Notizie per Categorie
Articoli Recenti
- Retirement: Canonical Ubuntu 20.04 LTS Reaching End of Standard Support on May 31, 2025 9 Aprile 2025
- Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI 9 Aprile 2025
- [In preview] Public Preview: Power BI Connector for vCore-based Azure Cosmos DB for MongoDB 9 Aprile 2025
- [In preview] Public Preview: Fabric Mirroring for Azure Database for PostgreSQL – flexible server 9 Aprile 2025
- [Launched] Generally Available: Azure SQL Updates for Early-April 2025 9 Aprile 2025
- [Launched] Generally Available: I/O Performance Analysis—SQL Server on Azure Virtual Machines 9 Aprile 2025
- [In preview] Public Preview: Self-serve enablement for all versions and deletes mode in Azure Cosmos DB for NoSQL 9 Aprile 2025
- How cyberattackers exploit domain controllers using ransomware 9 Aprile 2025
- [In preview] Public Preview: New Enhancements to Carbon Optimization – Expanded API limits, Subscription Reader Access, and Filtering Options 8 Aprile 2025
- Exploitation of CLFS zero-day leads to ransomware activity 8 Aprile 2025
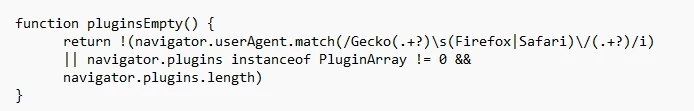
Microsoft Threat Intelligence continues to track and disrupt malicious activity attributed to a Russian state-sponsored actor we track as Star Blizzard (formerly SEABORGIUM, also known as COLDRIVER and Callisto Group). Star Blizzard has improved their detection evasion capabilities since 2022 while remaining focused on email credential theft against[…]
Read More
First announced in March 2023, Microsoft Security Copilot—Microsoft’s first generative AI security product—has sparked major interest. The widespread enthusiasm was on full display after announcing our Early Access Program in October 2023 and sharing our incredible Security Copilot innovations at Microsoft Ignite in November 2023. With the rapid[…]
Read More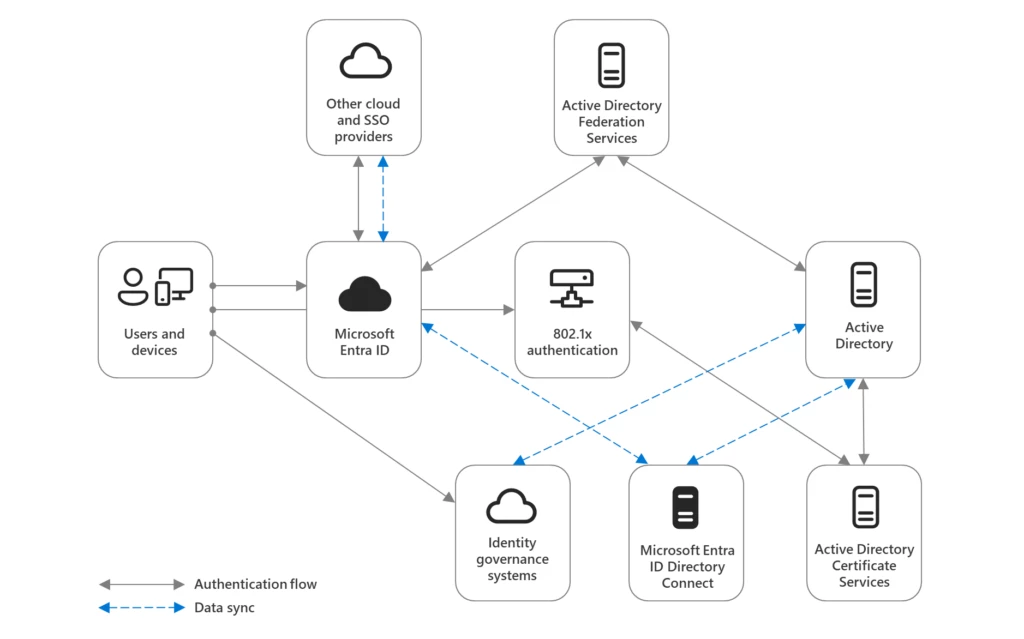
Microsoft observed a surge in cyberattacks targeting identities in 2023, with attempted password-based attacks increasing by more than tenfold in the first quarter of 2023 compared to the same period in 2022. Threat actors leverage compromised identities to achieve a significant level of access to target networks. The[…]
Read MoreThe post 3 reasons why now is the time to go cloud native for device management appeared first on Microsoft Security Blog. Source: Microsoft Security
Read MoreMicrosoft Power Platform developer tools are enabling professional developers to create more effective business solutions using Power Platform than ever before. Development is faster, applications are more secure, and deployed within managed environments that have guardrails applying organizational policies and promoting best practices. You can quickly: Create low-code[…]
Read More
Our story begins with a customer whose help desk unwittingly assisted a threat actor posing as a credentialed employee. In this fourth report in our ongoing Cyberattack Series, we look at the steps taken to discover, understand, and respond to a credential phishing and smishing (text-based phishing) cyberattack[…]
Read More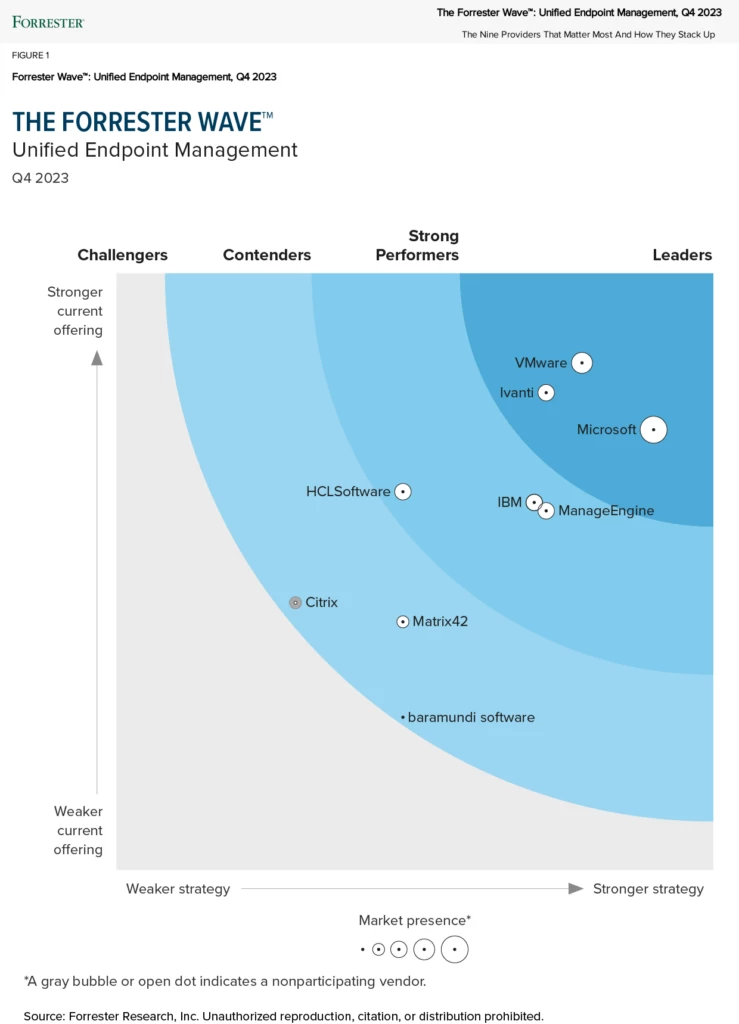
Maintaining a secure and optimized digital environment allows new ideas to flourish wherever they occur. In the modern workplace, where devices and locations are no longer fixed, Microsoft Intune eases the task of managing and protecting the endpoints of businesses everywhere. It helps secure systems and simplify management,[…]
Read MoreMicrosoft warmly invites you to join us in Orlando for the DEVIntersection Conference and the Microsoft Azure + AI Conference. You’ll hear from some of your favorite Microsoft leaders, including Scott Hanselman, Vice President of Microsoft Development Community, and Scott Hunter, Vice President Director of Product at Microsoft on the[…]
Read More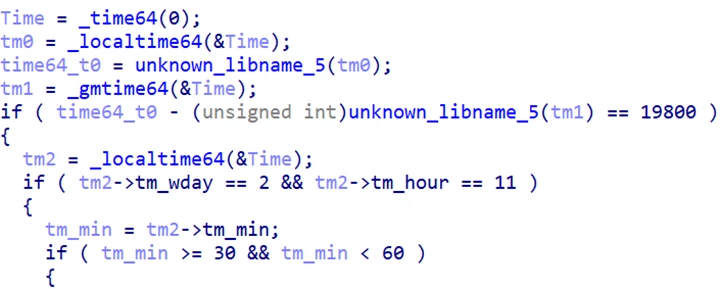
Microsoft Threat Intelligence has uncovered a supply chain attack by the North Korea-based threat actor Diamond Sleet (ZINC) involving a malicious variant of an application developed by CyberLink Corp., a software company that develops multimedia software products. This malicious file is a legitimate CyberLink application installer that has[…]
Read More
Protecting identity from compromise is top of mind for security professionals as identity attacks continue to intensify. Earlier this year we reported that we had observed a nearly three-fold increase in password attacks per second in the last two years, from 579 in 2021 to 4,000 in 2023.1[…]
Read More