Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
- [In preview] Private Preview: DCesv6 and ECesv6 series confidential VMs with Intel® TDX 17 Aprile 2025
- [Launched] Generally Available: ExpressRoute Metro Peering locations and Global Reach are now available in more regions 17 Aprile 2025
- [Launched] Generally Available: Azure Front Door custom cipher suite 17 Aprile 2025
- Microsoft’s Secure by Design journey: One year of success 17 Aprile 2025
- [In development] Private Preview: Azure Backup for AKS Now Supports Azure File Share-based Persistent Volumes 16 Aprile 2025
- [In preview] Public Preview: Remote Model Context Protocol (MCP) support in Azure Functions 16 Aprile 2025

Welcome to the second Microsoft Power Platform Conference! Since the first conference, there has been a seismic shift in how we build low-code solutions. With Power Platform Copilot, we are now in the era of AI-assisted low-code development. As such, this year’s conference is focused on helping the[…]
Read More
This year marks the twentieth anniversary of Cybersecurity Awareness Month, when we partner with the National Cybersecurity Alliance, the United States Cybersecurity and Infrastructure Security Agency (CISA), and organizations around the world to amplify the importance of cybersecurity best practices and how to be cybersmart. Initially, this moment[…]
Read More
During the past few years, we’ve managed a lot of change and disruption in our security work, in our lives, and in society at large. This year we’re excited to welcome back security leaders, aspiring leaders, and IT professionals—in person—to Microsoft Ignite from November 14 to 17, 2023,[…]
Read More
While attacks are getting more sophisticated, so are our defenses. With recent innovations like secured-core PCs that are 60 percent more resilient to malware than non-secured-core PCs,1 and the Microsoft Pluton Security Processor that adds more protection by isolating sensitive data like credentials and encryption keys, Windows 11[…]
Read MoreToday marks an exciting milestone in Microsoft’s AI journey. This morning, at an event in New York City, we made several major announcements to empower people across work and life—you can read more about Microsoft Bing and Edge with Copilot, what’s new from Microsoft 365 Copilot and Bing[…]
Read More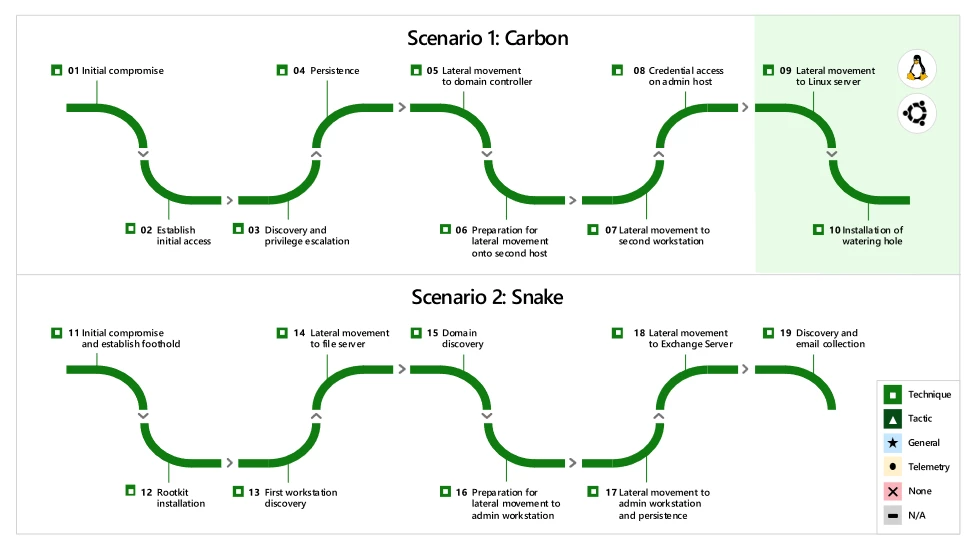
For the fifth consecutive year, Microsoft 365 Defender demonstrated industry-leading extended detection and response (XDR) capabilities in the independent MITRE Engenuity ATT&CK® Evaluations: Enterprise. The attack used during the test highlights the importance of a unified XDR platform and showcases Microsoft 365 Defender as a leading solution, enabled[…]
Read More
Microsoft is proud to be recognized as a Leader in the Forrester Wave™: Zero Trust Platform Providers, Q3 2023 report. At Microsoft, we understand modernizing security is a complex task in this era of ever-evolving cyberthreats and complex digital environments. Serious threats have necessitated a paradigm shift in[…]
Read More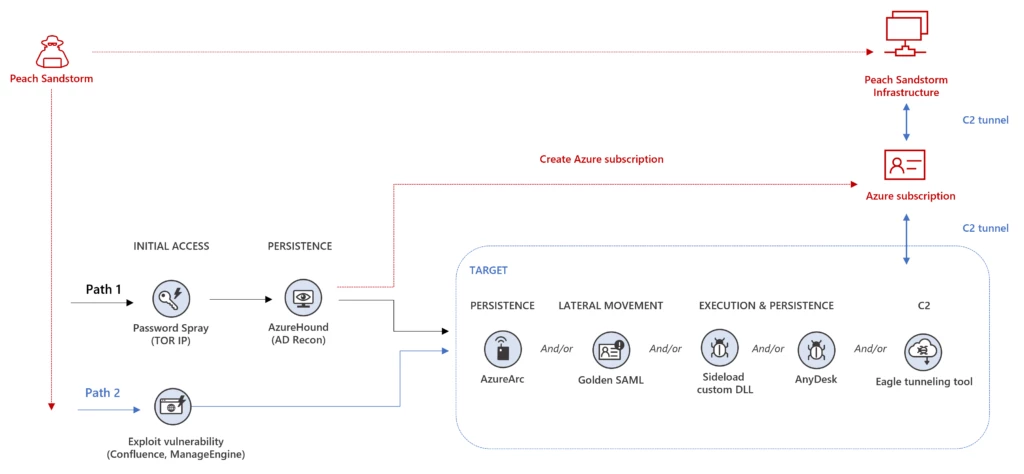
Since February 2023, Microsoft has observed password spray activity against thousands of organizations carried out by an actor we track as Peach Sandstorm (HOLMIUM). Peach Sandstorm is an Iranian nation-state threat actor who has recently pursued organizations in the satellite, defense, and pharmaceutical sectors around the globe. Based[…]
Read More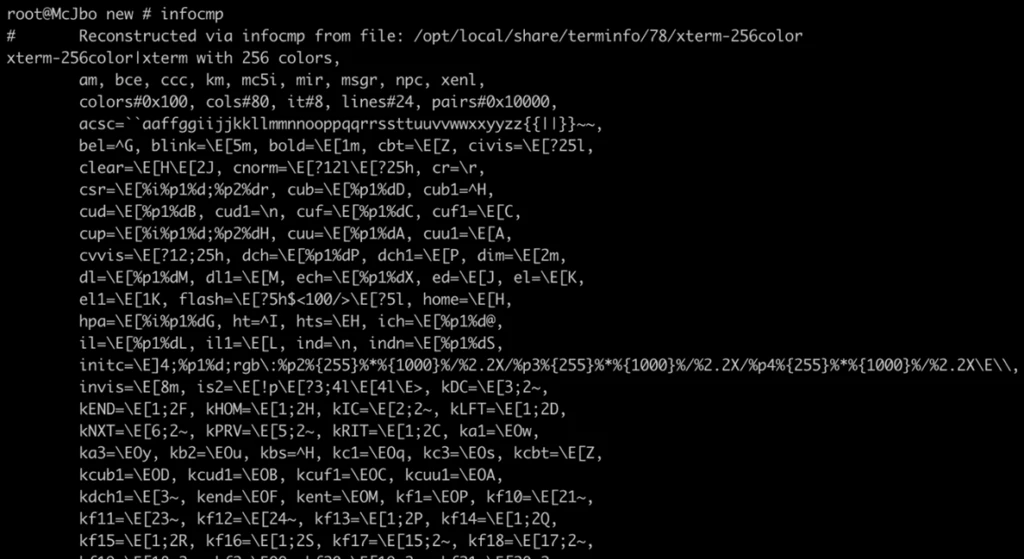
Microsoft has discovered a set of memory corruption vulnerabilities in a library called ncurses, which provides APIs that support text-based user interfaces (TUI). Released in 1993, the ncurses library is commonly used by various programs on Portable Operating System Interface (POSIX) operating systems, including Linux, macOS, and FreeBSD.[…]
Read More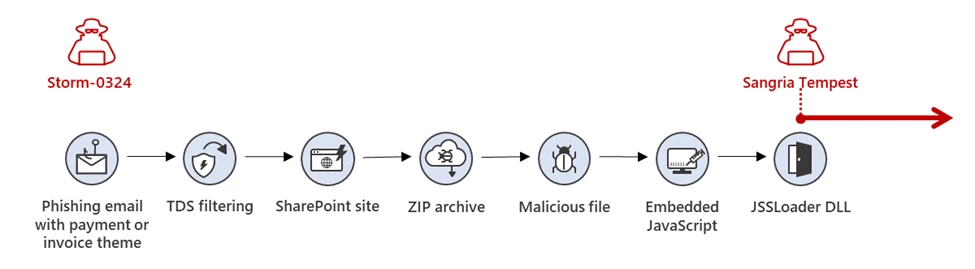
The threat actor that Microsoft tracks as Storm-0324 is a financially motivated group known to gain initial access using email-based initial infection vectors and then hand off access to compromised networks to other threat actors. These handoffs frequently lead to ransomware deployment. Beginning in July 2023, Storm-0324 was[…]
Read More