Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
- [In preview] Private Preview: DCesv6 and ECesv6 series confidential VMs with Intel® TDX 17 Aprile 2025
- [Launched] Generally Available: ExpressRoute Metro Peering locations and Global Reach are now available in more regions 17 Aprile 2025
- [Launched] Generally Available: Azure Front Door custom cipher suite 17 Aprile 2025
- Microsoft’s Secure by Design journey: One year of success 17 Aprile 2025
- [In development] Private Preview: Azure Backup for AKS Now Supports Azure File Share-based Persistent Volumes 16 Aprile 2025
- [In preview] Public Preview: Remote Model Context Protocol (MCP) support in Azure Functions 16 Aprile 2025
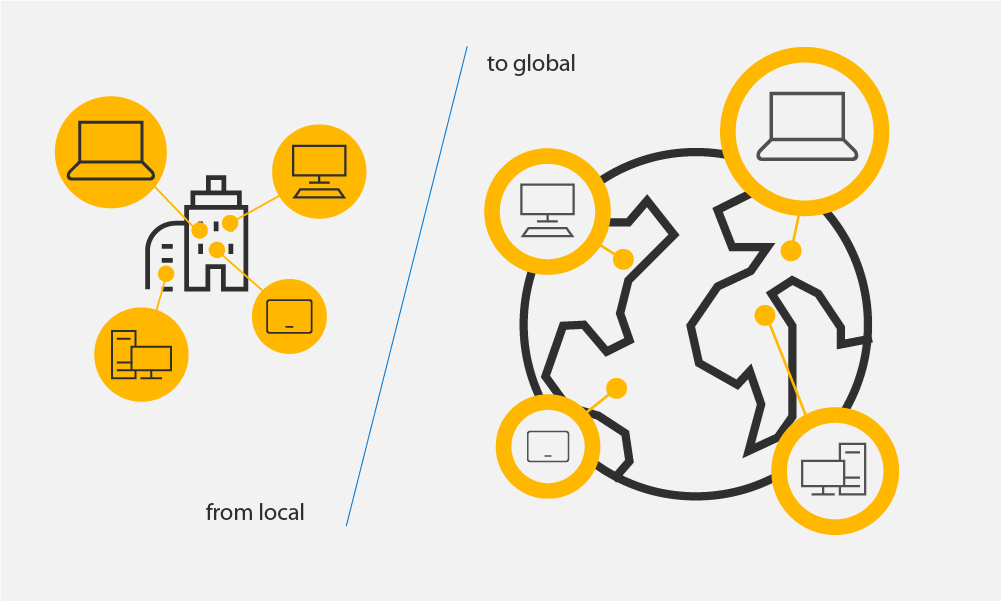
Productivity and innovation have become critical goals in many hybrid and remote work environments. Ensuring preventative and strong security, in turn, must be at the heart of that. In this blog series, we’ll discuss two Zero Trust business scenarios: enabling a more productive hybrid or remote work environment[…]
Read MoreThe post Release wave 1 expands agility, automation, and innovation across Microsoft Dynamics 365 and Power Platform appeared first on Microsoft Power Platform Blog. Source: Microsoft Power Platform
Read More
We’re thrilled to participate and connect with you at RSA Conference 2023 from April 23 to 27, 2023, in San Francisco. Join your security peers as we welcome you to the new era of security—shaped by the power of OpenAI’s GPT-4 generative AI—and introduce to you the recently[…]
Read MoreIf you read behind the attention-grabbing headlines, most novel techniques rely on compromised identities.1 In fact, of all the ways an attacker can get into your digital estate, identity compromise is still the most common.2 This makes identity your first line of defense. In many organizations, however, too[…]
Read More
Building a more secure future requires an end-to-end approach. There is no question that technology plays an essential role, but security will always be human-centered. That’s what Microsoft Secure is all about. It’s about sharing knowledge, best practices, and technology innovations that empower defenders. Microsoft Secure is live[…]
Read MoreThe task of securing organizations is constantly changing and getting more complex. Many organizations don’t have the time, resources, or expertise to build an in-house incident response program. For customers that want help remediating an especially complex breach (or avoiding one altogether), Microsoft Incident Response offers an end-to-end[…]
Read More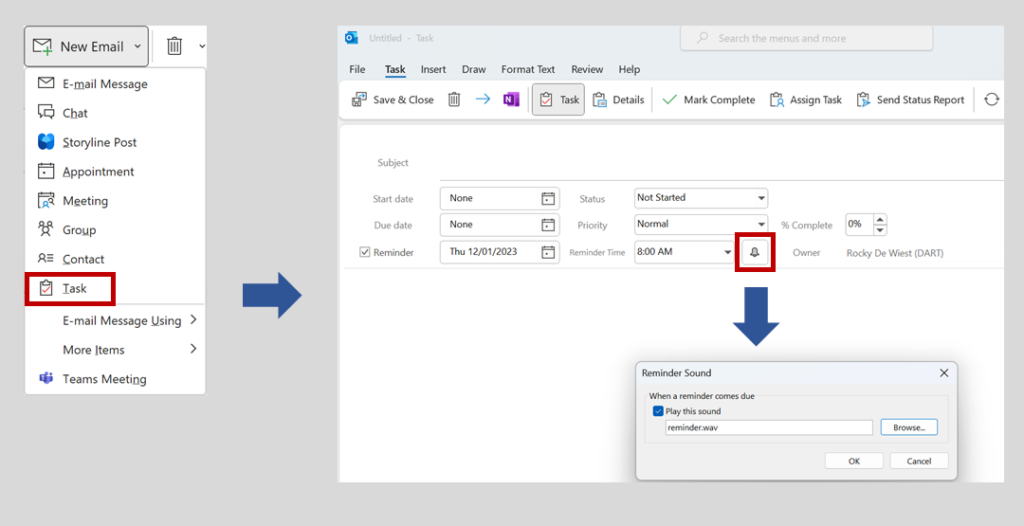
This guide provides steps organizations can take to assess whether users have been targeted or compromised by threat actors exploiting CVE-2023-23397. A successful exploit of this vulnerability can result in unauthorized access to an organization’s environment by triggering a Net-NTLMv2 hash leak. Understanding the vulnerability and how it[…]
Read More
Small and medium-sized businesses are at the heart of our economy and are dedicated to driving value for their customers, whether that means trying new recipes, exploring new inventory, expanding services, arranging the shop so it’s easier to navigate, or keeping the shelves stocked with the products customers[…]
Read More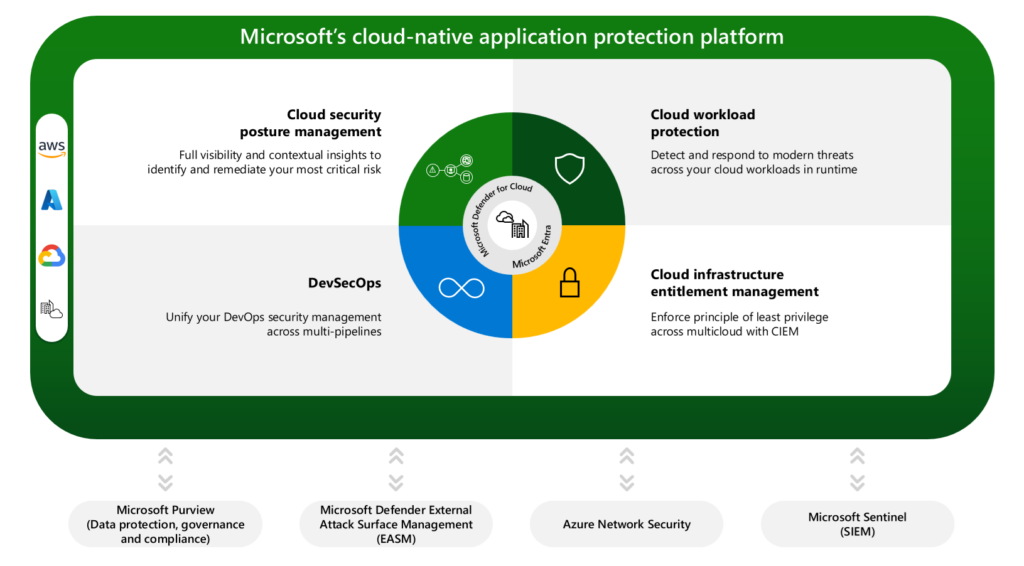
With digital transformation in the face of macroeconomic pressures, strategies to optimize both cloud environments and cloud security are increasingly appealing to enterprises. Organizations worry about vulnerabilities in code getting deployed, critical misconfigurations, overprivileged access to cloud infrastructure, and evolving threats that can cause sensitive data loss. Unfortunately,[…]
Read More
Businesses today are constantly facing new and bigger challenges. Technology is diversifying and evolving faster than ever to address these issues, giving industries across the board a growing number of solutions to sift through. While managing these fast-paced changes and innovations, you also need to engage your customers[…]
Read More