Notizie per Categorie
Articoli Recenti
- New whitepaper outlines the taxonomy of failure modes in AI agents 24 Aprile 2025
- Understanding the threat landscape for Kubernetes and containerized assets 23 Aprile 2025
- [Launched] Generally Available: Instance Mix for Virtual Machine Scale Sets 22 Aprile 2025
- Microsoft’s AI vision shines at MWC 2025 in Barcelona 22 Aprile 2025
- [Launched] Generally Available: Announcing the Next generation Azure Data Box Devices 22 Aprile 2025
- [Launched] Generally Available: Cross-Region Data Transfer Capability in Azure Data Box Devices 21 Aprile 2025
- [Launched] Generally Available: Azure Ultra Disk Storage is now available in Spain Central 21 Aprile 2025
- [Launched] Generally Available: Azure Firewall resource specific log tables get Azure Monitor Basic plan support 21 Aprile 2025
- Hannover Messe 2025: Microsoft puts industrial AI to work 21 Aprile 2025
- Securing our future: April 2025 progress report on Microsoft’s Secure Future Initiative 21 Aprile 2025
On July 18, 2023, we published the 2023 release wave 2 plans for Microsoft Dynamics 365 and Microsoft Power Platform, a compilation of new capabilities planned to be released between October 2023 and March 2024. This second release wave of the year offers hundreds of new features, including AI capabilities and enhancements, demonstrating[…]
Read More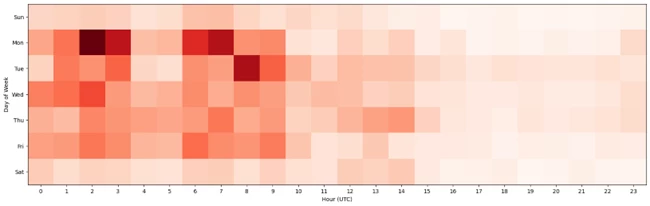
Executive summary On July 11, 2023, Microsoft published two blogs detailing a malicious campaign by a threat actor tracked as Storm-0558 that targeted customer email that we’ve detected and mitigated: Microsoft Security Response Center and Microsoft on the Issues. As we continue our investigation into this incident and deploy[…]
Read More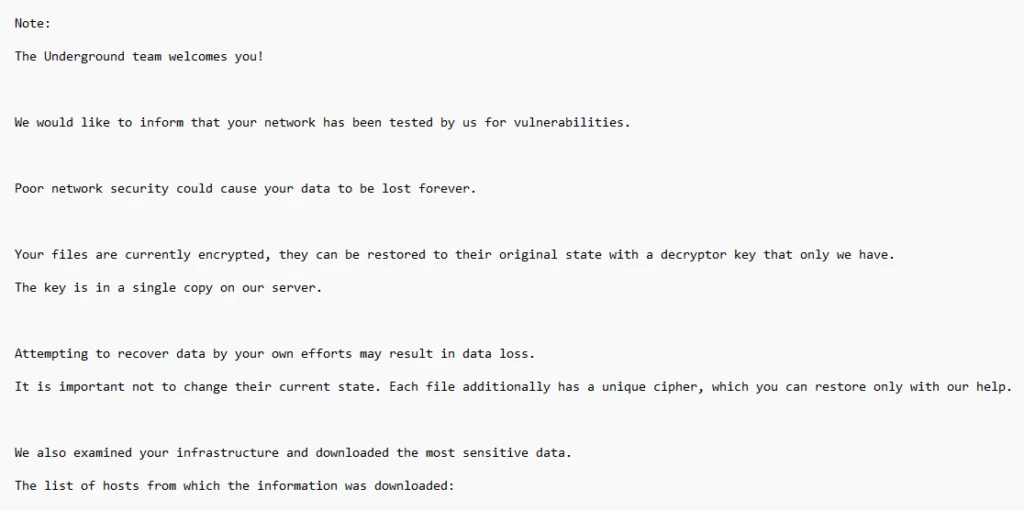
Microsoft has identified a phishing campaign conducted by the threat actor tracked as Storm-0978 targeting defense and government entities in Europe and North America. The campaign involved the abuse of CVE-2023-36884, which included a remote code execution vulnerability exploited before disclosure to Microsoft via Word documents, using lures[…]
Read More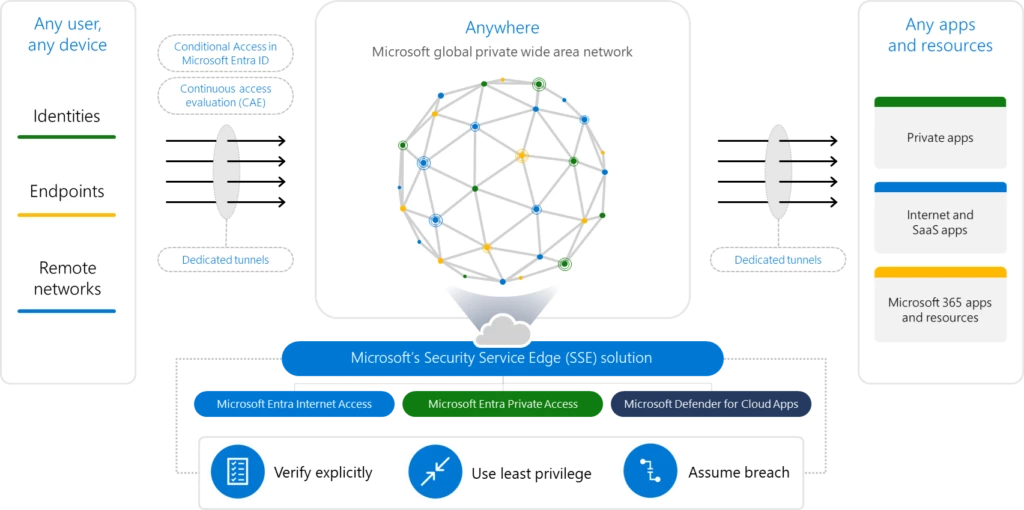
A year ago when we announced the Microsoft Entra product family, we asked what the world could achieve if we had trust in every digital experience and interaction.1 This question inspired us to offer a vision for securing the millions and millions of connections that happen every second[…]
Read More
We know customers of every size face ever-increasing security risks. In just the last 12 months the speed of attackers leveraging breaches is also increasing, as it only takes 72 minutes on average for an attacker to access private data from the time a user falls victim to[…]
Read More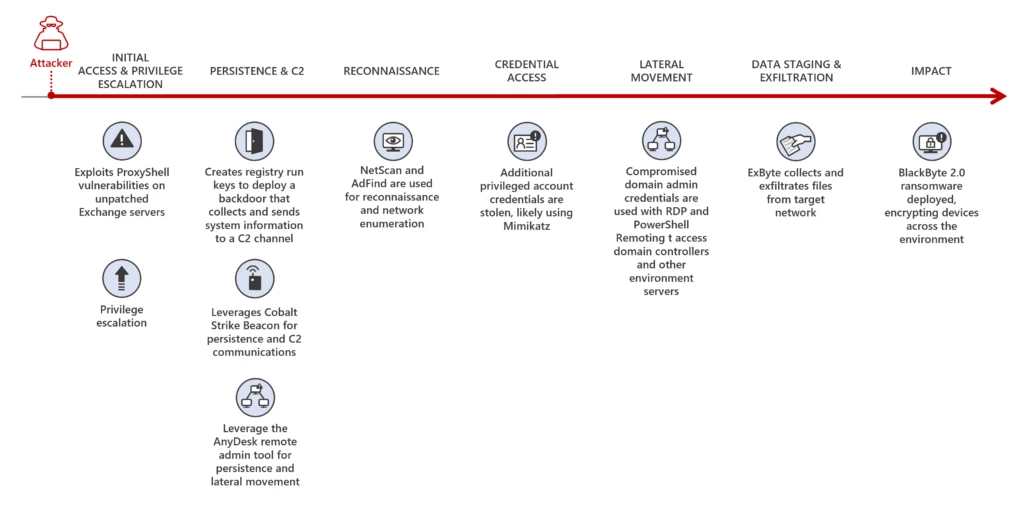
As ransomware attacks continue to grow in number and sophistication, threat actors can quickly impact business operations if organizations are not well prepared. In a recent investigation by Microsoft Incident Response (previously known as Microsoft Detection and Response Team – DART) of an intrusion, we found that the[…]
Read More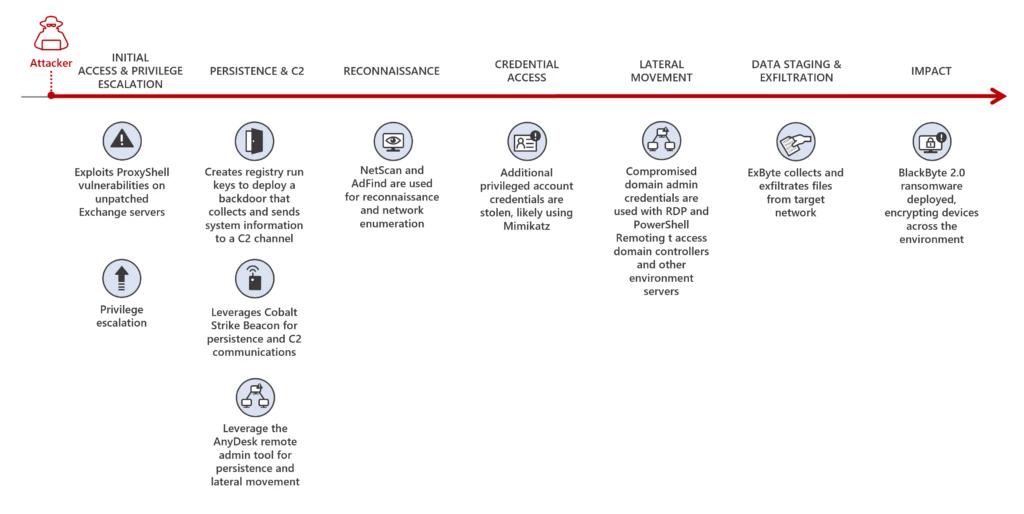
As ransomware attacks continue to grow in number and sophistication, threat actors can quickly impact business operations if organizations are not well prepared. In a recent investigation by Microsoft Incident Response (previously known as Microsoft Detection and Response Team – DART) of an intrusion, we found that the[…]
Read More
Microsoft security researchers tracked a 130.4 percent increase in organizations that have encountered ransomware over the last year. Endpoints are an important attack vector and ensuring that organizations have modern endpoint security as part of a broader extended detection and response strategy, is top of mind for chief[…]
Read More
Microsoft security researchers tracked a 130.4 percent increase in organizations that have encountered ransomware over the last year. Endpoints are an important attack vector and ensuring that organizations have modern endpoint security as part of a broader extended detection and response strategy, is top of mind for chief[…]
Read More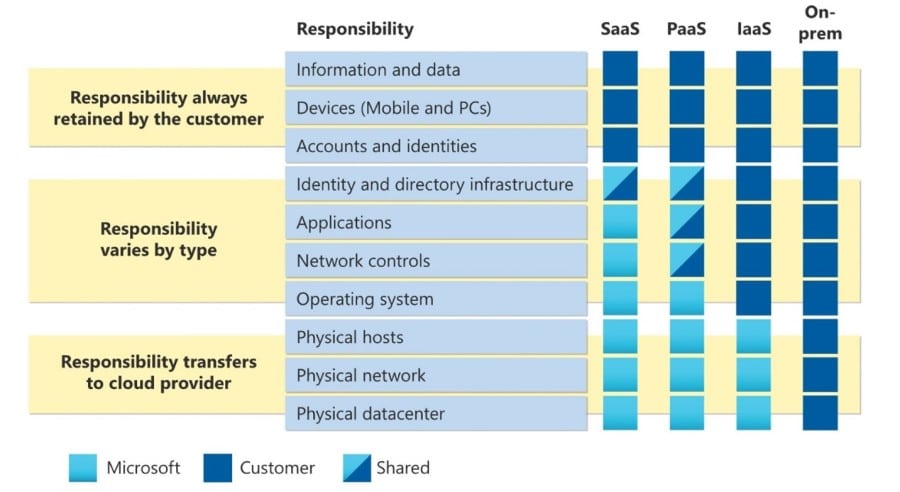
In today’s digital age, cloud computing has become an essential part of businesses, enabling them to store and access their data from anywhere. However, with convenience comes the risk of data breaches and cyberattacks. Therefore, it is crucial to implement best practices to secure data in cloud services.[…]
Read More