Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026

We are excited to announce that the new Microsoft Purview Data Governance solution will be generally available beginning September 1, 2024. This experience is designed to help today’s data leaders solve their key governance and security challenges in an AI-powered, business-friendly, and unified solution. Since the service launch[…]
Read MoreSome IT teams seem like they’re constantly stuck in never-ending loops of repetitive tasks. Day in, day out, they tackle the same problems, sometimes pushing more strategic work to the backburner to focus on the IT fire of the moment. It’s hard for a CIO to watch, especially[…]
Read More
We’re announcing new capabilities to help accelerate your transition to a Zero Trust security model with the general availability of the Microsoft Entra Suite, the industry’s most comprehensive secure access solution for the workforce, and the general availability of Microsoft Sentinel within the Microsoft unified security operations platform,[…]
Read More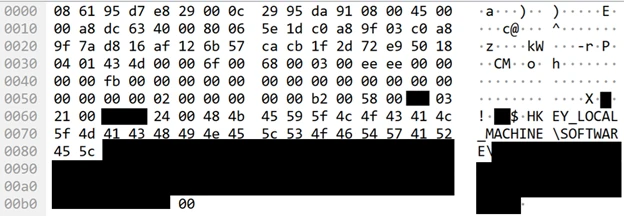
Microsoft discovered and responsibly disclosed two vulnerabilities in Rockwell Automation PanelView Plus that could be remotely exploited by unauthenticated attackers, allowing them to perform remote code execution (RCE) and denial-of-service (DoS). The RCE vulnerability in PanelView Plus involves two custom classes that can be abused to upload and[…]
Read More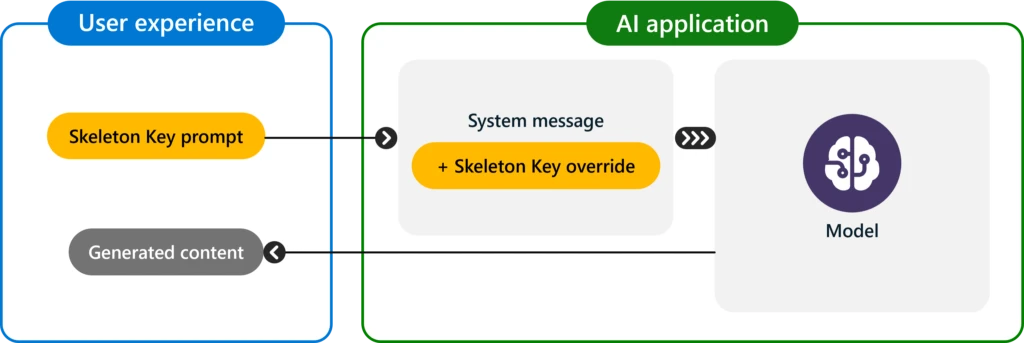
In generative AI, jailbreaks, also known as direct prompt injection attacks, are malicious user inputs that attempt to circumvent an AI model’s intended behavior. A successful jailbreak has potential to subvert all or most responsible AI (RAI) guardrails built into the model through its training by the AI[…]
Read More
I serve on the board of a publicly traded company. I fostered the creation of the board’s cybersecurity committee and I co-lead it. I’ve reflected on my work as a Global Black Belt, an advisor to chief information security officers (CISOs) and IT security and compliance teams, and[…]
Read More
Innovative organizations worldwide harness Microsoft Power Platform to revolutionize operations and achieve exceptional outcomes. Our customer stories underscore the significant impact of this technology across diverse industries, highlighting its role in fostering creativity and efficiency. We’re thrilled to showcase new success stories that illustrate the transformative power of[…]
Read More
Cyberthreats are evolving with alarming sophistication, making it crucial for organizations to react swiftly to incidents and prepare for potential threats. Preparing your organization’s incident response readiness falls broadly into three categories: the process, the people, and the technologies. Often with cybersecurity, more focus is on the technology[…]
Read More
Microsoft Defender Experts for XDR demonstrated excellent managed extended detection and response (MXDR) by unifying our human-driven services and Microsoft Defender XDR in the MITRE Engenuity ATT&CK® Evaluations: Managed Services menuPass + ALPHV BlackCat. Defender Experts for XDR offers a range of capabilities: Managed detection and response: Let[…]
Read More
Explore how effective incident response helps organizations detect, address, and stop cyberattacks Learn more As part of any robust incident response plan, organizations often work through potential security weaknesses by responding to hypothetical cyberthreats. In this blog post, we’ll imagine a scenario in which a threat actor uses[…]
Read More