Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
- [In preview] Private Preview: DCesv6 and ECesv6 series confidential VMs with Intel® TDX 17 Aprile 2025
- [Launched] Generally Available: ExpressRoute Metro Peering locations and Global Reach are now available in more regions 17 Aprile 2025
- [Launched] Generally Available: Azure Front Door custom cipher suite 17 Aprile 2025
- Microsoft’s Secure by Design journey: One year of success 17 Aprile 2025
- [In development] Private Preview: Azure Backup for AKS Now Supports Azure File Share-based Persistent Volumes 16 Aprile 2025
- [In preview] Public Preview: Remote Model Context Protocol (MCP) support in Azure Functions 16 Aprile 2025
Microsoft Power Platform developer tools are enabling professional developers to create more effective business solutions using Power Platform than ever before. Development is faster, applications are more secure, and deployed within managed environments that have guardrails applying organizational policies and promoting best practices. You can quickly: Create low-code[…]
Read More
Our story begins with a customer whose help desk unwittingly assisted a threat actor posing as a credentialed employee. In this fourth report in our ongoing Cyberattack Series, we look at the steps taken to discover, understand, and respond to a credential phishing and smishing (text-based phishing) cyberattack[…]
Read More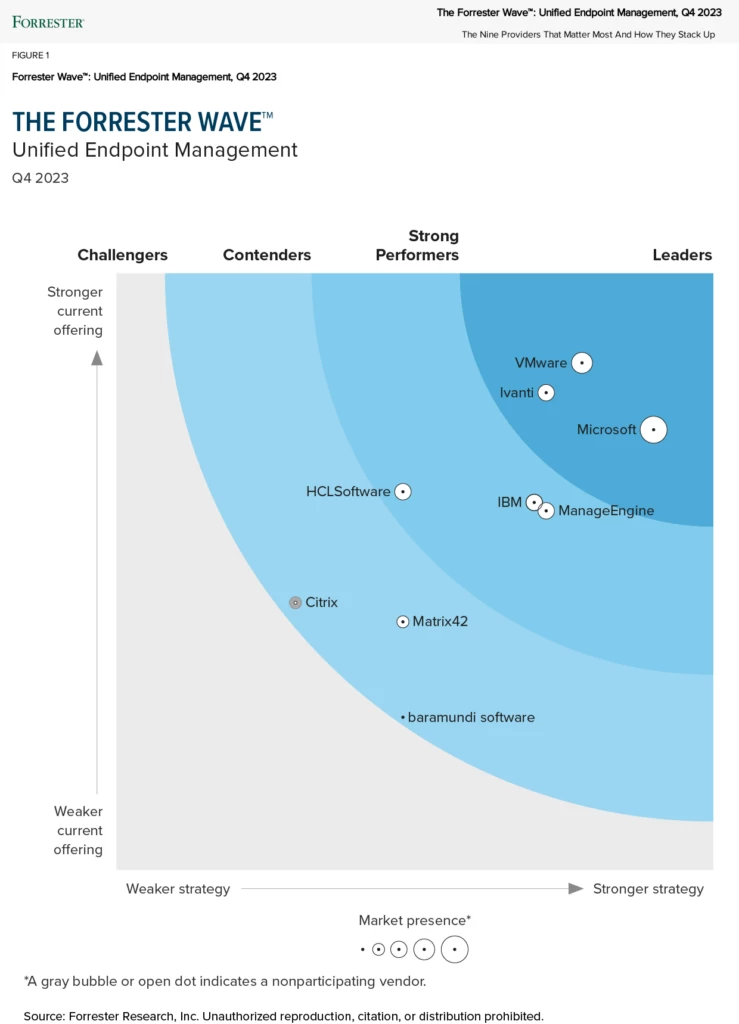
Maintaining a secure and optimized digital environment allows new ideas to flourish wherever they occur. In the modern workplace, where devices and locations are no longer fixed, Microsoft Intune eases the task of managing and protecting the endpoints of businesses everywhere. It helps secure systems and simplify management,[…]
Read MoreMicrosoft warmly invites you to join us in Orlando for the DEVIntersection Conference and the Microsoft Azure + AI Conference. You’ll hear from some of your favorite Microsoft leaders, including Scott Hanselman, Vice President of Microsoft Development Community, and Scott Hunter, Vice President Director of Product at Microsoft on the[…]
Read More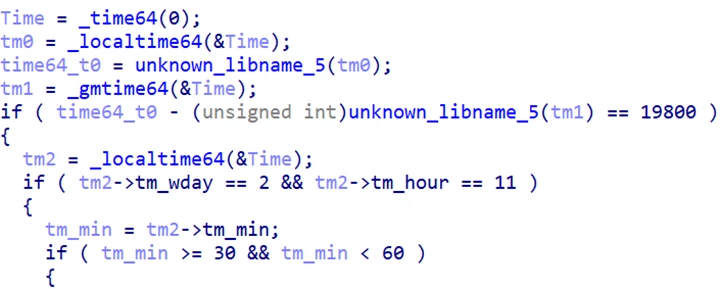
Microsoft Threat Intelligence has uncovered a supply chain attack by the North Korea-based threat actor Diamond Sleet (ZINC) involving a malicious variant of an application developed by CyberLink Corp., a software company that develops multimedia software products. This malicious file is a legitimate CyberLink application installer that has[…]
Read More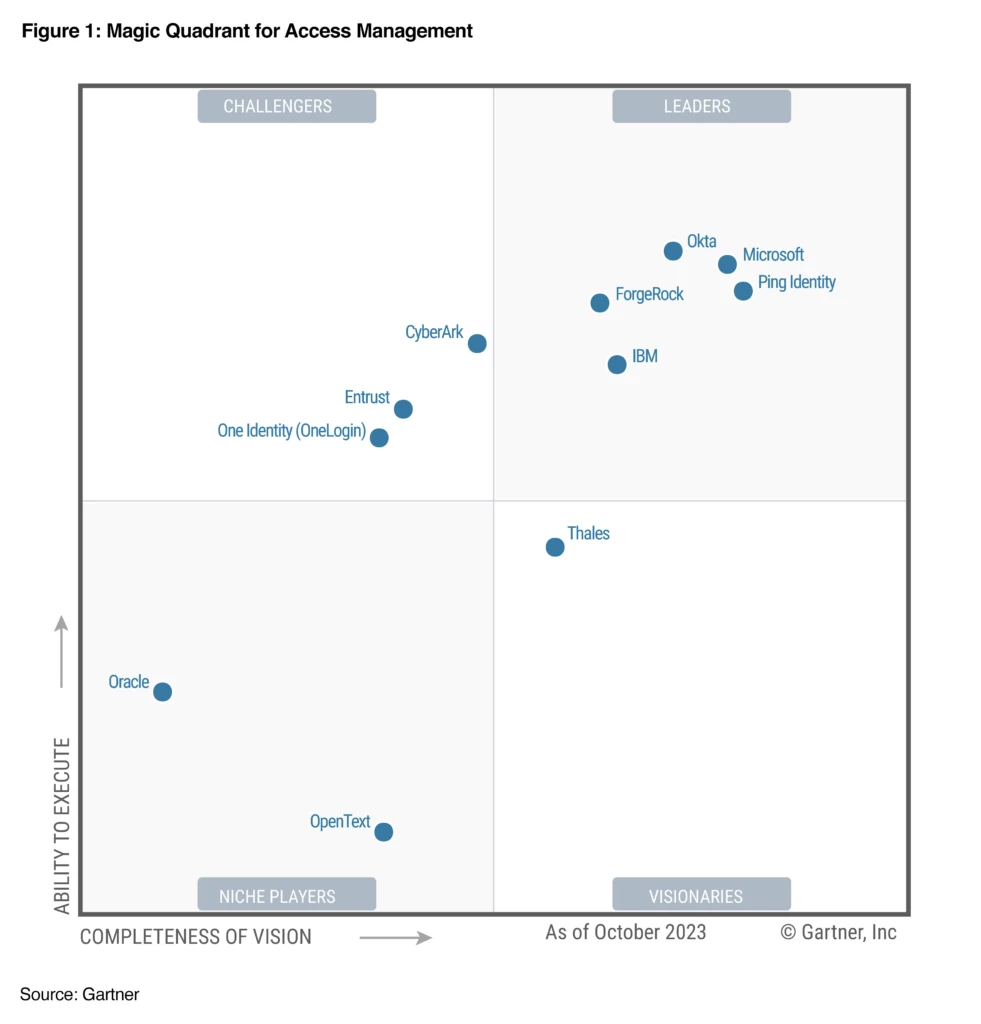
Protecting identity from compromise is top of mind for security professionals as identity attacks continue to intensify. Earlier this year we reported that we had observed a nearly three-fold increase in password attacks per second in the last two years, from 579 in 2021 to 4,000 in 2023.1[…]
Read More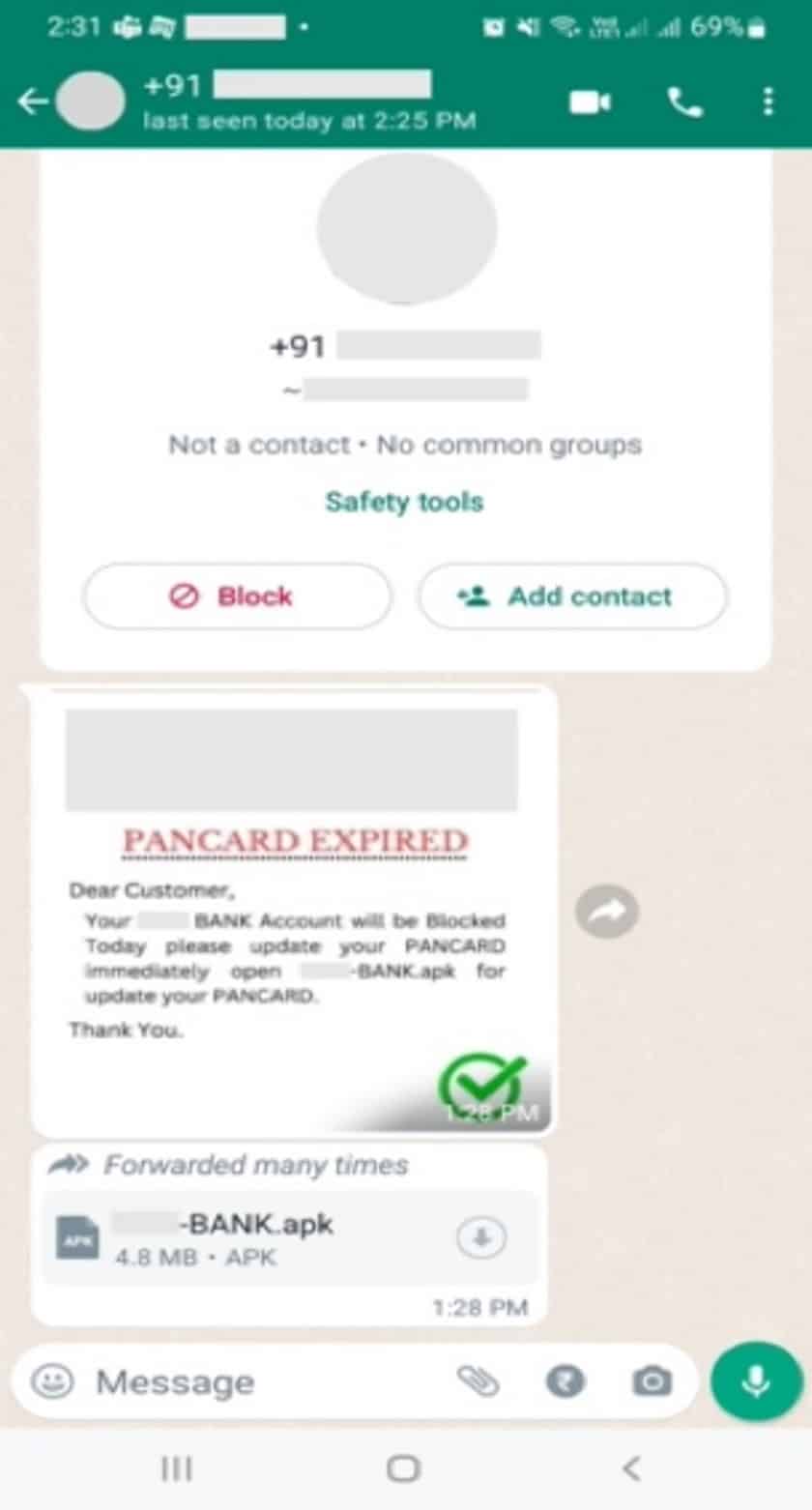
Microsoft has observed ongoing activity from mobile banking trojan campaigns targeting users in India with social media messages designed to steal users’ information for financial fraud. Using social media platforms like WhatsApp and Telegram, attackers are sending messages designed to lure users into installing a malicious app on[…]
Read More
The future of security with AI The increasing speed, scale, and sophistication of recent cyberattacks demand a new approach to security. Traditional tools are no longer enough to keep pace with the threats posed by cybercriminals. In just two years, the number of password attacks detected by Microsoft[…]
Read More
In the ever-evolving landscape of AI, Microsoft Power Platform has the unique opportunity to unlock the vast potential of business application data and logic. Every fragment of enterprise data carries latent insights and untapped productivity. At Microsoft Ignite 2023, witness firsthand how Microsoft Power Platform and Microsoft Dataverse[…]
Read MoreAt the CYBERWARCON 2023 conference, Microsoft and LinkedIn analysts are presenting several sessions detailing analysis across multiple sets of threat actors and related activity. This blog is intended to summarize the content of the research covered in these presentations and demonstrates Microsoft Threat Intelligence’s ongoing efforts to track[…]
Read More