share-based Persistent Volumes 16 Aprile 2025
- [In preview] Public Preview: Remote Model Context Protocol (MCP) support in Azure Functions 16 Aprile 2025

Organizations need to protect their sensitive data including intellectual property, trade secrets, customer data, and personally identifiable information from both insiders and external cyber attackers. In fact, 80 percent of organizations experience more than one data breach in their lifetime.1 With global, industry, and national-level regulations, the need[…]
Read MoreThis blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. You’ve implemented multifactor authentication for access to your enterprise network. But what if multifactor authentication isn’t as foolproof as you’re hoping? Are you comfortable betting your organization’s security on it? Multifactor authentication[…]
Read More
Today, Microsoft announced the successful completion of the Cloud Data Management Capabilities (CDMC) 14 Key Controls and Automations certification, conducted by Accenture and Avanade, accelerating the industry’s move to the cloud. The 14 Key Controls and Automations are a part of the EDM Council’s Cloud Data Management Capabilities[…]
Read More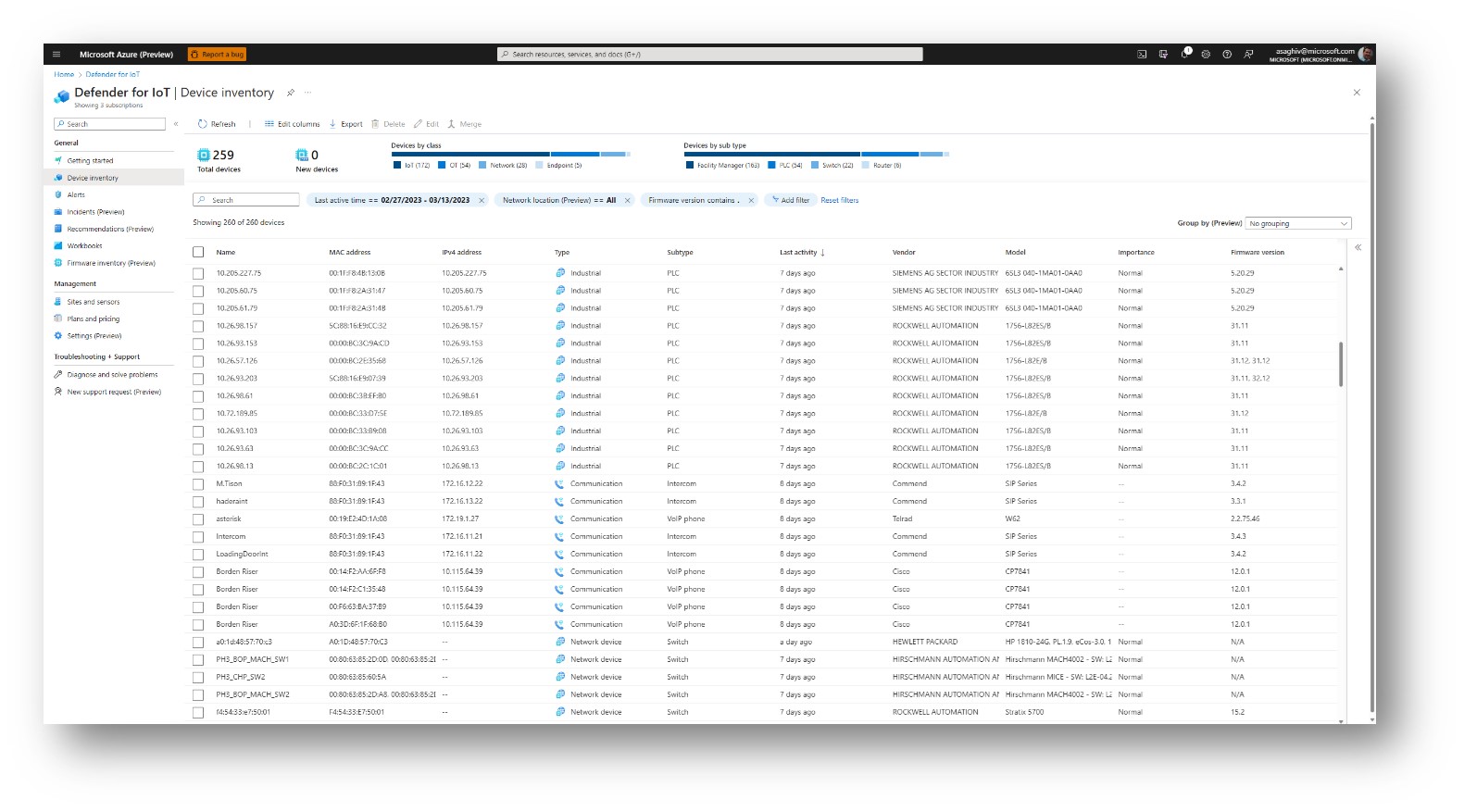
Traditionally, operational technology (OT) and IT have occupied separate sides of enterprise security. But with digital transformation and the advent of Industry 4.0, the old, siloed approach is showing its age.1 The rise of manufacturing execution systems has enabled more “smart factories” to deliver improved manageability and data[…]
Read More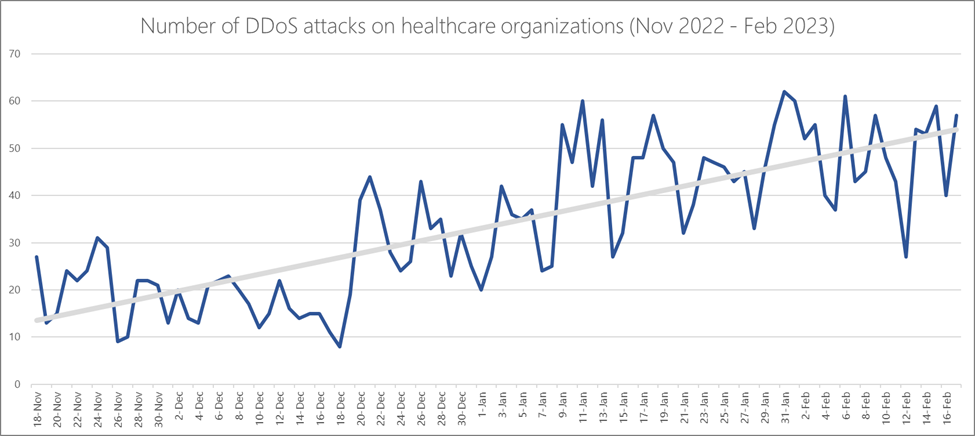
In the last year, geopolitical tension has led to an uptick of reported cybercrime events fueled by hacktivist groups. The US Cybersecurity and Infrastructure Security Agency (CISA) published an advisory to warn organizations about these attacks and teamed with the FBI on a distributed denial-of-service (DDoS) response strategy[…]
Read MoreMicrosoft Secure is our first flagship event designed just for security professionals. On March 28, 2023, we will bring together security professionals from around the world to explore security information and event management (SIEM) and extended detection and response (XDR), threat intelligence, AI, data security, multicloud security, and[…]
Read More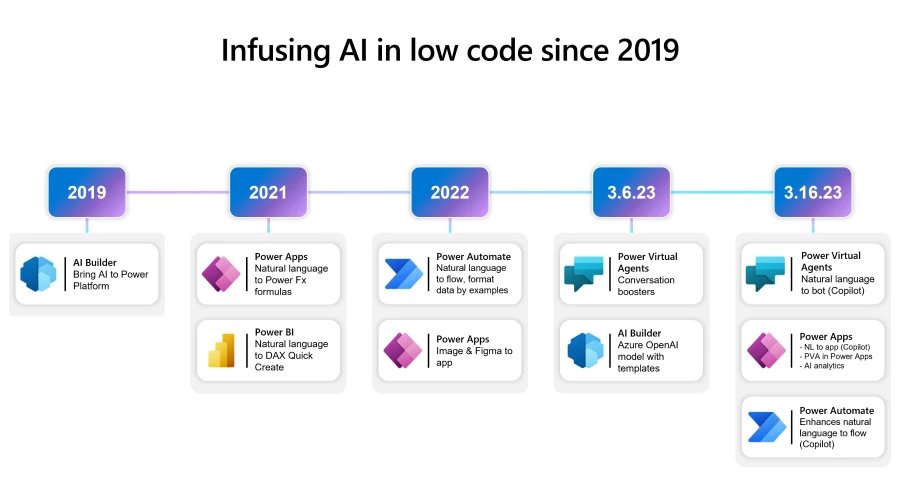
Microsoft Power Platform is reinventing software development with AI-powered no-code development. Today, Microsoft Power Platform is announcing Copilot in Power Apps, Power Automate, and Power Virtual Agents further democratizing development and enabling even more people to create innovative solutions through natural language. Now, if you can imagine your solution,[…]
Read MoreWe’re living in a seismic era for data security. Chief information security officers (CISOs) have to contend with a digital landscape that seems to shift daily as more organizations move to remote and hybrid work, redrawing the boundaries for how data is used and shared. The cloud has[…]
Read More
Adversary-in-the-middle (AiTM) phishing kits are part of an increasing trend that is observed supplanting many other less advanced forms of phishing. AiTM phishing is capable of circumventing multifactor authentication (MFA) through reverse-proxy functionality. DEV-1101 is an actor tracked by Microsoft responsible for the development, support, and advertising of[…]
Read MoreWomen’s History Month is a special time for me as I reflect on all the great innovations women have made over the years. Women have driven technology forward throughout history. Notable women in cybersecurity like cryptologists Agnes Meyer Driscoll and Genevieve Grotjan Feinstein worked behind the scenes of[…]
Read More